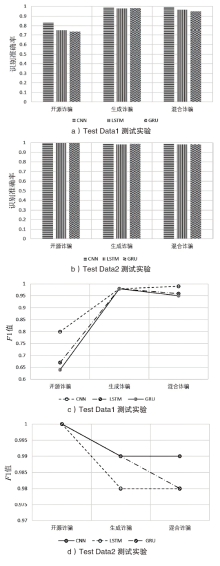
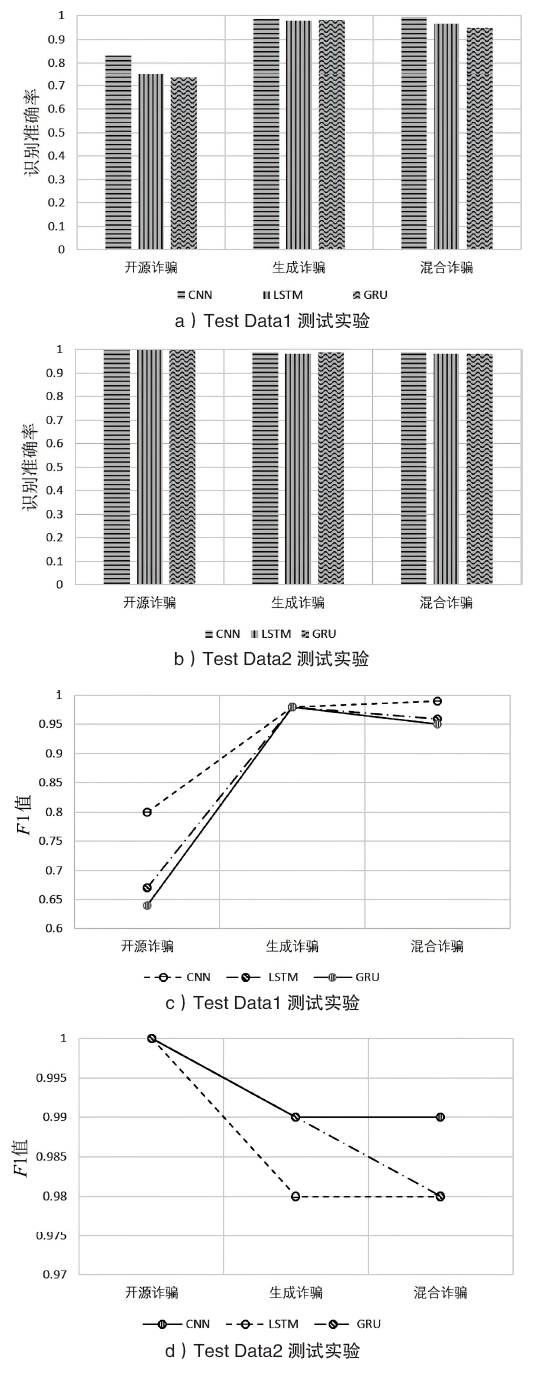
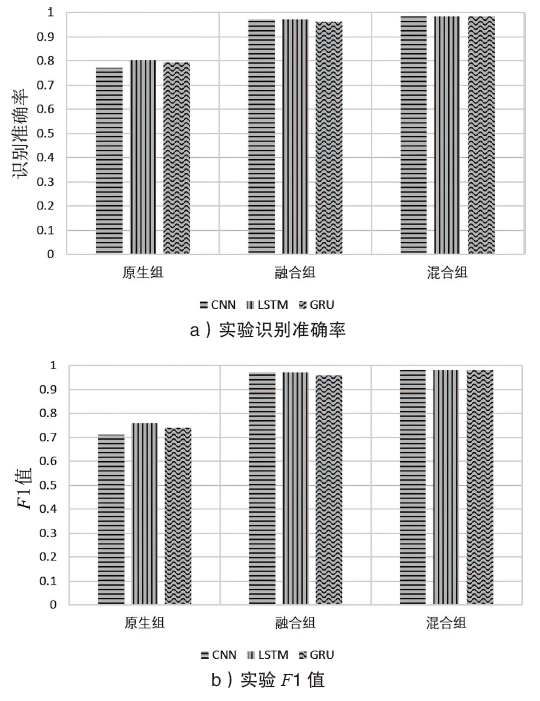
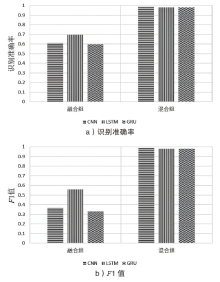
| [1] |
MA Zhonghong. Research on the Difficulties and Countermeasures of New Network Crime Investigation Represented by Telecommunication Fraud Based on the Investigation of W Province[J]. Journal of People's Public Security University of China (Social Sciences Edition), 2018, 34(3): 78-86.
|
|
马忠红. 以电信诈骗为代表的新型网络犯罪侦查难点及对策研究——基于W省的调研情况[J]. 中国人民公安大学学报(社会科学版), 2018, 34(3): 78-86.
|
| [2] |
JOO J W, MOON S Y, SINGH S, et al. S-Detector: An Enhanced Security Model for Detecting Smishing Attack for Mobile Computing[J]. Telecommunication Systems, 2017, 66(1): 29-38.
|
| [3] |
FARVARESH H, SEPEHRI M. A Data Mining Framework for Detecting Subscription Fraud in Telecommunication[J]. Engineering Applications of Artificial Intelligence, 2011, 24(1): 182-194.
|
| [4] |
YANG Jiechao, XU Jiangchun, YUE Qiuyan, et al. Research on SMS Fraud User Identification Based on SPARK and Random Forest[J]. Computer Engineering and Science, 2019, 41 (6): 1136-1144.
|
|
杨杰超, 许江淳, 岳秋燕, 等. 基于SPARK与随机森林的短信诈骗用户识别研究[J]. 计算机工程与科学, 2019, 41(6): 1136-1144.
|
| [5] |
WANG Shihao, CAI Yanguang. A Fraud Identification Method for Telecom Customers Based on Improved GA-SVM[J]. Journal of Dongguan Institute of Technology, 2019, 26 (5): 14-20
|
|
王世豪, 蔡延光. 基于改进GA-SVM的电信客户欺诈识别方法[J]. 东莞理工学院学报, 2019, 26(5):14-20
|
| [6] |
JIANG Nan. Securing Large Cellular Networks via a Data Oriented Approach: Applications to SMS Spam and Voice Fraud Defenses[D]. Minnesota: University of Minnesota, 2013.
|
| [7] |
BOUKERCHE A, Notare M. Behavior-Based Intrusion Detection in Mobile Phone Systems[J]. Journal of Parallel and Distributed Computing. 2002, 62, (9): 1476-1490.
|
| [8] |
DONG Lin, HUANG Liqing, YE Feng, et al. Overview of Generalized Methods for Face Forgery Detection[J]. Computer Science, 2022, 49 (2): 12-30.
|
|
董琳, 黄丽清, 叶锋, 等. 人脸伪造检测泛化性方法综述[J]. 计算机科学, 2022, 49(2): 12-30.
|
| [9] |
LAN Tian, PENG Chuan, LI Sen, et al. Overview of Mono Speech Noise Reduction and Reverberation[J]. Computer Research and Development, 2020, 57 (5): 928-953.
|
|
蓝天, 彭川, 李森, 等. 单声道语音降噪与去混响研究综述[J]. 计算机研究与发展, 2020, 57(5): 928-953.
|
| [10] |
CHENG Haoyi, LI Peifeng, ZHU Qiaoming. A Method of Event Anaphora Resolution Based on Cross Language Data Enhancement[J]. Journal of Chinese Information Science, 2022, 36 (3): 19-26
|
|
程昊熠, 李培峰, 朱巧明. 基于跨语言数据增强的事件同指消解方法[J]. 中文信息学报, 2022, 36(3): 19-26.
|
| [11] |
XU Huiyan, WU Keli, SUN Qingying, et al. Template-Based SMS Platform[J]. Computer System Application, 2015, 24 (5): 79-83.
|
|
徐会艳, 吴克力, 孙庆英, 等. 基于模板的短信平台[J]. 计算机系统应用, 2015, 24(5): 79-83.
|
| [12] |
LI Ping. Research on Several Issues of Criminal Cases Related to COVID-19[J]. Criminal Law, 2020, 64 (4): 22-38.
|
|
李萍. 涉新冠疫情犯罪案件若干问题研究[J]. 刑法论丛, 2020, 64(4): 22-38.
|
| [13] |
TONG Xin, WANG Luona, WANG Runzheng, et al. A Method for Generating Word Level Confrontation Samples for Chinese Text Classification[J]. Netinfo Security, 2020, 20 (9): 12-16.
|
|
仝鑫, 王罗娜, 王润正, 等. 面向中文文本分类的词级对抗样本生成方法[J]. 信息网络安全, 2020, 20(9): 12-16.
|
| [14] |
QIAN Lingfei, CUI Xiaolei. Research on the Construction Method of Domain Knowledge Map Based on Data Enhancement[J]. Modern Intelligence, 2022, 42 (3): 31-39.
|
|
钱玲飞, 崔晓蕾. 基于数据增强的领域知识图谱构建方法研究[J]. 现代情报, 2022, 42(3): 31-39.
|
| [15] |
XIAN Yantuan, GAO Fanya, XIANG Yan, et al. A Low Resource Dependency Syntax Analysis Method with Multi Strategy Data Enhancement[J]. Computer Science, 2022, 49 (1): 73-79.
|
|
线岩团, 高凡雅, 相艳, 等. 融合多策略数据增强的低资源依存句法分析方法[J]. 计算机科学, 2022, 49(1): 73-79.
|
 ), LI Mingfeng1, SUN Haichun1
), LI Mingfeng1, SUN Haichun1