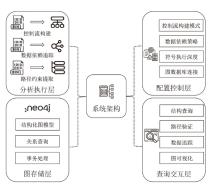
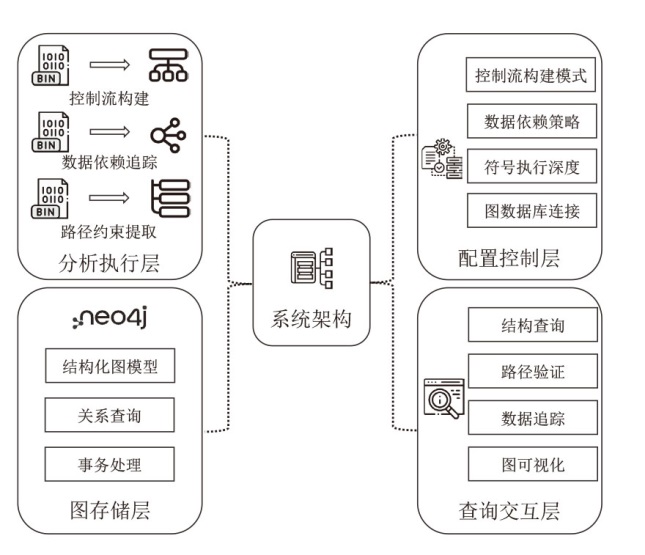
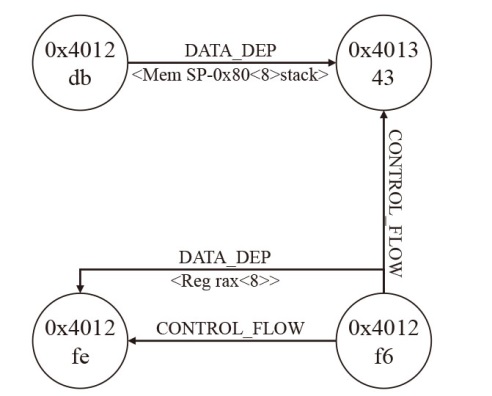
Netinfo Security ›› 2025, Vol. 25 ›› Issue (9): 1357-1366.doi: 10.3969/j.issn.1671-1122.2025.09.004
Previous Articles Next Articles
Intelligent Binary Analysis Method Based on Enhanced Semantic Program Dependency Graph
XUE Lei1( ), ZHANG Jican1, DU Pingxin2
), ZHANG Jican1, DU Pingxin2
- 1. School of Cyber Science and Technology, Sun Yat-sen University, Shenzhen 518107, China
2. NSFOCUS Technologies Group Co., Ltd., Beijing 100089, China
-
Received:2025-05-19Online:2025-09-10Published:2025-09-18
CLC Number:
Cite this article
XUE Lei, ZHANG Jican, DU Pingxin. Intelligent Binary Analysis Method Based on Enhanced Semantic Program Dependency Graph[J]. Netinfo Security, 2025, 25(9): 1357-1366.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.09.004
| 维度 | 核心参数 | 描述 |
|---|---|---|
| 控制流构建 | cfg_type, context_sensitivity_level | 控制快速或模拟执行构建模式,上下文敏感级别(1~3) |
| 数据依赖分析 | track_tmps, cross_ function, def_use_threshold | 控制是否追踪临时变量、是否启用跨过程追踪与定义使用阈值 |
| 符号执行策略 | symbolic_memory, concretize_memory, max_steps | 控制符号内存启用与路径深度 |
| 图数据库同步 | sync_nodes, sync_edges, sync_constraints, batch_size | 控制Neo4j节点、边、约束同步策略 |
| 运行时日志 | log_level | 控制日志详细程度 |
| 优化 等级 | 工具 | 时间/s | 基本块数量/个 | 边数量 /条 | 基本块提升百分比 | 边提升 百分比 |
|---|---|---|---|---|---|---|
| -O0 | Ghidra | 88 | 21533 | 32452 | — | — |
| IDA Pro | 65 | 23901 | 33120 | 10.9% | 2.0% | |
| Binary Ninja | 98 | 25884 | 35648 | 20.2% | 9.8% | |
| SPDG_fast | 67 | 34575 | 46250 | 60.5% | 42.5% | |
| SPDG_emulated | 80 | 34582 | 46260 | 60.6% | 42.5% | |
| -O1 | Ghidra | 51 | 17411 | 27305 | — | — |
| IDA Pro | 45 | 19821 | 29401 | 13.8% | 7.7% | |
| Binary Ninja | 82 | 22100 | 32190 | 26.7% | 17.8% | |
| SPDG_fast | 58 | 30100 | 40143 | 72.9% | 47.0% | |
| SPDG_emulated | 60 | 30109 | 40153 | 72.8% | 47.1% | |
| -O2 | Ghidra | 70 | 17791 | 27904 | — | — |
| IDA Pro | 50 | 19230 | 30210 | 8.1% | 8.2% | |
| Binary Ninja | 85 | 21500 | 32380 | 20.9% | 16.0% | |
| SPDG_fast | 66 | 29812 | 40101 | 67.7% | 43.5% | |
| SPDG_emulated | 72 | 29821 | 40112 | 67.7% | 43.6% | |
| -O3 | Ghidra | 91 | 18535 | 29185 | — | — |
| IDA Pro | 65 | 20310 | 31222 | 9.6% | 7.0% | |
| Binary Ninja | 112 | 22490 | 33100 | 21.0% | 13.4% | |
| SPDG_fast | 80 | 31258 | 42406 | 68.6% | 45.3% | |
| SPDG_emulated | 88 | 31267 | 42417 | 68.6% | 45.3% |
| [1] | XU Weiyang, LI Yao, TANG Yong, et al. Research on Cross-Architecture Vulnerabilities Searching in Binary Executables[J]. Netinfo Security, 2017, 17(9): 21-25. |
| 徐威扬, 李尧, 唐勇, 等. 一种跨指令架构二进制漏洞搜索技术研究[J]. 信息网络安全, 2017, 17(9): 21-25. | |
| [2] | HORWITZ S, REPS T, BINKLEY D. Interprocedural Slicing Using Dependence Graphs[J]. ACM Transactions on Programming Languages and Systems, 1990, 12(1): 26-60. |
| [3] | THE ANGR PROJECT CONTRIBUTORS. Introduction[EB/OL]. (2021-06-05)[2025-05-10]. https://docs.angr.io/en/latest/quickstart.html. |
| [4] | BASQUE Z L, BAJAJ A P, GIBBS W, et al. Ahoy SAILR! There Is No Need to DREAM of C: A Compiler-Aware Structuring Algorithm for Binary Decompilation[C]// USENIX. 33rd USENIX Security Symposium. Berkeley: USENIX, 2024: 361-378. |
| [5] | THE ANGR PROJECT CONTRIBUTORS. Intermediate Representation[EB/OL]. (2021-06-05)[2025-05-10]. https://docs.angr.io/advanced-topics/ir. |
| [6] | FERGUSON J, KAMINSKY D. Reverse Engineering Code with IDA Pro[M]. Burlington: Syngress, 2008. |
| [7] | GHIDRA DEVELOPMENT TEAM. How to Create Program Dependency Graph in Ghidra?[EB/OL]. (2021-07-10)[2025-05-10]. https://github.com/NationalSecurityAgency/ghidra/issues/3491. |
| [8] | KHATTAK U F, AL-NAFFAKH H A H, ALI A. A Review on Graph Representation for Object-Oriented Programming[EB/OL]. (2024-04-05)[2025-05-10]. https://doi.org/10.1051/bioconf/20249700131. |
| [9] | FERRANTE J, OTTENSTEIN K J, WARREN J D. The Program Dependence Graph and Its Use in Optimization[J]. ACM Transactions on Programming Languages and Systems, 1987, 9(3): 319-349. |
| [10] | RAMALINGAM G. On Sparse Evaluation Representations[EB/OL]. (2002-04-28)[2025-05-10]. https://doi.org/10.1016/S0304-3975(00)00315-7. |
| [11] | GITHUB SECURITY LAB. QL Language Specification[EB/OL]. (2021-05-20)[2025-05-10]. https://codeql.github.com/docs/ql-language-reference/ql-language-specification/. |
| [12] | FRANCIS N, GREEN A, GUAGLIARDO P, et al. Cypher: An Evolving Query Language for Property Graphs[C]// ACM. The 2018 International Conference on Management of Data. New York: ACM, 2018: 1433-1445. |
| [13] | YAMAGUCHI F, GOLDE N, ARP D, et al. Modeling and Discovering Vulnerabilities with Code Property Graphs[C]// IEEE. 2014 IEEE Symposium on Security and Privacy. New York: IEEE, 2014: 590-604. |
| [14] | JOERN PROJECT CONTRIBUTORS. Joern Documentation[EB/OL]. (2019-10-23)[2025-05-10]. https://docs.joern.io/quickstart/. |
| [15] | ALLAMANIS M, BROCKSCHMIDT M, KHADEMI M. Learning to Represent Programs with Graphs[EB/OL]. (2018-05-04)[2025-05-10]. https://doi.org/10.48550/arXiv.1711.00740. |
| [16] | CADAR C, DUNBAR D, ENGLER D R. Klee: Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs[C]// USENIX. 8th Symposium on Operating Systems Design and Implementation. Berkeley: USENIX, 2008: 209-224. |
| [17] | SHOSHITAISHVILI Y, WANG Ruoyu, SALLS C, et al. SOK: (State of) The Art of War: Offensive Techniques in Binary Analysis[C]// IEEE. 2016 IEEE Symposium on Security and Privacy. New York: IEEE, 2016: 138-157. |
| [18] | HE Jingxuan, SIVANRUPAN G, TSANKOV P, et al. Learning to Explore Paths for Symbolic Execution[C]// ACM. The 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 2526-2540. |
| [1] | LI Yixuan, JIA Peng, FAN Ximing, CHEN Chen. Control Flow Transformation Based Adversarial Example Generation for Attacking Malware Detection GNN Model [J]. Netinfo Security, 2024, 24(12): 1896-1910. |
| [2] | CHEN Zitong, JIA Peng, LIU Jiayong. Identification Method of Malicious Software Hidden Function Based on Siamese Architecture [J]. Netinfo Security, 2023, 23(5): 62-75. |
| [3] | WANG Yu, LYU Liangshuang, XIA Chunhe. A Windows Malware Detection Method Based on Semantic Analysis [J]. Netinfo Security, 2023, 23(10): 58-63. |
| [4] | WEN Weiping, LIU Chengjie, SHI Lin. A Null Pointer Reference Mining System Based on Data Flow Tracing [J]. Netinfo Security, 2022, 22(9): 40-45. |
| [5] | XIAO Xiaolei, ZHAO Xuelian. Overview of the Research on Governance of Cross-Border Data Flow in China [J]. Netinfo Security, 2022, 22(10): 45-51. |
| [6] | WEN Weiping, FANG Ying, YE He, CHEN Xiarun. A Code Obfuscation System against Symbolic Execution Attacks [J]. Netinfo Security, 2021, 21(7): 17-26. |
| [7] | LIANG Xiaobing, KONG Lingda, LIU Yan, YE Xin. Lightweight Dynamic Binary Instrumentation Algorithm for Embedded Software [J]. Netinfo Security, 2021, 21(4): 89-95. |
| [8] | BI Qinbo, ZHAO Chengdong. Research and Application of 5G Cybersecurity Threat Modeling Based on STRIDE-LM [J]. Netinfo Security, 2020, 20(9): 72-76. |
| [9] | Yanpeng CUI, Luming FENG, Zheng YAN, Huaqing LIN. Research on Software Security Model of Cloud Computing Based on Program Slicing Technology [J]. Netinfo Security, 2019, 19(7): 31-41. |
| [10] | Hu CHEN, Yao ZHOU, Junsuo ZHAO. Symbolic Execution Optimization Methods for Specific File Structures and Key Instructions [J]. Netinfo Security, 2018, 18(9): 86-94. |
| [11] | Xiajing WANG, Changzhen HU, Rui MA, Xinzhu GAO. A Survey of the Key Technology of Binary Program Vulnerability Discovery [J]. Netinfo Security, 2017, 17(8): 1-13. |
| [12] | Jianshan PENG, Qi XI, Qingxian WANG. Automatic Exploitation of Integer Overflow Vulnerabilities in Binary Programs [J]. Netinfo Security, 2017, 17(5): 14-21. |
| [13] | Tao ZHANG, Bei PEI, Weiping WEN, Zhong CHEN. Design and Implementation of Privilege Escalation Attack Detecting System Based on Android Platform [J]. Netinfo Security, 2016, 16(2): 15-21. |
| [14] | Mingliang HE, Zemao CHEN, Jin ZUO. Cluster Anomaly Detection Algorithm Based on Multi-windows Mechanism [J]. Netinfo Security, 2016, 16(11): 33-39. |
| [15] | . Research of Malicious Code in Automatic Unpacking [J]. , 2014, 14(5): 41-. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||