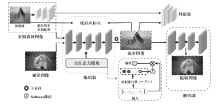
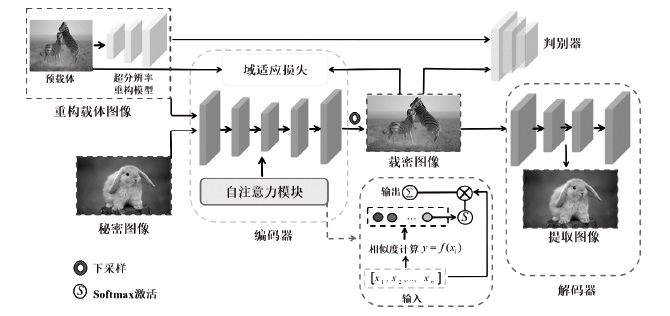
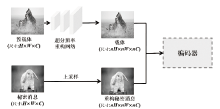
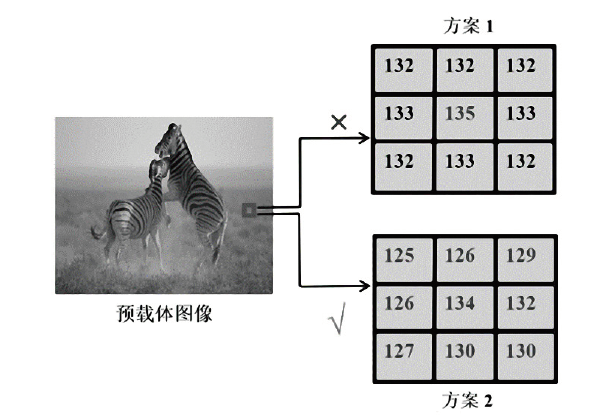
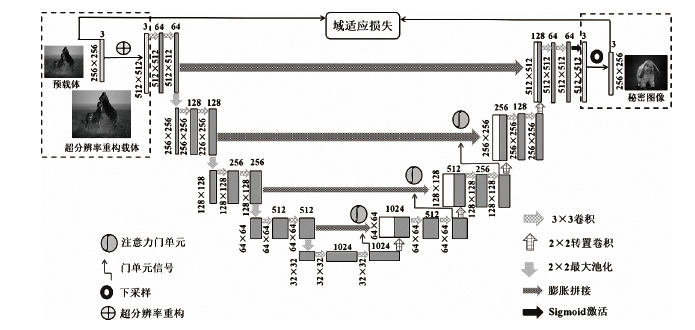
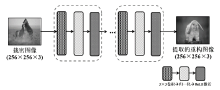
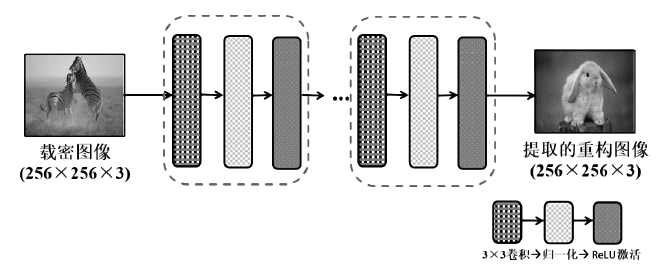
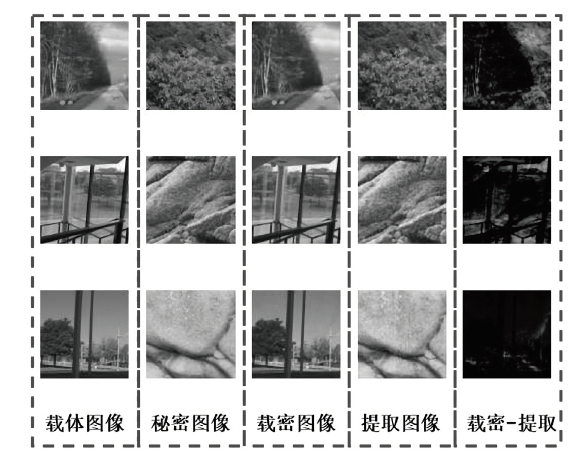
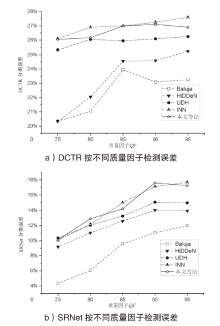
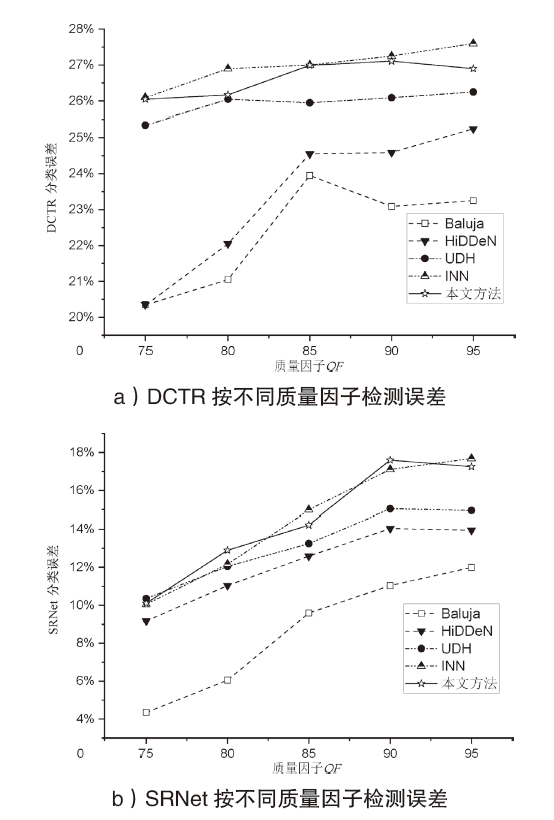
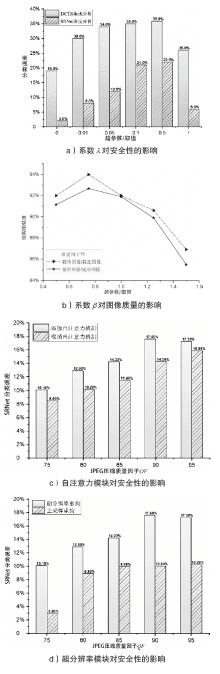
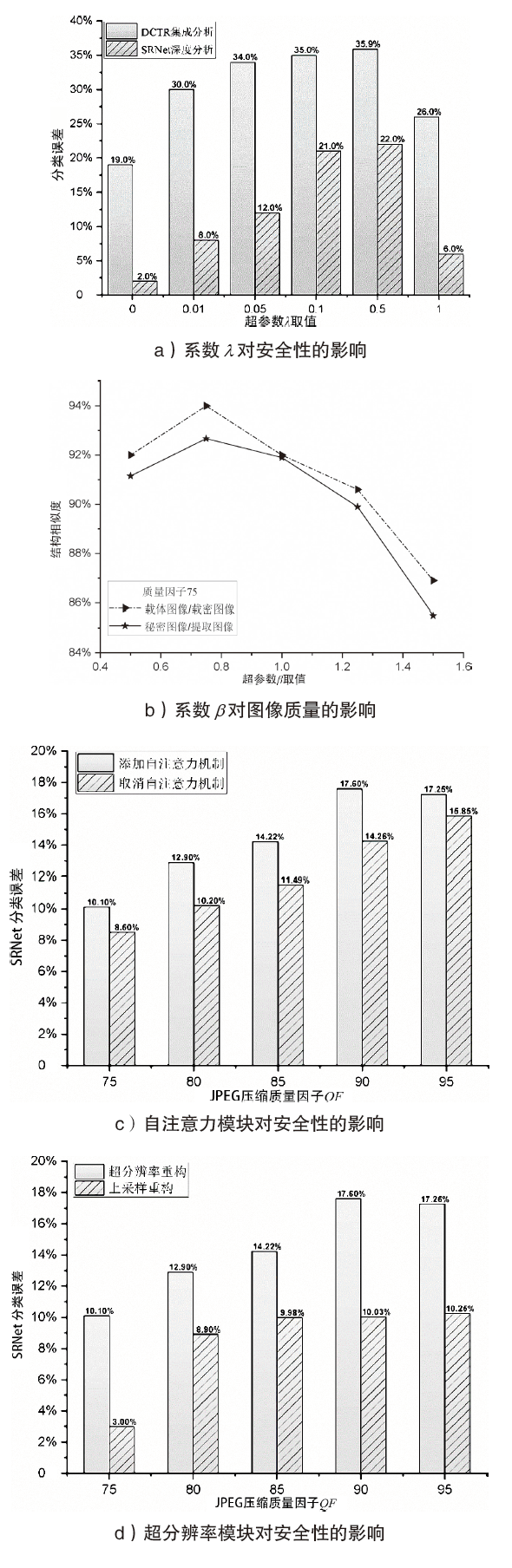
| [1] |
YU Kunliang, CHEN Liquan, WANG Yu, et al. A Channel Coding Information Hiding Algorithm for Images Based on Uniform Cyclic Shift[J]. Multimedia Tools and Applications, 2022, 81(8): 11279-11300.
doi: 10.1007/s11042-022-12034-8
URL
|
| [2] |
LIN C C, CHANG C C, KAO W J, et al. Efficient Electronic Patient Information Hiding Scheme with Tamper Detection Function for Medical Images[J]. IEEE Access, 2022(10): 18470-18485.
|
| [3] |
PAN Feng, LI Jun, YANG Xiaoyuan. Image Steganography Method Based on PVD and Modulus Function[C]// IEEE. 2011 International Conference on Electronics, Communications and Control (ICECC). New York: IEEE, 2011: 282-284.
|
| [4] |
MIELIKAINEN J. LSB Matching Revisited[J]. IEEE Signal Processing Letters, 2006, 13(5): 285-287.
doi: 10.1109/LSP.2006.870357
URL
|
| [5] |
COX I J, MILLER M L, BLOOM J A, et al. Digital Watermarking and Steganography[J]. Morgan Kaufmann, 2008, 11: 61-103.
|
| [6] |
FILLER T, JUDAS J, FRIDRICH J. Minimizing Additive Distortion in Steganography Using Syndrome-Trellis Codes[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(3): 920-935.
doi: 10.1109/TIFS.2011.2134094
URL
|
| [7] |
VOLKHONSKIY D, BORISENKO B, BURNAEV E. Generative Adversarial Networks for Image Steganography[EB/OL]. (2016-11-05)[2022-09-10]. https://openreview.net/pdf?id=H1hoFU9xe.htm.
|
| [8] |
TANG Weixuan, LI Bin, TAN Shuquan, et al. CNN-based adversarial embedding for image steganography[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(8): 2074-2087.
doi: 10.1109/TIFS.2019.2891237
URL
|
| [9] |
SHI Haichao, DONG Jing, WANG Wei, et al. Ssgan: Secure Steganography Based on Generative Adversarial Networks[C]// Springer. In Pacific Rim Conference on Multimedia. Berlin: Springer, 2017: 534-544.
|
| [10] |
NGUYEN B C, YOON S M, LEE H-K. Multi Bit Plane Image Steganography[C]// Springer. International Workshop on Digital Watermarking. Berlin:Springer, 2006: 61-70.
|
| [11] |
HETAL S, MUTZEL P. A Graph-Theoretic Approach to Steganography[C]// Springer. IFIP International Conference on Communications and Multimedia Security. Berlin:Springer, 2005: 119-128.
|
| [12] |
PEVNY T, FILLER T, BAS P. Using High-Dimensional Image Models to Perform Highly Undetectable Steganography[C]// Springer. In International Workshop on Information Hiding. Berlin:Springer, 2010: 161-177.
|
| [13] |
HOLUB V, FRIDRICH J. Designing Steganographic Distortion Using Directional Filters[C]// IEEE. 2012 IEEE International Workshop on Information Forensics and Security (WIFS). New York:IEEE, 2012: 234-239.
|
| [14] |
HOLUB V, FRIDRICH J, DENEMARK T. Universal Distortion Function for Steganography in an Arbitrary Domain[J]. EURASIP Journal on Information Security, 2014(1): 1-13.
|
| [15] |
LI Bin, WANG Ming, HUANG Jiwu, et al. A New Cost Function for Spatial Image Steganography[C]// IEEE. 2014 IEEE International Conference on Image Processing (ICIP). New York:IEEE, 2014: 4206-4210.
|
| [16] |
PEVNY T, BAS P, FRIDRICH J. Steganalysis by Subtractive Pixel Adjacency Matrix[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(2): 215-224.
doi: 10.1109/TIFS.2010.2045842
URL
|
| [17] |
GOODFELLOW L J, POUGET-A J, MIRZA M, et al. Generative Adversarial Nets. Advances in Neural Information Processing Systems[C]// ACM. Proceedings of the 27th International Conference on Neural Information Processing Systems. New York: ACM, 2014: 2672-2680.
|
| [18] |
RADFORD A, METZ L, CHINTALA S. Unsupervised Representation Learning with Deep Convolutional Generative Adversarial Networks[EB/OL]. (2016-01-07)[2022-09-10]. https://arxiv.org/abs/1511.06434.htm.
|
| [19] |
LIU Mingming, ZHANG Minqing, LIU Jia, et al. Coverless Information Hiding Based on Generative Adversarial Networks[J]. Journal of Applied Sciences, 2018, 36(2): 371-382.
|
|
刘明明, 张敏情, 刘佳, 等. 基于生成对抗网络的无载体信息隐藏[J]. 应用科学学报, 2018, 36(2): 371-382.
|
| [20] |
BI Xinliang, YANG Haibin, YANG Xiaoyuan, et al. Generative Strganography Scheme Based on StarGAN[J]. Netinfo Security, 2020, 20(12): 64-71.
|
|
毕新亮, 杨海滨, 杨晓元, 等. 基于StarGAN的生成式图像隐写方案[J]. 信息网络安全, 2020, 20(12): 64-71.
|
| [21] |
LIN Zhouhan, FENG Minwei, SANTOS C N, et al. A Structured Self-Attentive Sentence Embedding[J]. arXiv preprint arXiv, 2017, 3(9): 1-15.
|
| [22] |
ZHANG X, KONG X, WANG P, et al. Cover-Source Mismatch in Deep Spatial Steganalysis[C]//Springer. International Workshop on Digital Watermarking. Berlin:Springer, 2019: 71-83.
|
| [23] |
DASTGHEIB M B, JAHROMI M F, NEJAD J T. A Low Cost Image Steganalysis by Using Domain Adaptation[J]. International Journal of Information Science and Management (IJISM), 2018, 16(1): 191-201.
|
| [24] |
YANG Yong, KONG Xiangwei, WANG Bo, et al. Steganalysis on Internet Images Via Domain Adaptive Classifier[J]. Neurocomputing, 2019, 351: 205-216.
doi: 10.1016/j.neucom.2019.04.025
|
| [25] |
WANG Yaojie, YANG Xiaoyuan, LIU jia. Cross-Domain Image Steganography Based on GANs[C]// Springer. International Conference on Security with Intelligent Computing and Big-data Services. Berlin:Springer, 2018: 743-755.
|
| [26] |
GABRIEL G. NinaSR: Efficient Small and Large ConvNets for Super-Resolution. GitHub repository[EB/OL]. (2021-08-21)[2022-09-10]. https://github.com/Coloquinte/torchSR.
|
| [27] |
DUAN Xintao, LIU Nao, GOU Mengxiao, et al. SteganoCNN: Image Steganography with Generalization Ability Based on Convolutional Neural Network[J]. Entropy, 2020, 22(10): 1155.
doi: 10.3390/e22101155
URL
|
| [28] |
BOROUMAND M, CHEN Mo, FRIDRICH J. Deep Residual Network for Steganalysis of Digital Images[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(5): 1181-1193.
doi: 10.1109/TIFS.2018.2871749
URL
|
| [29] |
BALUJA S. Hiding Images within Images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2020, 42(7): 1685-1697.
doi: 10.1109/TPAMI.2019.2901877
pmid: 30835212
|
| [30] |
ZHU Jiren, KAPLAN R, JOHNSON J, et al. Hidden: Hiding Data with Deep Networks[C]// Springer. European Conference on Computer Vision (ECCV). Berlin: Springer, 2018: 682-697.
|
| [31] |
ZHANG Chaoning, BENZ P, KARJAUV A, et al. UDH: Universal Deep Hiding for Steganography, Watermarking, and Light Field Messaging[J]. Advances in Neural Information Processing Systems, 2020, 33: 10223-10234.
|
| [32] |
LU Shaoping, WANG Rong, ZHANG Tao, et al. Large-Capacity Image Steganography Based on Invertible Neural Networks[C]// IEEE. IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 10816-10825.
|
| [33] |
HOLUB V, FRIDRICH J. Low-Complexity Features for JPEG Steganalysis Using Undecimated DCT[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(2): 219-228.
|
 ), ZHANG Yubin3
), ZHANG Yubin3