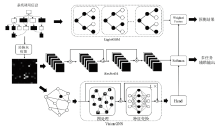
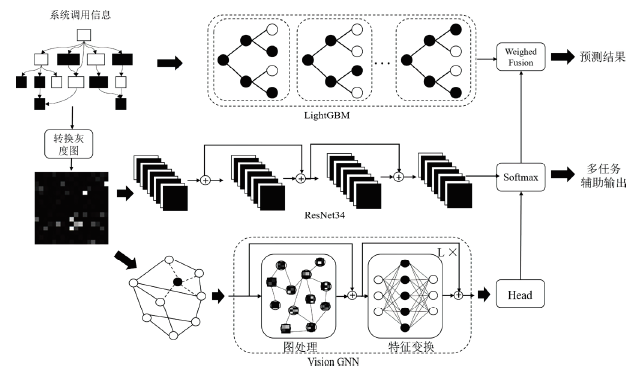
| [1] |
JIN Bo, WU Songyang, XIONG Xiong, et al. Research on Digital Forensics of Smart Devices[J]. Journal of Cyber Security, 2016, 1(3): 37-51.
|
|
金波, 吴松洋, 熊雄, 等. 新型智能终端取证技术研究[J]. 信息安全学报, 2016, 1(3): 37-51.
|
| [2] |
ENCK W, ONGTANG M, MCDANIEL P. On Lightweight Mobile Phone Application Certification[C]// ACM.Proceedings of the 16th ACM Conference on Computer and Communications Security. New York Illinois: ACM, 2009: 235-245.
|
| [3] |
ENCK W, GILBERT P, HAN S, et al. Taintdroid: An information-Flow Tracking System for Realtime Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems (TOCS), 2014, 32(2): 1-29.
|
| [4] |
ARZT S, RASTHOFER S, FRITZ C, et al. Flowdroid: Precise Context, Flow, Field, Object-Sensitive and Lifecycle-Aware Taint Analysis for android Apps[J]. Acm Sigplan Notices, 2014, 49(6): 259-269.
|
| [5] |
ZHANG Chaoqin, HU Guangwu, WANG Zhenlong, et al. A Novel SVM-Based Detection Method for Android Malware[J]. Computer Applications and Software, 2018, 35(10): 292-298.
|
|
张超钦, 胡光武, 王振龙, 等. 一种基于支持向量机的安卓恶意软件新型检测方法[J]. 计算机应用与软件, 2018, 35(10): 292-298.
|
| [6] |
QU Jun, GU Liujun. Research on Android Malware Detection Based on Naive Bayes[J]. Netinfo Security, 2020(S1): 27-30.
|
|
瞿俊, 顾刘军. 基于朴素贝叶斯的安卓恶意软件检测研究[J]. 信息网络安全, 2020(S1): 27-30.
|
| [7] |
LI Jianghua, QIU Chen. Android Malware Detection Method Based on Meta-Information[J]. Application Research of Computers, 2019, 36(10): 3058-3062.
|
|
李江华, 邱晨. 一种基于元信息的Android恶意软件检测方法[J]. 计算机应用研究, 2019, 36(10): 3058-3062.
|
| [8] |
ZHU Huijuan, JIANG Tonghai, MA Bo, et al. HEMD: A Highly Efficient Random Forest-Based Malware Detection Framework for Android[J]. Neural Computing and Applications, 2018, 30(11): 3353-3361.
|
| [9] |
XIONG Jian, QIN Renchao, HE Mengyi, et al. Application of Improved Random Forest Algorithm in Android Malware Detection[J]. Computer Engineering and Applications, 2021, 57(3): 130-136.
|
|
熊健, 覃仁超, 何梦乙, 等. 改进随机森林在Android恶意软件检测中的应用[J]. 计算机工程与应用, 2021, 57(3): 130-136.
|
| [10] |
ZHAO Yuxin, NURBOL, AI Zhuang. Android Malware Detection Based on Ensemble Learning Voting Algorithm[J]. Computer Engineering and Applications, 2020, 56(22): 74-82.
|
|
赵宇鑫, 努尔布力, 艾壮. 基于集成学习投票算法的Android恶意应用检测[J]. 计算机工程与应用, 2020, 56(22): 74-82.
|
| [11] |
GAO Yangchen, FANG Yong, LIU Liang, et al. Android Malware Detection Technology Based on Deep Convolutional Neural Network[J]. Journal of Sichuan University (Natural Science Edition), 2020, 57(4): 673-680.
|
|
高杨晨, 方勇, 刘亮, 等. 基于卷积神经网络的Android恶意软件检测技术研究[J]. 四川大学学报(自然科学版), 2020, 57(4): 673-680.
|
| [12] |
VINAYAKUMAR R, SOMAN K P, POORNACHANDRAN P, et al. Detecting Android Malware Using Long Short-Term Memory (LSTM)[J]. Journal of Intelligent & Fuzzy Systems, 2018, 34(3): 1277-1288.
|
| [13] |
YUE Ziwei, FANG Yong, ZHANG Lei. Android Malware Detection Based on Graph Attention Networks[J]. Journal of Sichuan University (Natural Science Edition), 2022, 59(5): 88-95.
|
|
岳子巍, 方勇, 张磊. 基于图注意力网络的安卓恶意软件检测[J]. 四川大学学报(自然科学版), 2022, 59(5): 88-95.
|
| [14] |
WANG Wei, ZHAO Mengxue, WANG Jigang. Effective Android Malware Detection with a Hybrid Model Based on Deep Autoencoder and Convolutional Neural Network[J]. Journal of Ambient Intelligence and Humanized Computing, 2019, 10(8): 3035-3043.
|
| [15] |
RENJITH G, LAUDANNA S, AJI S, et al. GANG-MAM: GAN Based enGine for Modifying Android Malware[EB/OL]. (2022-02-17)[2022-07-06]. https://www.softxjournal.com/article/S2352-7110(22)00003-6/fulltext.
|
| [16] |
HAN Kai, WANG Yunhe, GUO Jianyuan, et al. Vision GNN: An Image is Worth Graph of Nodes[EB/OL]. (2022-07-05)[2022-09-03]. https://arxiv.org/abs/2206.00272.
|
| [17] |
HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE.Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778.
|
| [18] |
KE Guolin, MENG Qi, FINLEY T, et al. LightGBM: A Highly Efficient Gradient Boosting Decision Tree[C]// NIPS. Proceedings of the 31st International Conference on Neural Information Processing Systems. West Chester: Curran Associates, 2017: 3147-3155.
|
| [19] |
MAHDAVIFAR S, ALHADIDI D, GHORBANi A. Effective and Efficient Hybrid Android Malware Classification Using Pseudo-Label Stacked Auto-Encoder[J]. Journal of Network and Systems Management, 2022, 30(1): 1-34.
|
| [20] |
DOSOVITSKIY A, BEYER L, KOLESNIKOV A, et al. An Image is Worth 16x16 Words: Transformers for Image Recognition at Scale[EB/OL]. (2021-06-03)[2022-07-06]. https://arxiv.org/abs/2010.11929.
|
| [21] |
SIMONYAN K, ZISSERMAN A. Very Deep Convolutional Networks for Large-Scale Image Recognition[EB/OL]. (2015-04-10) [2022-07-06]. https://arxiv.org/abs/1409.1556.
|
| [22] |
HUANG Gao, LIU Zhuang, MAATEN L, et al. Densely Connected Convolutional Networks[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2017: 4700-4708.
|
| [23] |
SANDLER M, HOWARD A, ZHU M, et al. Mobilenetv2: Inverted Residuals and Linear Bottlenecks[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE Computer Society, 2018: 4510-4520.
|
| [24] |
ZHANG Xiangyu, ZHOU Xinyu, LIN Mengxiao, et al. Shufflenet: An Extremely Efficient Convolutional Neural Network for Mobile Devices[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 6848-6856.
|
| [25] |
XIE Saining, GIRSHICK R, DOLLÁR P, et al. Aggregated Residual Transformations for Deep Neural Networks[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2017: 1492-1500.
|
| [26] |
LI Heng, ZHOU Shiyao, YUAN Wei, et al. Adversarial-Example Attacks toward Android Malware Detection System[J]. IEEE Systems Journal, 2019, 14(1): 653-656.
|
| [27] |
ZHI Yongbo, XI Ning, LIU Yuanqing, et al. A Lightweight Android Malware Detection Framework Based on Knowledge Distillation[C]// Springer. International Conference on Network and System Security. Berlin:Springer, 2021: 116-130.
|
 ), WANG Jingya1, YANG Ying2
), WANG Jingya1, YANG Ying2