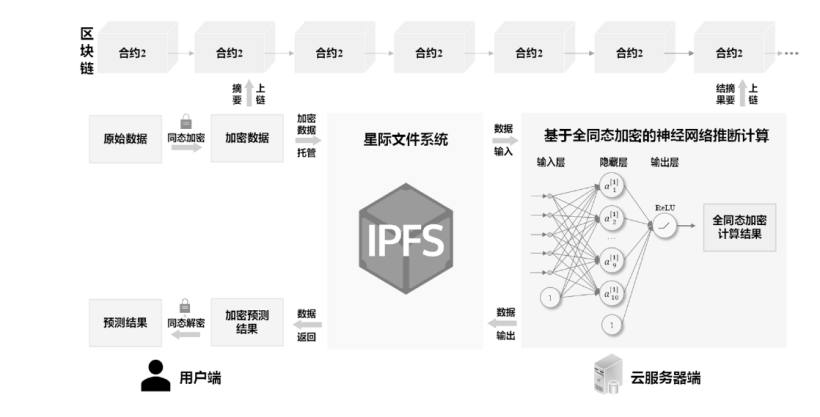
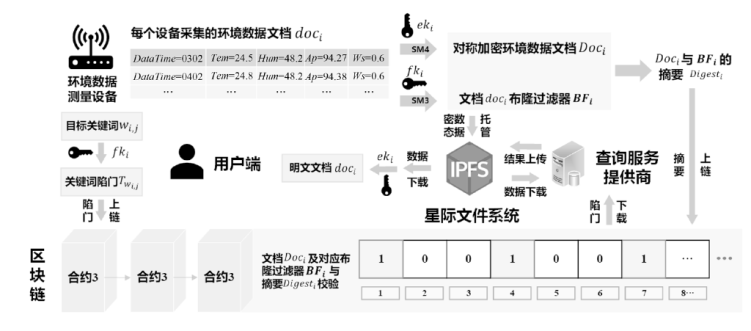
Netinfo Security ›› 2024, Vol. 24 ›› Issue (10): 1515-1527.doi: 10.3969/j.issn.1671-1122.2024.10.005
Previous Articles Next Articles
Privacy Computing in Environmental Big Data on Blockchain
WANG Nan1,2, YUAN Ye1,2, YANG Haoran1,2, WEN Zhouzhi1,2, SU Ming1,2,3,4( ), LIU Xiaoguang1,2
), LIU Xiaoguang1,2
- 1. College of Computer Science, Nankai University, Tianjin 300350, China
2. College of Cyber Science, Nankai University, Tianjin 300350, China
3. State Key Laboratory of Public Big Data, Guizhou 550025, China
4. Key Laboratory of Data and Intelligent System Security, Ministry of Education, Tianjin 300350, China
-
Received:2024-05-22Online:2024-10-10Published:2024-09-27
CLC Number:
Cite this article
WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain[J]. Netinfo Security, 2024, 24(10): 1515-1527.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.10.005
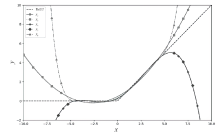
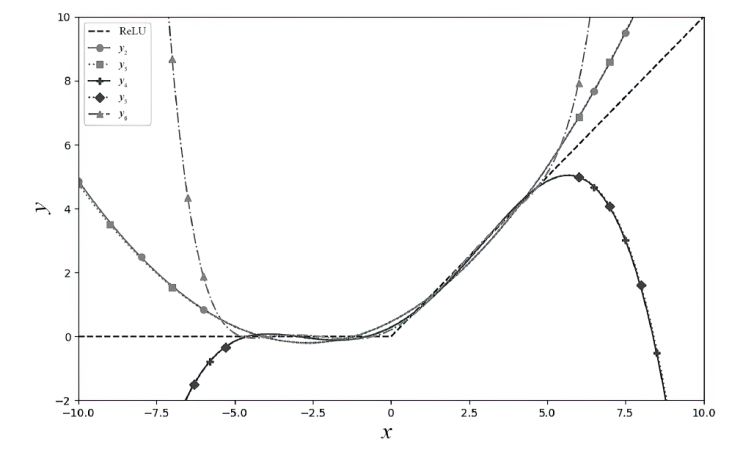
| 多项式次数 | 多项式函数表达式 |
|---|---|
| 2 | y2=0.09401488x2+0.49922105x+0.46555915 |
| 3 | y3=0.000118167887x3+0.0940148772x2+0.497444982x+0.46555915 |
| 4 | y4=-0.00324432116x4+0.000118167487x3+0.163675005x2+0.497444995x+0.291060996 |
| 5 | y5=0.0000042x5-0.003244x4+0.00000122x3+0.163675005x2+0.498072743x+0.291060996 |
| 6 | y6=0.0002379x6+0.0000042x5-0.01137x4+0.00000122x3+0.2315x2+0.4981x+0.210103044 |
| [1] | YANG Jin. Research on Problems and Solutions in the Monitoring and Management of Environmental Impact Assessment Status[J]. Environment and Development, 2020, 32(5): 12-14. |
| 杨晋. 环境影响评价现状监测管理中存在的问题及解决对策研究[J]. 环境与发展, 2020, 32(5): 12-14. | |
| [2] | RAMACHANDRAN M, CHANG V. Towards Performance Evaluation of Cloud Service Providers for Cloud Data Security[J]. International Journal of Information Management, 2016, 36(4): 618-625. |
| [3] | DONG Qiuxiang, GUAN Zhi, CHEN Zhong. A Survey on Computational Cryptography Techniques for Encrypted Data[J]. Computer Applications Research, 2016, 33(9): 9-12. |
| 董秋香, 关志, 陈钟. 加密数据上的计算密码学技术研究综述[J]. 计算机应用研究, 2016, 33(9): 9-12. | |
| [4] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[J]. Iacr Cryptology Eprint Archive, 2012: 1-19. |
| [5] | GOH E J. Secure Indexes[D]. Stanford: Stanford University, 2003. |
| [6] | SCHUH F, LARIMER D. Bitshares 2.0: General Overview[EB/OL]. [2024-04-23]. https://pdfs.semanticscholar.org/c5c6/eefc414d32637890dbe40a1440e46f68e10f.pdf. |
| [7] | RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computation, 1978, 4(11): 169-180. |
| [8] | RIVEST R L, SHAMIR A, ADLEMAN L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126. |
| [9] | ELGAMAL T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. IEEE Transactions on Information Theory, 1985, 31(4): 469-472. |
| [10] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// IACR. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 1999: 223-238. |
| [11] | BONEH D, GOH E J, NISSIM K. Evaluating 2-DNF Formulas on Ciphertexts[C]// IACR. Theory of Cryptography Conference. Heidelberg: Springer, 2005: 325-341. |
| [12] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. (Leveled)Fully Homomorphic Encryption without Bootstrapping[J]. ACM Transactions on Computation Theory (TOCT), 2014, 6(3): 1-36. |
| [13] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate Numbers[C]// IACR. International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2017: 409-437. |
| [14] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]// IEEE. Proceeding of IEEE Symposium on Security and Privacy(S&P 2000). New York: IEEE, 2000: 44-55. |
| [15] | BLOOM B H. Spacetime Tradeoffs in Hash Coding with Allowable Errors[J]. Communications of the ACM, 1970, 13(7): 422-426. |
| [16] | XU Peng, SUSILO W, WANG Wei, et al. ROSE: Robust Searchable Encryption with Forward and Backward Security[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1115-1130. |
| [17] | BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// IACR. EUROCRYPT 2004:International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2004: 506-522. |
| [18] | ABDALLA M, BELLARE M, CATALANO D, et al. Searchable Encryption Revisited: Consistency Properties, Relation to Anonymous IBE, and Extensions[J]. Journal of cryptology, 2008, 21: 350-391. |
| [19] | TONG Qiuyun, MIAO Yinbin, WENG Jian, et al. Verifiable Fuzzy Multi-Keyword Search over Encrypted Data with Adaptive Security[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(5): 5386-5399. |
| [20] | TONG Qiuyun, LI Xinghua, MIAO Yinbin, et al. Privacy-Preserving Boolean Range Query with Temporal Access Control in Mobile Computing[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(5): 5159-5172. |
| [21] | HUANG Qinlong, YAN Guanyu, WEI Qinglin. Attribute-Based Expressive and Ranked Keyword Search Over Encrypted Documents in Cloud Computing[J]. IEEE Transactions on Services Computing, 2023, 16(2): 957-968. |
| [22] | SALEH F. Blockchain without Waste: Proof-of-Stake[J]. The Review of Financial Studies, 2021, 34(3): 1156-1190. |
| [23] | LAMPORT L. The Part-Time Parliament[J]. ACM Transactions on Computer Systems, 1998, 16(2): 133-169. |
| [24] | GM/T 0004-2012 SM3 Cryptographic Hash Algorithm[S]. Beijing: National Cryptography Administration, 2012. |
| GM/T 0004-2012 SM3密码杂凑算法[S]. 北京: 国家密码管理局, 2012. | |
| [25] | GB/T 32907-2016 Information Security Technology: SM4 Block Cipher Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GB/T 32907-2016 信息安全技术 SM4分组密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [26] | CHEN Zhigang, WANG Jian, SONG Xinxia. Research on Fully Homomorphic Encryption[J]. Computer Applications Research, 2014, 31(6): 1624-1631. |
| 陈智罡, 王箭, 宋新霞. 全同态加密研究[J]. 计算机应用研究, 2014, 31(6): 1624-1631. | |
| [27] | XU Shicong. Research on Privacy-Preserving Convolutional Neural Network Forward Propagation Method[D]. Xi’an: Xidian University, 2019. |
| 许世聪. 隐私保护卷积神经网络前向传播方法研究[D]. 西安: 西安电子科技大学, 2019. | |
| [28] | Microsoft. Microsoft SEAL[EB/OL]. (2019-12-30)[2023-05-01]. https://github.com/microsoft/SEAL. |
| [29] | GILAD-BACHRACH R, DOWLIN N, LAINE K, et al. Cryptonets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[C]// IMLS. International Conference on Machine Learning. New York: PMLR, 2016: 201-210. |
| [30] | CHEN Song. Beijing PM2.5[EB/OL]. (2017-01-18)[2024-05-06]. https://archive.ics.uci.edu/dataset/381/beijing+pm2+5+data. |
| [1] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [2] | YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System [J]. Netinfo Security, 2024, 24(9): 1432-1443. |
| [3] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [4] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [5] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [6] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [7] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| [8] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [9] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [10] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [11] | QI Han, WANG Jingtong, ABDULLAH Gani, GONG Changqing. Robustness of Variational Quantum Convolutional Neural Networks Based on Random Quantum Layers [J]. Netinfo Security, 2024, 24(3): 363-373. |
| [12] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [13] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [14] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [15] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||