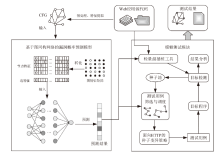
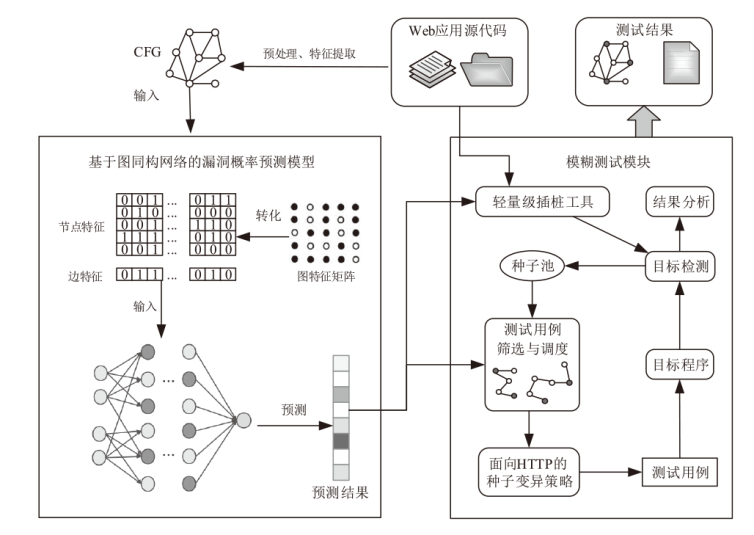
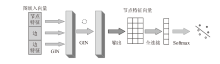
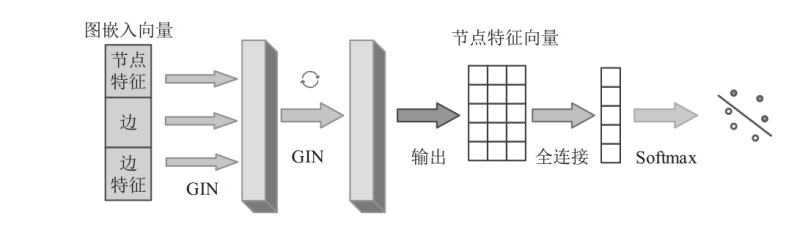
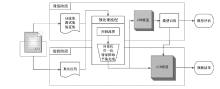
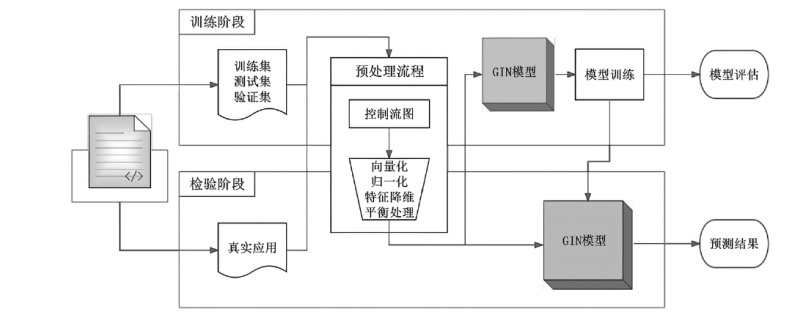
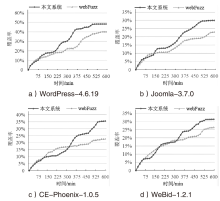
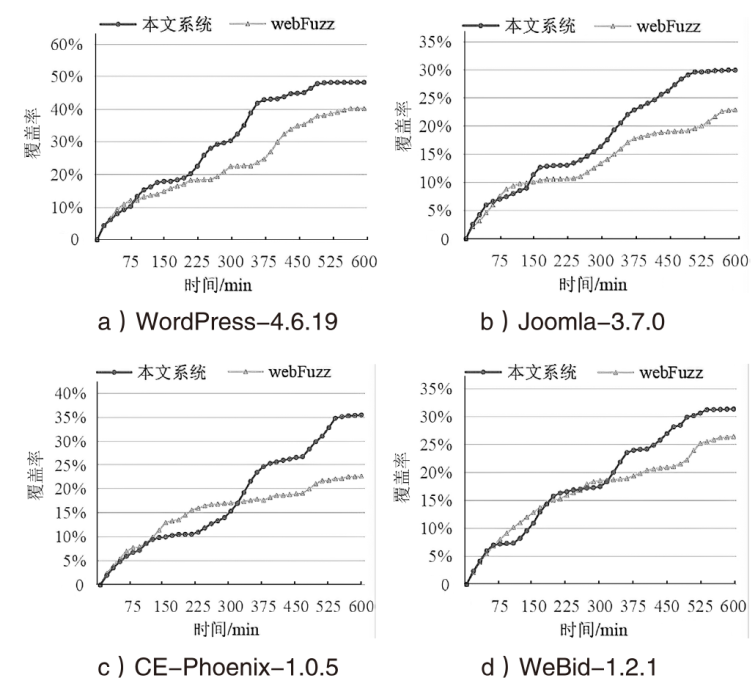
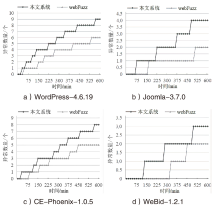
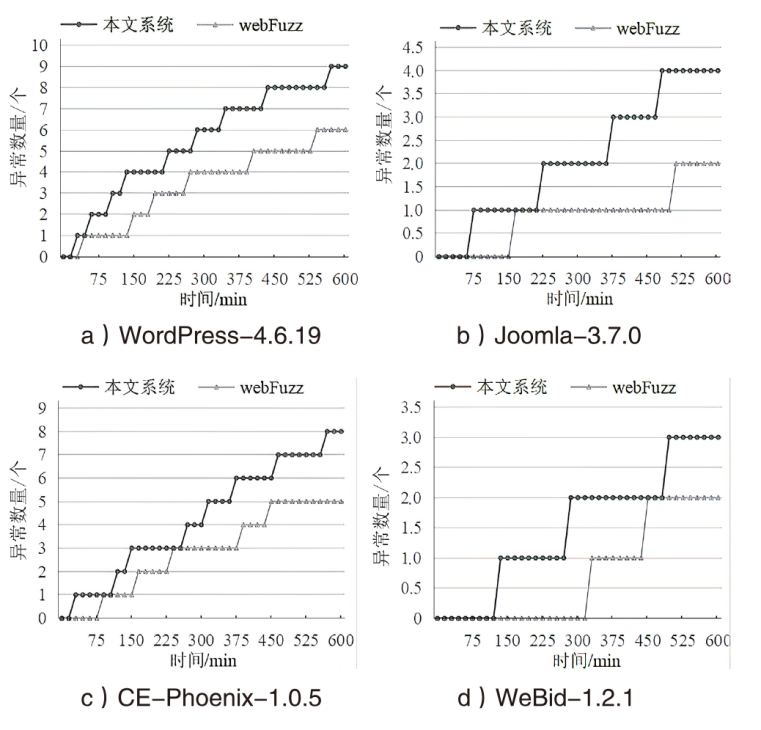
| [1] |
MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44.
|
| [2] |
TU Ling, MA Yue, CHENG Cheng, et al. Hybrid Protocol Deformation Based Web Security Fuzzy Testing and Utility Evaluation Approach[J]. Computer Science, 2017, 44(5): 141-145.
doi: 10.11896/j.issn.1002-137X.2017.05.025
|
|
涂玲, 马跃, 程诚, 等. 基于协议混合变形的Web安全模糊测试与效用评估方法[J]. 计算机科学, 2017, 44(5): 141-145.
doi: 10.11896/j.issn.1002-137X.2017.05.025
|
| [3] |
ZHOU Xinshi. Research and Implementation of Web Vulnerability Mining Technology Based on Fuzzy Testing[D]. Beijing: Beijing University of Posts and Telecommunications, 2020.
|
|
周心实. 基于模糊测试的Web漏洞挖掘技术研究与实现[D]. 北京: 北京邮电大学, 2020.
|
| [4] |
VAN R O, CHARALAMBOUS M A, KAIZER D, et al. WebFuzz: Grey-Box Fuzzing for Web Applications[C]// Springer. 26th European Symposium on Research in Computer Security (ESORICS 2021). Heidelberg: Springer, 2021: 152-172.
|
| [5] |
GAUTHIER F, HASSANSHAHI B, SELWYN-SMITH B, et al. BackREST: A Model-Based Feedback-Driven Greybox Fuzzer for Web Applications[EB/OL]. (2021-08-19)[2024-03-05]. https://arxiv.org/abs/2108.08455v1.
|
| [6] |
ZHAO Jiazhen, LU Yuliang, ZHU Kailong, et al. Cefuzz: An Directed Fuzzing Framework for PHP RCE Vulnerability[EB/OL]. (2022-03-01)[2024-03-05]. https://doi.org/10.3390/electronics11050758.
|
| [7] |
Google. American Fuzzy Lop[EB/OL]. (2023-04-01)[2024-03-05]. http://lcamtuf.coredump.cx/afl/.
|
| [8] |
BÖHME M, PHAM V T, ROYCHOUDHURY A. Coverage-Based Greybox Fuzzing as Markov Chain[C]// ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1032-1043.
|
| [9] |
BÖHME M, PHAM V T, NGUYEN M D, et al. Directed Greybox Fuzzing[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344.
|
| [10] |
CHEN Hongxu, XUE Yinxing, LI Yuekang, et al. Hawkeye: Towards a Desired Directed Grey-Box Fuzzer[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 2095-2108.
|
| [11] |
PortSwigger. Burp Suite[EB/OL]. (2023-03-23)[2024-03-05]. https://portswigger.net/burp.
|
| [12] |
Acunetix. Acunetix Web Vulnerability Scanner[EB/OL]. (2023-03-23)[2024-03-05]. https://www.acunetix.com/.
|
| [13] |
HCLSoftware. AppScan[EB/OL]. (2023-03-23)[2024-03-05]. https://www.hcltechsw.com/appscan.
|
| [14] |
ZAP Dev Team. OWASP Zed Attack Proxy[EB/OL]. (2023-03-23)[2024-03-05]. https://www.zaproxy.org/.
|
| [15] |
Vulners Inc. w3af-Open Source Web Application Security Scanner[EB/OL]. (2023-03-23)[2024-03-05]. http://w3af.org/.
|
| [16] |
LI Yuwei, JI Shouling, LYU Chenyang, et al. V-Fuzz: Vulnerability Prediction-Assisted Evolutionary Fuzzing for Binary Programs[J]. IEEE Transactions on Cybernetics, 2022, 52(5): 3745-3756.
|
| [17] |
ZHAO Yuyue, LI Yangyang, YANG Tengfei, et al. Suzzer: A Vulnerability-Guided Fuzzer Based on Deep Learning[C]// Springer. International Conference on Information Security and Cryptology. Heidelberg: Springer, 2020: 134-153.
|
| [18] |
WANG Yan, JIA Peng, LIU Luping, et al. A Systematic Review of Fuzzing Based on Machine Learning Techniques[EB/OL]. (2020-08-18)[2024-03-05]. https://arxiv.org/abs/1908.01262.
|
| [19] |
Nikic. A PHP Parser Written in PHP[EB/OL]. (2018-03-15)[2024-03-05]. https://github.com/nikic/PHP-Parser.
|
| [20] |
XU K, HU Weihua, LESKOVEC J, et al. How Powerful are Graph Neural Networks?[EB/OL]. (2018-10-01)[2024-03-05]. https://arxiv.org/abs/1810.00826.
|
| [21] |
Wikipedia. Weisfeiler Leman Graph Isomorphism Test[EB/OL]. (2023-03-23)[2024-03-05]. https://en.wikipedia.org/wiki/Weisfeiler_Leman_graph_isomorphism_test.
|
| [22] |
NIST. PHP Vulnerability Test Suite[EB/OL]. (2023-03-23)[2024-03-05]. https://samate.nist.gov/SARD/test-suites/103.
|
 ), ZHANG Chong1,2, WANG Jie1,2, HU Yuyi1,2
), ZHANG Chong1,2, WANG Jie1,2, HU Yuyi1,2