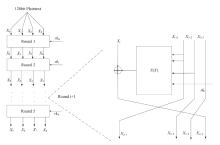
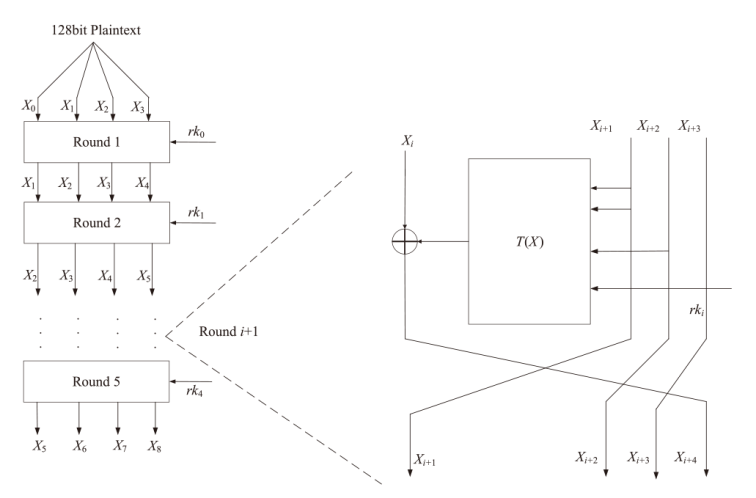
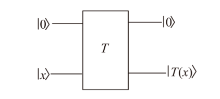
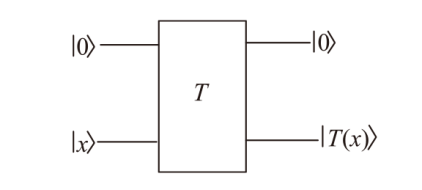
| [1] |
SHOR P. Algorithms for Quantum Computation: Discrete Logarithms and Factoring[C]// IEEE. 35th Annual Symposium on the Foundations of Computer Science. New York: IEEE, 1994: 124-134.
|
| [2] |
National Institute of Standards and Technology. Submission Requirements and Evaluation Criteria for the Post-Quantum Cryptography Standardization Process[EB/OL]. [2023-06-18]. https://csrc.nist.gov/CSRC/media/Projects/Post-Quantum-Cryptography/documents/call-for-proposals-final-dec-2016.pdf.
|
| [3] |
Grover L K. A Fast Quantum Mechanical Algorithm for Database Search[EB/OL]. (1996-11-19) [2023-06-18]. https://doi.org/10.48550/arXiv.quant-ph/9605043.
|
| [4] |
XIE Huiqin, YANG Li. A Quantum Related-Key Attack Based on the Bernstein-Vazirani Algorithm[EB/OL]. (2020-07-14) [2023-06-18]. https://link.springer.com/article/10.1007/s11128-020-02741-2.
|
| [5] |
KAPLAN M, LEURENT G, LEVERRIER A, et al. Quantum Differential and Linear Cryptanalysis[EB/OL]. (2017-05-07) [2023-06-18]. https://doi.org/10.48550/arXiv.1510.05836.
|
| [6] |
XIE Huiqin, YANG Li. Quantum Impossible Differential and Truncated Differential Cryptanalysis[EB/OL]. (2018-07-23) [2023-06-18]. https://doi.org/10.48550/arXiv.1712.06997.
|
| [7] |
VAZIRANI U. On the Power of Quantum Computation[J]. Philosophical Transactions Mathematical Physical & Engineering Sciences, 1998, 356(1743): 1759-1768.
|
| [8] |
KUWAKADO H, MORII M. Quantum Distinguisher between the 3-Round Feistel Cipher and the Random Permutation[C]// IEEE. IEEE International Symposium on Information Theory. New York: IEEE, 2010: 2682-2685.
|
| [9] |
KUWAKADO H, MORII M. Security on the Quantum-Type Even-Mansour Cipher[C]// IEEE. Information Theory and Its Applications (ISITA), 2012 International Symposium on. New York: IEEE, 2012: 312-316.
|
| [10] |
SANTOLI T, SCHAFFNER C. Using Simon's Algorithm to Attack Symmetric-Key Cryptographic Primitives[EB/OL]. (2017-01-31) [2023-06-18]. https://doi.org/10.48550/arXiv.1603.07856.
|
| [11] |
MALVIYA A K, TIWARI N, CHAWLA M. Quantum Cryptanalytic Attacks of Symmetric Ciphers: A Review[J]. Computers and Electrical Engineering, 2022: 101-109.
|
| [12] |
GUO Jian, JEAN J, NIKOLI I, et al. Extended Meet-in-the-Middle Attacks on Some Feistel Constructions[J]. Designs Codes and Cryptography, 2016, 80(3): 587-618.
doi: 10.1007/s10623-015-0120-4
URL
|
| [13] |
PATARIN J. Generic Attacks on Feistel Schemes[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2001: 222-238.
|
| [14] |
KIM P, HAN D, JEONG K C. Time-Space Complexity of Quantum Search Algorithms in Symmetric Cryptanalysis: Applying to AES and SHA-2[J]. Quantum Information Processing, 2018, 17(12): 1-39.
doi: 10.1007/s11128-017-1770-0
URL
|
| [15] |
DONG Xiaoyang, DONG Bingyou, WANG Xiaoyun. Quantum Attacks on Some Feistel Block Ciphers[J]. Designs, Codes and Cryptography. 2020(88): 1179-1203.
|
| [16] |
KAPLAN M, LEURENT G, LEVERRIER A, et al. Breaking Symmetric Cryptosystems Using Quantum Period Finding[C]// Springer. Annual International Cryptology Conference. Heidelberg: Springer, 2016: 207-237.
|
| [17] |
LEVERRIER A. Quantum Differential Cryptanalysis[EB/OL]. (2015-02-12) [2023-06-18]. http://www.dagstuhl.de/en/program/calendar/semhp/?semnr=15371.
|
| [18] |
BERNSTEIN E, VAZIRANI U. Quantum Complexity Theory[J]. Siam Journal on Computing, 1997, 26(5): 1411-1473.
doi: 10.1137/S0097539796300921
URL
|
| [19] |
DAEMEN J, RIJMEN V. Probability Distributions of Correlation and Differentials in Block Ciphers[J]. Journal of Mathematical Cryptology, 2007, 1(3): 221-242.
|
| [20] |
KAPLAN M. Quantum Attacks Against Iterated Block Ciphers[J]. Matematicheskie Voprosy Kriptografii, 2014, 34: 71-90.
|
| [21] |
SHIMON E, YISHAY M. A Construction of a Cipher from a Single Pseudorandom Permutation[J]. Journal of Cryptology, 1997, 10(3): 151-161.
doi: 10.1007/s001459900025
URL
|
| [22] |
KATZ J, LINDELL Y. Introduction to Modern Cryptography[M]. Boca Raton: Chapman & Hall/CRC, 2007.
|
 ), CHEN Fei, ZHANG Feng
), CHEN Fei, ZHANG Feng