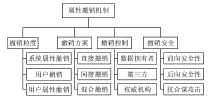
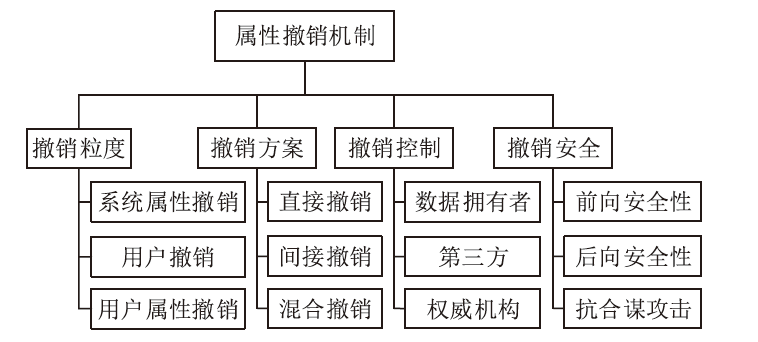
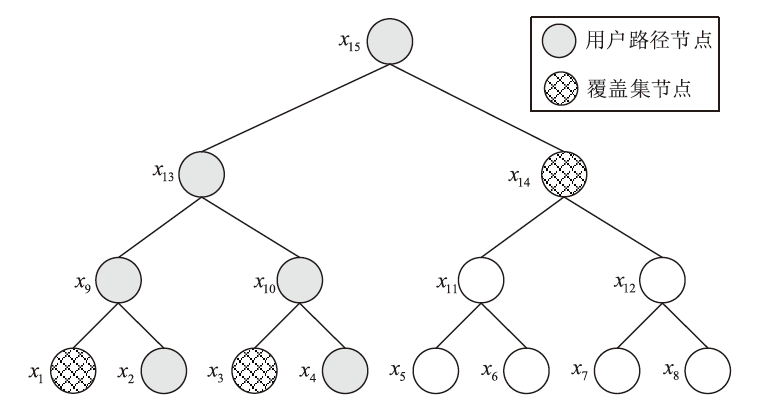
Netinfo Security ›› 2023, Vol. 23 ›› Issue (4): 39-50.doi: 10.3969/j.issn.1671-1122.2023.04.005
Previous Articles Next Articles
Overview of Research on the Revocable Mechanism of Attribute-Based Encryption
LI Li1, ZHU Jiangwen2( ), YANG Chunyan2
), YANG Chunyan2
- 1. Department of Electronic and Communication Engineering, Beijing Electronic Science and Technology Institute, Beijing 100070, China
2. School of Computer Science and Technology, Xidian University, Xi’an 710071, China
-
Received:2022-10-12Online:2023-04-10Published:2023-04-18 -
Contact:ZHU Jiangwen E-mail:zhinen@stu.xidian.edu.cn
CLC Number:
Cite this article
LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption[J]. Netinfo Security, 2023, 23(4): 39-50.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.04.005
| 方案 | 支持模式 | 撤销粒度 | |||||
|---|---|---|---|---|---|---|---|
| CP-ABE | KP-ABE | 用户 | 系统属性 | 用户属性 | |||
| 文献[8] | 支持 | 支持 | 支持 | 支持 | 不支持 | ||
| 文献[10] | 不支持 | 支持 | 支持 | 支持 | 支持 | ||
| 文献[11] | 不支持 | 支持 | 支持 | 不支持 | 不支持 | ||
| 文献[12] | 支持 | 不支持 | 支持 | 不支持 | 不支持 | ||
| 文献[16] | 支持 | 不支持 | 支持 | 不支持 | 不支持 | ||
| 文献[19] | 支持 | 不支持 | 支持 | 不支持 | 不支持 | ||
| 文献[22] | 不支持 | 支持 | 支持 | 不支持 | 不支持 | ||
| 文献[24] | 支持 | 支持 | 支持 | 支持 | 支持 | ||
| 文献[26] | 支持 | 不支持 | 支持 | 支持 | 支持 | ||
| 方案 | 访问结构 | 安全信道 | 困难假设 | ||||
| 文献[8] | 非单调线性结构 | 需要 | BDH | ||||
| 文献[10] | LSSS | 需要 | q-BDHE | ||||
| 文献[11] | LSSS | 需要 | CDH、DLIN | ||||
| 文献[12] | LSSS | 不需要 | q-DPBDHE2 | ||||
| 文献[16] | LSSS | 需要 | BDHE | ||||
| 文献[19] | LSSS | 需要 | q-BDHE | ||||
| 文献[22] | 树型结构 | 需要 | (d+3)-MDDH | ||||
| 文献[24] | 树型结构 | 需要 | DBDH | ||||
| 文献[26] | LSSS | 需要 | n-eDDH | ||||
| 方案 | 存储开销 | ||
|---|---|---|---|
| 公钥长度 | 用户私钥长度 | 密文长度 | |
| 文献[8] | 2U+4 | 3l | 2S+3 |
| 文献[10] | R+2 | 4l+r+1 | 2S+3-r |
| 文献[12] | 2U1+8 | 1 | 4l+1 |
| 文献[16] | U+R+T+4 | S+3T+R+2 | l+4 |
| 文献[19] | U+T+logD+3 | TlogN | T(T+l+1) |
| 文献[22] | U+3T+7 | 2l+4 | RcT+S+4 |
| 文献[24] | 3U+3 | 2U+3 | U+4 |
| 文献[26] | 2N+2U+3 | 2S+1 | 6l+2 |
| 方案 | 计算开销 | ||
| 系统初始化 | 加密 | 用户解密 | |
| 文献[8] | (2U+3)e | (2S+2)e | Ie+6IP |
| 文献[10] | Re+p | (2S+3-r)e | (R+I+1)e+(2I+2)p |
| 文献[12] | U1e+U1p | (6l+1)e | e |
| 文献[16] | (R+1)e+p | (r+T+2l+3)e | (I+1)e+(2I+4)p |
| 文献[19] | e+p | (T(Ul+T))e | Ie+Ip |
| 文献[22] | e+p | (RcT+S+2)e+Rcp | Ie+(2I+T+2)p |
| 文献[24] | 3Ue+p | (U+2)e | (U+1)p |
| 文献[26] | (2N+2U+1)e | (2(U-R)l+3l+1)e+p | Ie+(2I+2(U-R)+2)p |
| 方案 | 访问结构 | 撤销控制 | 支持模式 | 安全信道 | |
|---|---|---|---|---|---|
| 文献[3] | 树型结构 | 权威机构 | CP-ABE | 需要 | |
| 文献[31] | 树型结构 | 权威机构 | KP-ABE | 需要 | |
| 文献[32] | 树型结构 | 第三方 | CP-ABE | 需要 | |
| 文献[33] | 树型结构 | 第三方 | CP-ABE | 需要 | |
| 文献[35] | LSSS | 第三方 | CP-ABE | 需要 | |
| 文献[40] | LSSS | 第三方 | CP-ABE | 需要 | |
| 文献[42] | 树型结构 | 第三方 | CP-ABE | 需要 | |
| 文献[43] | 树型结构 | 第三方 | CP-ABE | 需要 | |
| 文献[46] | 树型结构 | 第三方 | CP-ABE | 需要 | |
| 文献[49] | LSSS | 第三方 | CP-ABE | 需要 | |
| 文献[52] | LSSS | 第三方 | CP-ABE | 需要 | |
| 文献[54] | 树型结构 | 第三方 | CP-ABE | 需要 | |
| 文献[55] | LSSS | 第三方 | CP-ABE | 需要 | |
| 方案 | 即时撤销 | 安全模型 | 困难假设 | ||
| 文献[3] | 不支持 | 随机预言机模型 | DBDH | ||
| 文献[31] | 不支持 | 随机预言机模型 | DBDH | ||
| 文献[32] | 支持 | 一般群模型 | BDH | ||
| 文献[33] | 支持 | 一般群模型 | BDH | ||
| 文献[35] | 支持 | 随机预言机模型 | q-BDHE | ||
| 文献[40] | 支持 | 随机预言机模型 | q-BDHE | ||
| 文献[42] | 支持 | 标准模型 | CDH | ||
| 文献[43] | 支持 | 随机预言机模型 | DBDH | ||
| 文献[46] | 支持 | × | × | ||
| 文献[49] | 支持 | 随机预言机模型 | q-BDHE | ||
| 文献[52] | 支持 | 随机预言机模型 | q-BDHE | ||
| 文献[54] | 支持 | 随机预言机模型 | q-BDHE | ||
| 文献[55] | 支持 | 随机预言机模型 | q-BDHE | ||
| 方案 | 存储开销 | 计算开销 | 撤销引起的 计算开销 | |||
|---|---|---|---|---|---|---|
| 用户私钥长度 | 密文 长度 | 用户 加密 | 用户 解密 | 用户 私钥 | 密文 | |
| 文献[3] | 2S+1 | 2l+3 | (2l+2)e | Ie+2Ip | × | × |
| 文献[32] | S+1 | l+3 | (R+2)e | Re+(R+1)p | × | × |
| 文献[33] | 2S+1 | 2l+Rl+3 | (2l+2)e | Ie+3p | 7ne | 0 |
| 文献[35] | A+2 | (4l+3)f | (5l+3)fe | nIe+6Ip | np | 2mp |
| 文献[40] | S+2 | 2l+3 | (3l+2)e | 2Ie+(2I+2)p | ne | me |
| 文献[42] | 1 | 2l+3 | (3l+3)e | e | 2ne | (2l+3)me |
| 文献[43] | 2S+2 | 3l+2r+3 | (3l+2r+2)e | (r+2)e+ (3I+2r+1) | 5e | me |
| 文献[46] | 2S | 4l+3 | 0 | e | 0 | (6l+1)me |
| 文献[49] | S+4 | 2l+5 | 2e | p | 0 | (2l+1)me |
| 文献[52] | 1 | 2l+5 | (3l+5)e | e | ne | me |
| 文献[54] | 2S | 4l+2 | (6l+1)e | (I+2)e+3Ip | ne | me |
| 文献[55] | 1 | 2l+4 | (2l+2)e | e | ne | 0 |
| [1] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Workshop on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1984: 47-53. |
| [2] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [3] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. 2007 IEEE Symposium on Security and Privacy(SP’07). New York: IEEE, 2007: 321-334. |
| [4] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [5] | ZHAO Zhiyuan, WANG Jianhua, ZHU Zhiqiang, et al. Survey of Attribute-Based Encryption in Cloud Storage Environment[J]. Application Research of Computers, 2018, 35(4): 961-968. |
| 赵志远, 王建华, 朱智强, 等. 云存储环境下属性基加密综述[J]. 计算机应用研究, 2018, 35(4):961-968. | |
| [6] | ATTRAPADUNG N, IMAI H. Attribute-Based Encryption Supporting Direct/Indirect Revocation Modes[C]// Springer. IMA International Conference on Cryptography and Coding. Heidelberg: Springer, 2009: 278-300. |
| [7] | WANG Jinxiao. A Study on the Revocation Mechanism of Attribute-Based Encryption[D]. Hangzhou: Hangzhou Dianzi University, 2013. |
| 王锦晓. 属性基加密中撤销机制的研究[D]. 杭州: 杭州电子科技大学, 2013. | |
| [8] | OSTROVSKY R, SAHAI A, WATERS B. Attribute-Based Encryption with Non-Monotonic Access Structures[C]// ACM. 14th ACM Conference on Computer and Communications Security. New York: ACM, 2007: 195-203. |
| [9] | ATTRAPADUNG N, IMAI H. Conjunctive Broadcast and Attribute-Based Encryption[C]// Springer. International Conference on Pairing-Based Cryptography. Heidelberg: Springer, 2009: 248-265. |
| [10] | LI Qiang, FENG Dengguo, ZHANG Liwu. An Attribute Based Encryption Scheme with Fine-Grained Attribute Revocation[C]// IEEE. 2012 IEEE Global Communications Conference(GLOBECOM). New York: IEEE, 2012: 885-890. |
| [11] | WANG Changji, FANG Jian, XIE Jiangguo. Fully Secure Unbounded Revocable Key-Policy Attribute-Based Encryption Scheme[C]// Springer. International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage. Heidelberg: Springer, 2016: 251-264. |
| [12] |
ZHANG Kai, MA Jianfeng, LI Hui, et al. Multi-Authority Attribute-Based Encryption with Efficient Revocation[J]. Journal on Communications, 2017, 38(3): 83-91.
doi: 10.11959/j.issn.1000-436x.2017068 |
|
张凯, 马建峰, 李辉, 等. 支持高效撤销的多机构属性加密方案[J]. 通信学报, 2017, 38(3):83-91.
doi: 10.11959/j.issn.1000-436x.2017068 |
|
| [13] |
WANG Hao, ZHENG Zhihua, WU Lei, et al. New Directly Revocable Attribute-Based Encryption Scheme and Its Application in Cloud Storage Environment[J]. Cluster Computing, 2017, 20(3): 2385-2392.
doi: 10.1007/s10586-016-0701-7 URL |
| [14] | YAMADA K, ATTRAPADUNG N, EMURA K, et al. Generic Constructions for Fully Secure Revocable Attribute-Based Encryption[J]. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2018, 101(9): 1456-1472. |
| [15] | MICHALAS A, WEINGARTEN N. Healthshare: Using Attribute-Based Encryption for Secure Data Sharing between Multiple Clouds[C]// IEEE. 2017 IEEE 30th International Symposium on Computer-Based Medical Systems(CBMS). New York: IEEE, 2017: 811-815. |
| [16] | LIU J K, YUEN T H, ZHANG Peng, et al. Time-Based Direct Revocable Ciphertext-Policy Attribute-Based Encryption with Short Revocation List[C]// Springer. International Conference on Applied Cryptography and Network Security. Heidelberg: Springer, 2018: 516-534. |
| [17] |
ZHAO Yang, REN Mao, JIANG Songquan, et al. An Efficient and Revocable Storage CP-ABE Scheme in the Cloud Computing[J]. Computing, 2019, 101(8): 1041-1065.
doi: 10.1007/s00607-018-0637-2 |
| [18] | DONG Xingting, ZHANG Yanhua, WANG Baocang, et al. Server-Aided Revocable Attribute-Based Encryption from Lattices[EB/OL]. (2020-02-12)[2022-09-02]. https://doi.org/10.1155/2020/1460531. |
| [19] | WEI Jianghong, CHEN Xiaofeng, HUANG Xinyi, et al. RS-HABE: Revocable-Storage and Hierarchical Attribute-Based Access Scheme for Secure Sharing of E-Health Records in Public Cloud[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(5): 2301-2315. |
| [20] | ZHANG Jiawei, LI Teng, JIANG Qi, et al. Enabling Efficient Traceable and Revocable Time-Based Data Sharing in Smart City[J]. EURASIP Journal on Wireless Communications and Networking, 2022(1): 1-26. |
| [21] | YANG Yanjiang, DING Xuhua, LU Haibing, et al. Achieving Revocable Fine-Grained Cryptographic Access Control over Cloud Data[C]// Springer. 16th International Conference, ISC 2013. Heidelberg: Springer, 2015: 293-308. |
| [22] |
SHI Yanfeng, ZHENG Qingji, LIU Jiqiang, et al. Directly Revocable Key-Policy Attribute-Based Encryption with Verifiable Ciphertext Delegation[J]. Information Sciences, 2015, 295: 221-231.
doi: 10.1016/j.ins.2014.10.020 URL |
| [23] | LEWKO A, SAHAI A, WATERS B. Revocation Systems with Very Small Private Keys[C]// IEEE. 2010 IEEE Symposium on Security and Privacy. New York: IEEE, 2010: 273-285. |
| [24] | YU Shucheng, WANG Cong, REN Kui, et al. Attribute Based Data Sharing with Attribute Revocation[C]// ACM. 5th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2010: 261-270. |
| [25] | ZHU Guobin, XIE Xin, ZHANG Xing, et al. Direct Revocable Ciphertext Policy Attribute-Based Encryption Scheme with Constant-Size Ciphertext[J]. Journal of University of Electronic Science and Technology of China, 2021, 50(1): 76-83. |
| 朱国斌, 谢鑫, 张星, 等. 支持直接撤销的固长密文策略属性基加密方案[J]. 电子科技大学学报, 2021, 50(1):76-83. | |
| [26] |
WANG Pengpian, FENG Dengguo, ZHANG Liwu. CP-ABE Scheme Supporting Fully Fine-Grained Attribute Revocation[J]. Journal of Software, 2012, 23(10): 2805-2816.
doi: 10.3724/SP.J.1001.2012.04184 URL |
| 王鹏翩, 冯登国, 张立武. 一种支持完全细粒度属性撤销的CP-ABE方案[J]. 软件学报, 2012, 23(10):2805-2816 | |
| [27] |
YAN Xixi, MENG Hui. Ciphertext Policy Attribute-Based Encryption Scheme Supporting Direct Revocation[J]. Journal on Communications, 2016, 37(5): 44-50.
doi: 10.11959/j.issn.1000-436x.2016091 |
|
闫玺玺, 孟慧. 支持直接撤销的密文策略属性基加密方案[J]. 通信学报, 2016, 37(5):44-50.
doi: 10.11959/j.issn.1000-436x.2016091 |
|
| [28] | ZHANG Wenfang, CHEN Zhen, LIU Xudong, et al. CP-ABE Scheme Supporting Fine-Grained Attribute Direct Revocation[J]. Journal of Software, 2019, 30(9): 2760-2771. |
| 张文芳, 陈桢, 刘旭东, 等. 支持细粒度属性直接撤销的CP-ABE方案[J]. 软件学报, 2019, 30(9):2760-2771. | |
| [29] | NAOR D, NAOR M, LOTSPIECH J. Revocation and Tracing Schemes for Stateless Receivers[C]// Springer. Annual International Cryptology Conference. Heidelberg: Springer, 2001: 41-62. |
| [30] | PIRRETTI M, TRAYNOR P, MCDANIEL P, et al. Secure Attribute-Based Systems[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 99-112. |
| [31] | BOLDYREVA A, GOYAL V, KUMAR V. Identity-Based Encryption with Efficient Revocation[C]// ACM. 15th ACM Conference on Computer and Communications Security. New York: ACM, 2008: 417-426. |
| [32] | IBRAIMI L, PETKOVIC M, NIKOVA S, et al. Mediated Ciphertext-Policy Attribute-Based Encryption and Its Application[C]// Springer. International Workshop on Information Security Applications. Heidelberg: Springer, 2009: 309-323. |
| [33] |
HUR J, NOH D K. Attribute-Based Access Control with Efficient Revocation in Data Outsourcing Systems[J]. IEEE Transactions on Parallel and Distributed Systems, 2010, 22(7): 1214-1221.
doi: 10.1109/TPDS.2010.203 URL |
| [34] |
LI Jiguo, YAO Wei, HAN Jinguang, et al. User Collusion Avoidance CP-ABE with Efficient Attribute Revocation for Cloud Storage[J]. IEEE Systems Journal, 2017, 12(2): 1767-1777.
doi: 10.1109/JSYST.4267003 URL |
| [35] |
YANG Kan, JIA Xiaohua. Expressive, Efficient, and Revocable Data Access Control for Multi-Authority Cloud Storage[J]. IEEE Transactions on Parallel and Distributed Systems, 2013, 25(7): 1735-1744.
doi: 10.1109/TPDS.2013.253 URL |
| [36] |
YANG Kan, JIA Xiaohua, REN Kui, et al. DAC-MACS: Effective Data Access Control for Multiauthority Cloud Storage Systems[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(11): 1790-1801.
doi: 10.1109/TIFS.2013.2279531 URL |
| [37] | YUEN T H, ZHANG Ye, YIU S M, et al. Identity-Based Encryption with Post-Challenge Auxiliary Inputs for Secure Cloud Applications and Sensor Networks[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2014: 130-147. |
| [38] | YANG Yanjing, LU Haibing, WENG Jian, et al. Fine-Grained Conditional Proxy Re-Encryption and Application[C]// Springer. International Conference on Provable Security. Heidelberg: Springer, 2014: 206-222. |
| [39] | YANG Yanjiang, LIU J K, LIANG Kaitai, et al. Extended Proxy-Assisted Approach: Achieving Revocable Fine-Grained Encryption of Cloud Data[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2015: 146-166. |
| [40] | ZU Longhui, LIU Zhenhua, LI Juanjuan. New Ciphertext-Policy Attribute-Based Encryption with Efficient Revocation[C]// IEEE. 2014 IEEE International Conference on Computer and Information Technology. New York: IEEE, 2014: 281-287. |
| [41] | ZHANG Weiwei, FENG Gui, LIU Jianyi, et al. A DRM Scheme Supporting Attribute Revocation and Outsourced Decryption in the Cloud Compting Environment[J]. Journal of Computer Research and Development, 2015, 52(12): 2659-2668. |
| 张维纬, 冯桂, 刘建毅, 等. 云计算环境下支持属性撤销的外包解密DRM方案[J]. 计算机研究与发展, 2015, 52(12):2659-2668. | |
| [42] |
SUN Lei, ZHAO Zhiyuan, WANG Jianhua, et al. Attribute-Based Encryption Scheme Supporting Attribute Revocation in Cloud Storage Environment[J]. Journal on Communications, 2019, 40(5): 47-56.
doi: 10.11959/j.issn.1000-436x.2019116 |
|
孙磊, 赵志远, 王建华, 等. 云存储环境下支持属性撤销的属性基加密方案[J]. 通信学报, 2019, 40(5):47-56.
doi: 10.11959/j.issn.1000-436x.2019116 |
|
| [43] | ZHANG Peng, CHEN Zehong, LIANG Kaitai, et al. A Cloud-Based Access Control Scheme with User Revocation and Attribute Update[C]// Springer. Australasian Conference on Information Security and Privacy. Heidelberg: Springer, 2016: 525-540. |
| [44] |
WANG Shangping, ZHANG Xia, ZHANG Yaling. Efficient Revocable and Grantable Attribute-Based Encryption from Lattices with Fine-Grained Access Control[J]. IET Information Security, 2018, 12(2): 141-149.
doi: 10.1049/ise2.v12.2 URL |
| [45] |
FAN Kai, LIU Tingting, ZHANG Kuan, et al. A Secure and Efficient Outsourced Computation on Data Sharing Scheme for Privacy Computing[J]. Journal of Parallel and Distributed Computing, 2020, 135: 169-176.
doi: 10.1016/j.jpdc.2019.09.008 URL |
| [46] | TU Shanshan, WAQAS M, HUANG Fengming, et al. A Revocable and Outsourced Multi-Authority Attribute-Based Encryption Scheme in Fog Computing[EB/OL]. (2021-08-04)[2022-09-01]. https://doi.org/10.1016/j.comnet.2021.108196. |
| [47] | YANG Yang, SUN Jianguo, LIU Zechao, et al. Practical Revocable and Multi-Authority CP-ABE Scheme from RLWE for Cloud Computing[J]. Journal of Information Security and Applications, 2022, 65: 2214-2126. |
| [48] | LYUBASHEVSKY V, PEIKERT C, REGEV O. On Ideal Lattices and Learning with Errors over Rings[J]. Journal of the ACM, 2013, 60(6): 1-35. |
| [49] |
ZHAO Jing, ZENG Peng, CHOO K K R. An Efficient Access Control Scheme with Outsourcing and Attribute Revocation for Fog-Enabled E-Health[J]. IEEE Access, 2021, 9: 13789-13799.
doi: 10.1109/Access.6287639 URL |
| [50] |
MING Yang, HE Baokang, WANG Chenhao. Efficient Revocable Multi-Authority Attribute-Based Encryption for Cloud Storage[J]. IEEE Access, 2021, 9: 42593-42603.
doi: 10.1109/ACCESS.2021.3066212 URL |
| [51] |
MING Yang, HE Baokang. Attribute Revocation and Verifiable Outsourcing Supported Multi-Authority Attribute-Based Encryption Scheme[J]. Journal of Computer Applications, 2019, 39(12): 3556-3562.
doi: 10.11772/j.issn.1001-9081.2019061019 |
|
明洋, 何宝康. 支持属性撤销的可验证外包的多授权属性加密方案[J]. 计算机应用, 2019, 39(12):3556-3562.
doi: 10.11772/j.issn.1001-9081.2019061019 |
|
| [52] |
MA Hua, XIE Ying, WANG Jianfeng, et al. Revocable Attribute-Based Encryption Scheme with Efficient Deduplication for Ehealth Systems[J]. IEEE Access, 2019, 7: 89205-89217.
doi: 10.1109/ACCESS.2019.2926627 |
| [53] |
LI Qi, MA Jianfeng, LI Rui, et al. Secure, Efficient and Revocable Multi-Authority Access Control System in Cloud Storage[J]. Computers & Security, 2016, 59: 45-59.
doi: 10.1016/j.cose.2016.02.002 URL |
| [54] |
LIU Zechao, JIANG Z L, WANG Xuan, et al. Practical Attribute-Based Encryption: Outsourcing Decryption, Attribute Revocation and Policy Updating[J]. Journal of Network and Computer Applications, 2018, 108: 112-123.
doi: 10.1016/j.jnca.2018.01.016 URL |
| [55] | LI Xuejun, ZHANG Dan, LI Hui. Efficient Revocable Attribute Based Encryption Scheme[J]. Journal of Communications, 2019, 40(6): 32-39. |
|
李学俊, 张丹, 李晖. 可高效撤销的属性基加密方案[J]. 通信学报, 2019, 40(6):32-39.
doi: 10.11959/j.issn.1000-436x.2019150 |
|
| [56] | ATTRAPADUNG N, IMAI H. Attribute-Based Encryption Supporting Direct/Indirect Revocation Modes[C]// Springer. IMA International Conference on Cryptography and Coding. Heidelberg: Springer, 2009: 278-300. |
| [1] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [2] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| [3] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [4] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [5] | SHI Guofeng, ZHANG Xinglan. An Attribute-based Encryption Scheme for Cloud Storage Supporting Range Ciphertext Search [J]. Netinfo Security, 2020, 20(6): 75-81. |
| [6] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [7] | XU Shengwei, WANG Feijie. Attribute-based Encryption Scheme Traced Under Multi-authority [J]. Netinfo Security, 2020, 20(1): 33-39. |
| [8] | Jinmiao WANG, Guowei WANG, Mei WANG, Ruijin ZHU. Achieving Privacy Preserving and Flexible Access Control in Fog Computing [J]. Netinfo Security, 2019, 19(9): 41-45. |
| [9] | Shengyu WANG, Jinmiao WANG, Qingfeng DONG, Ruijin ZHU. A Survey of Attribute-based Encryption Technology [J]. Netinfo Security, 2019, 19(9): 76-80. |
| [10] | Jianhua LIU, Xiaokun ZHENG, Dong ZHENG, Zhangheng AO. Secure Attribute Based Encryption Enabled Cloud Storage System with Ciphertext Search [J]. Netinfo Security, 2019, 19(7): 50-58. |
| [11] | Zhongyuan QIN, Yin HAN, Qunfang ZHANG, Xuejin ZHU. An Improved Scheme of Multi-PKG Cloud Storage Access Control [J]. Netinfo Security, 2019, 19(6): 11-18. |
| [12] | Xixi YAN, Qichao ZHANG, Yongli TANG, Qinlong HUANG. Ciphertext Policy Attribute-based Encryption Scheme Supporting Traitor Tracing [J]. Netinfo Security, 2019, 19(5): 47-53. |
| [13] | Qinghe DONG, Qian HE, Bingcheng JIANG, Peng LIU. Scheme of Cloud Database Oriented Multi-tenant Attribute-based Security Isolation and Data Protection [J]. Netinfo Security, 2018, 18(7): 60-68. |
| [14] | Xixi YAN, Yuan LIU, Mingxing HU, Qinlong HUANG. LWE-based Multi-authority Attribute-based Encryption Scheme in Cloud Environment [J]. Netinfo Security, 2017, 17(9): 128-133. |
| [15] | YAN Xixi, YE Qing, LIU Yu. Attribute-based Encryption Scheme Supporting Privacy Preserving and User Revocation in the Cloud Environment [J]. 信息网络安全, 2017, 17(6): 14-21. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||