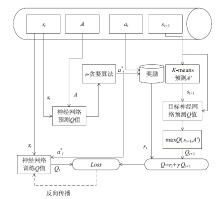
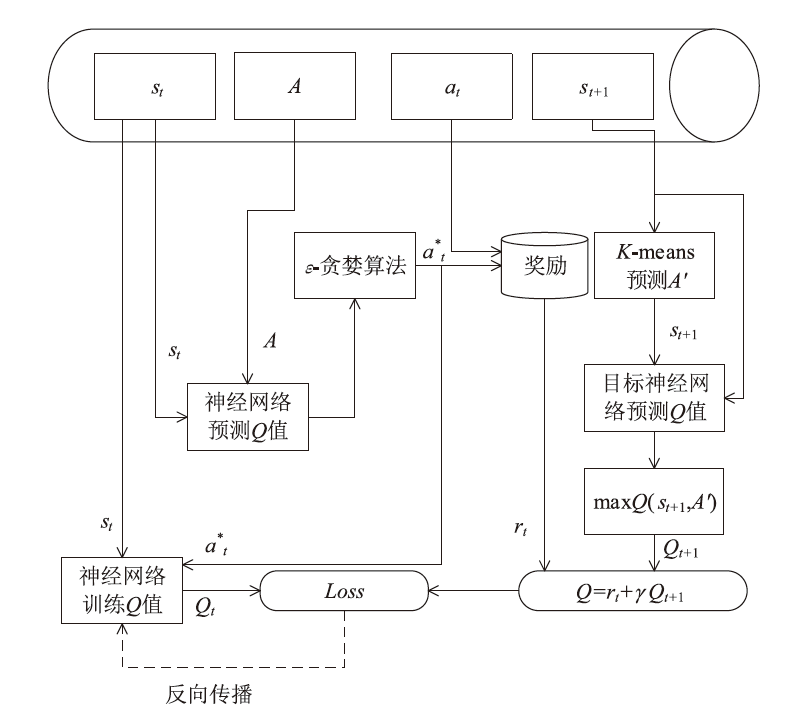
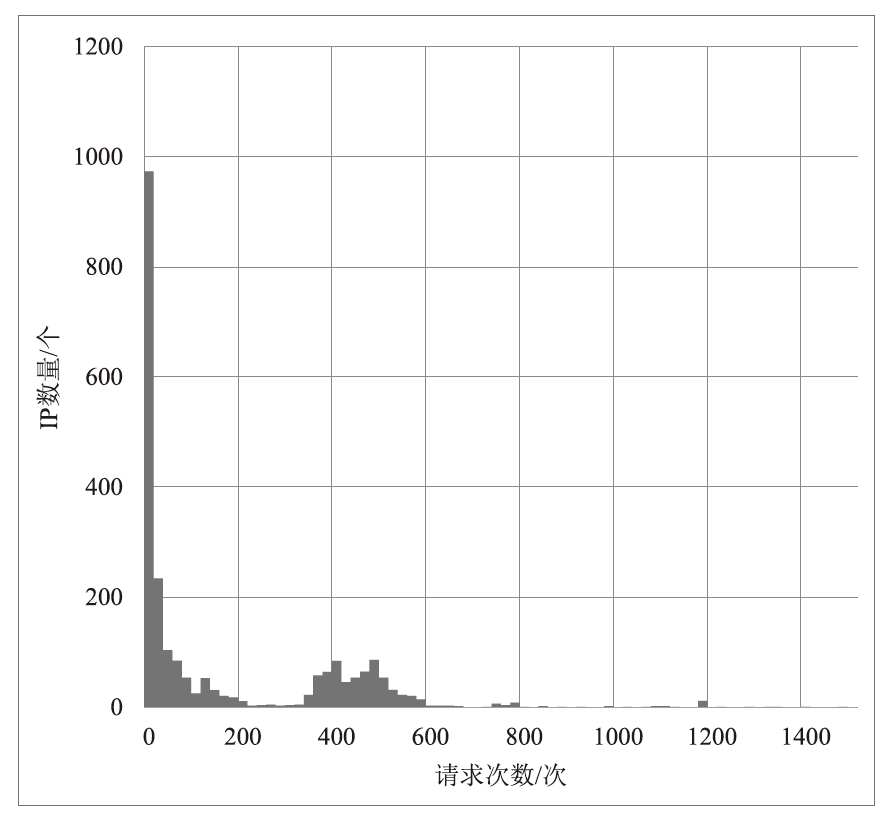
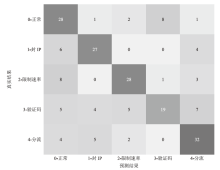
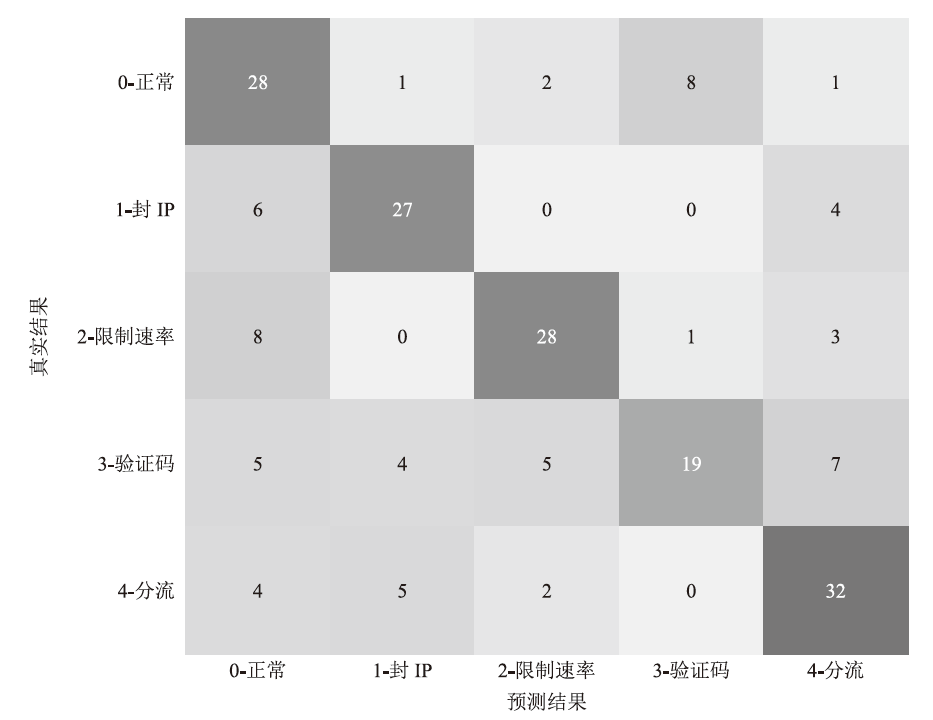
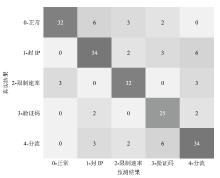
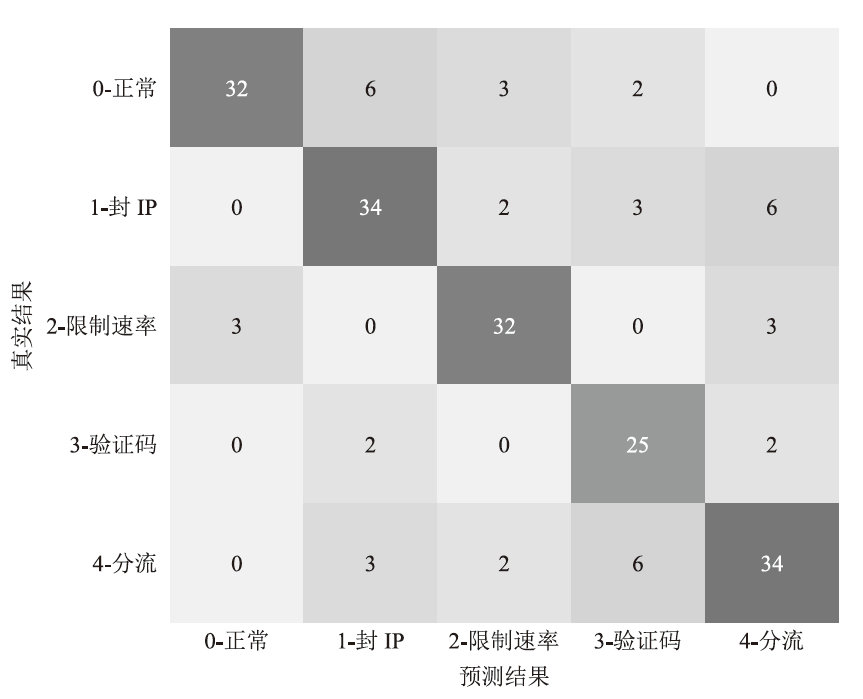
Netinfo Security ›› 2024, Vol. 24 ›› Issue (9): 1458-1469.doi: 10.3969/j.issn.1671-1122.2024.09.013
Previous Articles Next Articles
Anomaly Traffic Identification and Defense Model in Networks Based on the Multi-Gate Mixture of Experts
GUO Yongjin1,2, HUANG Hejun1,2( )
)
- 1. Shanghai Open University, Shanghai 200433, China
2. Shanghai Education Software Development Company, Shanghai 200082, China
-
Received:2024-06-02Online:2024-09-10Published:2024-09-27
CLC Number:
Cite this article
GUO Yongjin, HUANG Hejun. Anomaly Traffic Identification and Defense Model in Networks Based on the Multi-Gate Mixture of Experts[J]. Netinfo Security, 2024, 24(9): 1458-1469.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.09.013
| 特征 | 含义 |
|---|---|
| ip_ua_unique_path_cnt_w | 窗口内相同IP、UA(User-Agent)的情况下path的去重数量 |
| ip_unique_ua_cnt_w | 窗口内相同IP情况下遍历不同UA的去重数量 |
| ip_cnt_w | 窗口内IP数量 |
| url_cnt_w | 窗口内URL数量 |
| ip_ua_cnt_w | 窗口内IP和UA的组合数量 |
| ip_url_cnt_w | 窗口内IP和URL的组合数量 |
| ip_ua_url_cnt_w | 窗口内IP、UA和URL的组合数量 |
| url_unique_ip_cnt_w | 窗口内同一URL下IP的去重数量 |
| ip_34xx_cnt_w | 窗口内同一IP下状态码为401/403/404的数量 |
| ip_url_unique_ua_cnt_w | 窗口内同一IP和URL下UA的去重数量 |
| ip_req_mean_w | 窗口内同一IP下请求包大小均值 |
| [1] | PRICE-WILLIAMS M, HEARD N, RUBIN-DELANCHY P. Detecting Weak Dependence in Computer Network Traffic Patterns by Using Higher Criticism[J]. Journal of the Royal Statistical Society Series C, 2019, 68(3): 641-655. |
| [2] | WAN Jiafu, CHEN Baotong, IMRAN M, et al. Toward Dynamic Resources Management for IoT-Based Manufacturing[J]. IEEE Communications Magazine, 2018, 56(2): 52-59. |
| [3] | TIAN Zhihong, SHI Wei, WANG Yuhang, et al. Real-Time Lateral Movement Detection Based on Evidence Reasoning Network for Edge Computing Environment[J]. IEEE Transactions on Industrial Informatics, 2019, 15(7): 4285-4294. |
| [4] | VAN HASSELT H, GUEZ A, SILVER D. Deep Reinforcement Learning with Double Q-Learning[EB/OL]. (2015-12-08)[2024-05-11]. http://arxiv.org/abs/1509.06461v3. |
| [5] | CHOI H, KIM M, LEE G, et al. Unsupervised Learning Approach for Network Intrusion Detection System Using Autoencoders[J]. The Journal of Supercomputing, 2019, 75(9): 5597-5621. |
| [6] | AHMED M, SERAJ R, ISLAM S M S. The k-Means Algorithm: A Comprehensive Survey and Performance Evaluation[EB/OL]. (2020-08-07)[2024-05-11]. https://doi.org/10.3390/electronics9081295. |
| [7] | HAUSKNECHT M, STONE P, RAMANI D. Deep Recurrent Q-Learning for Partially Observable MDPS[EB/OL]. [2024-05-11]. https://arxiv.org/abs/1507.06527v4. |
| [8] | WANG Ke, STOLFO S J. Anomalous Payload-Based Network Intrusion Detection[EB/OL]. [2024-05-11]. https://wenku.baidu.com/view/8b5063a2284ac850ad02429f.html?fr=xueshu&_wkts_=1724600629659&needWelcomeRecommand=1. |
| [9] | KIM M S, KONG H J, HONG S C, et al. A Flow-Based Method for Abnormal Network Traffic Detection[C]// IEEE. 2004 IEEE/IFIP Network Operations and Management Symposium. New York: IEEE, 2004: 599-612. |
| [10] | QIAO Yiguo, XIN Xuezhu, BIN Yu, et al. Anomaly Intrusion Detection Method Based on HMM[J]. Electronics Letters, 2002, 38(13): 663-664. |
| [11] | LEI Yang. Network Anomaly Traffic Detection Algorithm Based on SVM[C]// IEEE. 2017 International Conference on Robots & Intelligent System (ICRIS). New York: IEEE, 2017: 217-220. |
| [12] | KONG Lingjing, HUANG Guowei, WU Keke. Identification of Abnormal Network Traffic Using Support Vector Machine[C]// IEEE. 2017 18th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT). New York: IEEE, 2017: 288-292. |
| [13] | JIANG Wei, FANG Binxing, TIAN Zhihong, et al. Research on Defense Strategies Selection Based on Attack-Defense Stochastic Game Model[J]. Journal of Computer Research & Development, 2010, 47(10): 1714-1723. |
| [14] | WEI Longfei, SARWAT A I, SAAD W, et al. Stochastic Games for Power Grid Protection against Coordinated Cyber-Physical Attacks[J]. IEEE Transactions on Smart Grid, 2018, 9(2): 684-694. |
| [15] | WATKINS C, DAYAN P. Q-Learning[J]. Machine Learning, 1992, 8(3-4): 279-292. |
| [16] | NGUYEN T T, REDDI V J. Deep Reinforcement Learning for Cyber Security[J]. IEEE Transactions on Neural Networks and Learning Systems, 2023, 34(8): 3779-3795. |
| [17] | EGHTESAD T, VOROBEYCHIK Y, LASZKA A. Adversarial Deep Reinforcement Learning Based Adaptive Moving Target Defense[C]// Srpinger. International Conference on Decision and Game Theory for Security. Heidelberg: Springer, 2020: 58-79. |
| [18] | CASGRAIN P, NING B, JAIMUNGAL S. Deep Q-Learning for Nash Equilibria: Nash-DQN[EB/OL]. [2024-05-11]. https://arxiv.org/abs/1904.10554v2. |
| [19] | SHEN Sheng, HOU Le, ZHOU Yanqi, et al. Mixture-of-Experts Meets Instruction Tuning: A Winning Combination for Large Language Models[EB/OL]. [2024-05-11]. https://arxiv.org/pdf/2305.14705. |
| [20] | SHAZEER N, MIRHOSEINI A, MAZIARZ K, et al. Outrageously Large Neural Networks: The Sparsely-Gated Mixture-of-Experts Layer[EB/OL]. [2024-05-11]. https://arxiv.org/abs/1701.06538v1. |
| [21] | LEPIKHIN D, LEE H, XU Yuanzhong, et al. GShard: Scaling Giant Models with Conditional Computation and Automatic Sharding[EB/OL]. [2024-05-11]. https://arxiv.org/pdf/2006.16668. |
| [1] | LI Jiao, ZHANG Yuqing, WU Yabiao. Data Augmentation Method via Large Language Model for Relation Extraction in Cybersecurity [J]. Netinfo Security, 2024, 24(10): 1477-1483. |
| [2] | WANG Qiang, LIU Yizhi, LI Tao, HE Xiaochuan. Review of Encrypted Network Traffic Anonymity and Systemic Defense Tactics [J]. Netinfo Security, 2024, 24(10): 1484-1492. |
| [3] | SHEN Qintao, LIANG Ruigang, WANG Baolin, ZHANG Jingcheng, CHEN Kai. Vulnerability Causation Analysis Based on Dynamic Execution Logging and Reverse Analysis [J]. Netinfo Security, 2024, 24(10): 1493-1505. |
| [4] | WEI Jinxia, HUANG Xizhang, FU Yuhao, LI Jing, LONG Chun. Mining Traffic Detection Method Based on Global Feature Learning [J]. Netinfo Security, 2024, 24(10): 1506-1514. |
| [5] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [6] | ZHANG Zihan, LAI Qingnan, ZHOU Changling. Survey on Fuzzing Test in Deep Learning Frameworks [J]. Netinfo Security, 2024, 24(10): 1528-1536. |
| [7] | WANG Yaxin, ZHANG Jian. Fingerprint Feature Extraction of Electronic Medical Records Based on Few-Shot Named Entity Recognition Technology [J]. Netinfo Security, 2024, 24(10): 1537-1543. |
| [8] | ZHANG Zhanpeng, WANG Juan, ZHANG Chong, WANG Jie, HU Yuyi. The Research on Efficient Web Fuzzing Technology Based on Graph Isomorphic Network [J]. Netinfo Security, 2024, 24(10): 1544-1552. |
| [9] | SA Qirui, YOU Weijing, ZHANG Yifei, QIU Weiyang, MA Cunqing. A Survey of Ownership Protection Schemes for Federated Learning Models [J]. Netinfo Security, 2024, 24(10): 1553-1561. |
| [10] | CHEN Jing, ZHANG Jian. A Data-Free Personalized Federated Learning Algorithm Based on Knowledge Distillation [J]. Netinfo Security, 2024, 24(10): 1562-1569. |
| [11] | LU Xiaofeng, CHENG Tianze, LONG Chengnian. A Random Walk Based Black-Box Adversarial Attack against Graph Neural Network [J]. Netinfo Security, 2024, 24(10): 1570-1577. |
| [12] | WU Lizhao, WANG Xiaoding, XU Tian, QUE Youxiong, LIN Hui. Defense Strategies against Poisoning Attacks in Semi-Asynchronous Federated Learning [J]. Netinfo Security, 2024, 24(10): 1578-1585. |
| [13] | YAO Mengmeng, WANG Yu, HONG Yuping. The Formal Analysis of SIP Protocol Based on the Recursive Authentication Test [J]. Netinfo Security, 2024, 24(10): 1586-1594. |
| [14] | ZHAO Ge, ZHENG Yang, TAO Zelin. Systematic Risk Assessment Analysis for Smart Wearable Devices [J]. Netinfo Security, 2024, 24(10): 1595-1603. |
| [15] | HE Kaiyu, WANG Bin, YU Zhe, CHEN Fang. Research on ARP Spoofing Attack and Hardware Defense [J]. Netinfo Security, 2024, 24(10): 1604-1610. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||