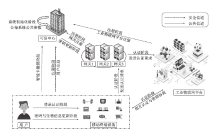
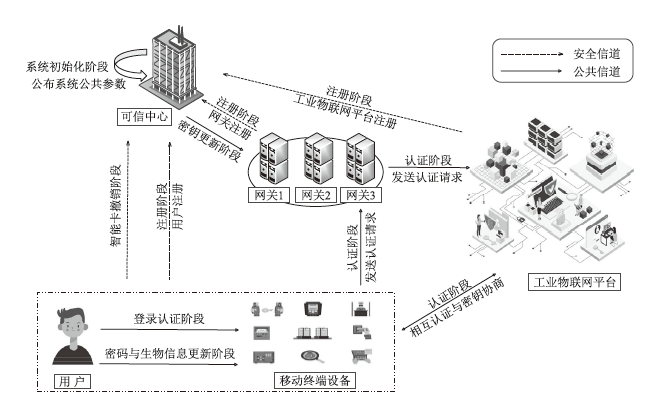
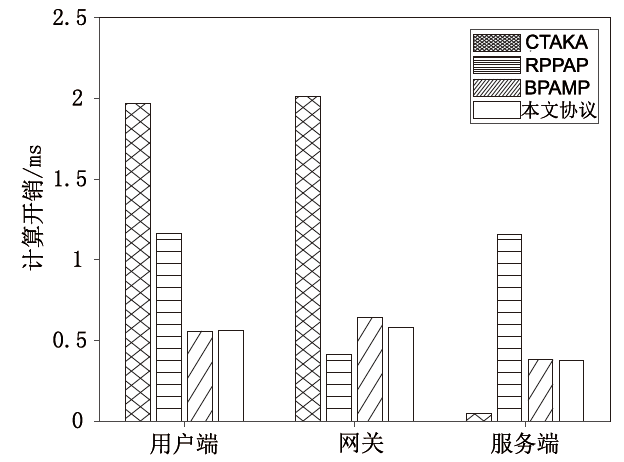
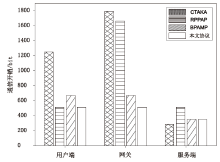
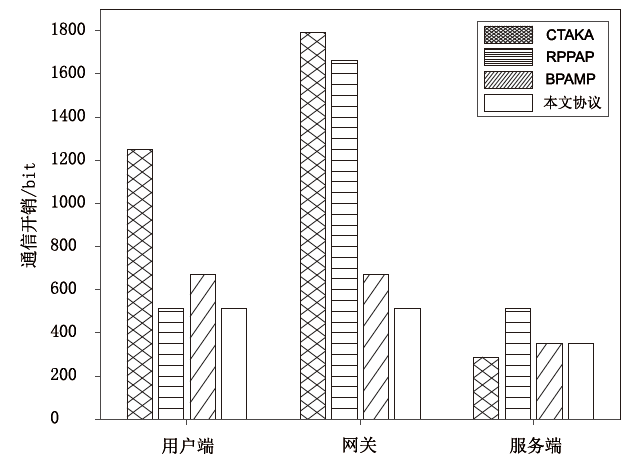
Netinfo Security ›› 2024, Vol. 24 ›› Issue (7): 1015-1026.doi: 10.3969/j.issn.1671-1122.2024.07.004
Previous Articles Next Articles
Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems
ZHANG Xiaojun1,2( ), ZHANG Nan1,2, HAO Yunpu1,2, WANG Zhouyang1,2, XUE Jingting1,2
), ZHANG Nan1,2, HAO Yunpu1,2, WANG Zhouyang1,2, XUE Jingting1,2
- 1. School of Computer Science and Software Engineering, Southwest Petroleum University, Chengdu 610500, China
2. Engineering Research Center for Intelligent Oil & Gas Exploration and Development of Sichuan Province, Southwest Petroleum University, Chengdu 610500, China
-
Received:2024-04-17Online:2024-07-10Published:2024-08-02
CLC Number:
Cite this article
ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems[J]. Netinfo Security, 2024, 24(7): 1015-1026.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.07.004
| 符号 | 描述 | 符号 | 描述 |
|---|---|---|---|
| 系统私钥和公钥 | 单向哈希 函数 | ||
| 网关身份 标识 | 网关的 共同密钥 | ||
| 平台身份 标识 | 用户身份标识 | ||
| 用户登录 口令 | 生物特征 信息 | ||
| 生成函数和再生函数 | 生物密钥和公共信息 | ||
| 随机数 | 凭证 | ||
| 混沌映射 变量 | 哈希值 | ||
| 盲化值 | 协商的密钥 | ||
| 时间戳 | 智能卡 |
| 协议 | 用户端 | 网关 | 服务端 |
|---|---|---|---|
| CTAKA | |||
| RPPAP | |||
| BPAMP | |||
| 本文协议 |
| [1] |
LU Yang, XU Lida. Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics[J]. IEEE Internet of Things Journal, 2019, 6(2): 2103-2115.
doi: 10.1109/JIOT.2018.2869847 |
| [2] | ZUO Yanjun, QI Zhenyu. A Blockchain-Based IoT Framework for Oil Field Remote Monitoring and Control[J]. IEEE Access, 2022, 10: 2497-2514. |
| [3] | LI Na, MA Maode, WANG Hui. ASAP-IIoT: An Anonymous Secure Authentication Protocol for Industrial Internet of Things[J]. Sensors, 2024, 24(4): 1243-1265. |
| [4] | CHAUDHRY S A, YAHYA K, GARG S, et al. LAS-SG: An Elliptic Curve-Based Lightweight Authentication Scheme for Smart Grid Environments[J]. IEEE Transactions on Industrial Informatics, 2023, 19(2): 1504-1511. |
| [5] | CHENG Leixiao, MENG Fei. Certificateless Public Key Authenticated Searchable Encryption with Enhanced Security Model in IIoT Applications[J]. IEEE Internet of Things Journal, 2023, 10(2): 1391-1400. |
| [6] | LIU Suhui, CHEN Liquan, YU Hongtao, et al. BP-AKAA: Blockchain-Enforced Privacy-Preserving Authentication and Key Agreement and Access Control for IIoT[J]. Journal of Information Security and Applications, 2023, 73: 103443-103454. |
| [7] | ZHOU Xiaotong, HE Debiao, NING Jianting, et al. Single-Server Public-Key Authenticated Encryption with Keyword Search and Its Application in IIoT[J]. IEEE Transactions on Network Science and Engineering, 2024, 11(1): 404-415. |
| [8] | KARATI A, ISLAM S H, KARUPPIAH M. Provably Secure and Lightweight Certificateless Signature Scheme for IIoT Environments[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3701-3711. |
| [9] | ZHANG Yinghui, DENG R H, ZHENG Dong, et al. Efficient and Robust Certificateless Signature for Data Crowdsensing in Cloud-Assisted Industrial IoT[J]. IEEE Transactions on Industrial Informatics, 2019, 15(9): 5099-5108. |
| [10] | XIONG Hu, WU Yan, JIN Chuanjie, et al. Efficient and Privacy-Preserving Authentication Protocol for Heterogeneous Systems in IIoT[J]. IEEE Internet of Things Journal, 2020, 7(12): 11713-11724. |
| [11] | CUI Jie, WANG Fengqun, ZHANG Qingyang, et al. Efficient Batch Authentication Scheme Based on Edge Computing in IIoT[J]. IEEE Transactions on Network and Service Management, 2023, 20(1): 357-368. |
| [12] | DONG Jingnan, XU Guangxia, MA Chuang, et al. Blockchain-Based Certificate-Free Cross-Domain Authentication Mechanism for Industrial Internet[J]. IEEE Internet of Things Journal, 2024, 11(2): 3316-3330. |
| [13] | CUI Jie, CHENG Fangzheng, ZHONG Hong, et al. Multi-Factor Based Session Secret Key Agreement for the Industrial Internet of Things[J]. Ad Hoc Networks, 2023, 138: 102997-103009. |
| [14] | YANG Jenho. A Multi-Gateway Authentication and Key-Agreement Scheme on Wireless Sensor Networks for IoT[J]. EURASIP Journal on Information Security, 2023, 2023(1): 2-15. |
| [15] | QIU Shuming, WANG Ding, XU Guoai, et al. Practical and Provably Secure Three-Factor Authentication Protocol Based on Extended Chaotic-Maps for Mobile Lightweight Devices[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(2): 1338-1351. |
| [16] | SURESH D, ODELU V, REDDY A G, et al. Provably Secure Pseudo-Identity Three-Factor Authentication Protocol Based on Extended Chaotic-Maps for Lightweight Mobile Devices[J]. IEEE Access, 2022, 10: 109526-109536. |
| [17] | GUO Xianfeng, ZHANG Jiashu. Secure Group Key Agreement Protocol Based on Chaotic Hash[J]. Information Sciences, 2010, 180(20): 4069-4074. |
| [18] | LEE T. Enhancing the Security of Password Authenticated Key Agreement Protocols Based on Chaotic Maps[J]. Information Sciences, 2015, 290: 63-71. |
| [19] | CHATTERJEE S, ROY S, DAS A K, et al. Secure Biometric-Based Authentication Scheme Using Chebyshev Chaotic Map for Multi-Server Environment[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(5): 824-839. |
| [20] | RYU J, KANG D, WON D. Improved Secure and Efficient Chebyshev Chaotic Map-Based User Authentication Scheme[J]. IEEE Access, 2022, 10: 15891-15910. |
| [21] | WANG Cong, LI Xiaohang, MA Maode, et al. PSAK: A Provably Secure Authenticated Key Agreement Scheme Based on Extended Chebyshev Chaotic Maps for Smart Grid Environments[J]. Transactions on Emerging Telecommunications Technologies, 2023, 34(5): e4752-e4772. |
| [22] | ZHANG Liping, ZHU Yue, REN Wei, et al. An Energy-Efficient Authentication Scheme Based on Chebyshev Chaotic Map for Smart Grid Environments[J]. IEEE Internet of Things Journal, 2021, 8(23): 17120-17130. |
| [23] | MIAO Junfeng, WANG Zhaoshun, WU Zeqing, et al. A Blockchain-Enabled Privacy-Preserving Authentication Management Protocol for Internet of Medical Things[J]. Expert Systems with Applications, 2024, 237: 121329-121339. |
| [24] | QIAO Hui, DONG Xuewen, JIANG Qi, et al. Anonymous Lightweight Authenticated Key Agreement Protocol for Fog-Assisted Healthcare IoT System[J]. IEEE Internet of Things Journal, 2023, 10(19): 16715-16726. |
| [25] | CUI Jie, YU Jing, ZHONG Hong, et al. Chaotic Map-Based Authentication Scheme Using Physical Unclonable Function for Internet of Autonomous Vehicle[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(3): 3167-3181. |
| [26] | SRINIVAS J, DAS A K, WAZID M, et al. Anonymous Lightweight Chaotic Map-Based Authenticated Key Agreement Protocol for Industrial Internet of Things[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(6): 1133-1146. |
| [27] | TANVEER M, BADSHAH A, KHAN A U, et al. CMAF-IIoT: Chaotic Map Based Authentication Framework for Industrial Internet of Things[J]. Internet of Things, 2023, 23: 100902-100919. |
| [28] | KRISHNASRIJA R, MANDAL A K, CORTESI A. A Lightweight Mutual and Transitive Authentication Mechanism for IoT Network[J]. Ad Hoc Networks, 2023, 138: 103003-103019. |
| [29] | ZHANG Yu, SUN Guangmin, ZHAI Peng, et al. A Provably Secure Traceability Authentication Protocol Based on Chebyshev Chaotic Map[J]. Netinfo Security, 2022, 22(12): 25-33. |
| 张昱, 孙光民, 翟鹏, 等. 一种基于切比雪夫混沌映射的可证明安全的溯源认证协议[J]. 信息网络安全, 2022, 22(12): 25-33. | |
| [30] | ZHANG Linhua. Cryptanalysis of the Public Key Encryption Based on Multiple Chaotic Systems[J]. Chaos, Solitons & Fractals, 2008, 37(3): 669-674. |
| [31] | KOCAREV L, TASEV Z. Public-Key Encryption Based on Chebyshev Maps[EB/OL]. (2003-06-20)[2024-04-02]. https://ieeexplore.ieee.org/document/1204947. |
| [32] | JIANG Qi, ZHANG Ning, NI Jianbing, et al. Unified Biometric Privacy Preserving Three-Factor Authentication and Key Agreement for Cloud-Assisted Autonomous Vehicles[J]. IEEE Transactions on Vehicular Technology, 2020, 69(9): 9390-9401. |
| [33] | RANGWANI D, SADHUKHAN D, RAY S, et al. A Robust Provable-Secure Privacy-Preserving Authentication Protocol for Industrial Internet of Things[J]. Peer-to-Peer Networking and Applications, 2021, 14(3): 1548-1571. |
| [1] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [2] | SUN Junfeng, LI Chenghai, SONG Yafei. ACCQPSO: An Improved Quantum Particle Swarm Optimization Algorithm and Its Applications [J]. Netinfo Security, 2024, 24(4): 574-586. |
| [3] | ZHANG Min, FENG Yongqiang, XU Chunxiang, ZHANG Jianhua. Research on Multi-Factor Authenticated Key Agreement Protocol for Smart Home Networks [J]. Netinfo Security, 2024, 24(1): 133-142. |
| [4] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones [J]. Netinfo Security, 2022, 22(9): 21-30. |
| [5] | TONG Xiaojun, SU Yuyue, ZHANG Miao, WANG Zhu. Lightweight Cipher Algorithm Based on Chaos and Improved Generalized Feistel Structure [J]. Netinfo Security, 2022, 22(8): 8-18. |
| [6] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, LUO Shoushan. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain [J]. Netinfo Security, 2022, 22(6): 61-72. |
| [7] | SHEN Yan, YAO Mengmeng. Research on Formal Analysis Based on Event of Group Key Agreement Protocol [J]. Netinfo Security, 2022, 22(5): 30-36. |
| [8] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [9] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [10] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| [11] | ZHAO Guofeng, ZHOU Wentao, XU Chuan, XU Lei. A Secure Identity Authentication Scheme for Space-ground Integrated Network Based on Bilinear Pairing [J]. Netinfo Security, 2020, 20(12): 33-39. |
| [12] | Ruiying CHEN, Zemao CHEN, Hao WANG. Design and Optimization of Security Monitoring and Controlling Protocol in Industrial Control Systems [J]. Netinfo Security, 2019, 19(2): 60-69. |
| [13] | Qingfeng CHENG, Zhanjing RUAN, Ruijie ZHANG. Analysis of Three Pairing-free Authenticated Key Agreement Protocols [J]. Netinfo Security, 2019, 19(1): 16-26. |
| [14] | Yanan CHEN, Qian MEI, Hu XIONG, Weixiang XU. Certificateless Parallel Key-insulated Signature for Industrial Internet of Things [J]. Netinfo Security, 2018, 18(10): 1-9. |
| [15] | Baoyuan KANG, Jiaqiang WANG, Dongyang SHAO, Chunqing LI. A Secure Authentication and Key Agreement Protocol for Heterogeneous Ad Hoc Wireless Sensor Networks [J]. Netinfo Security, 2018, 18(1): 23-30. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||