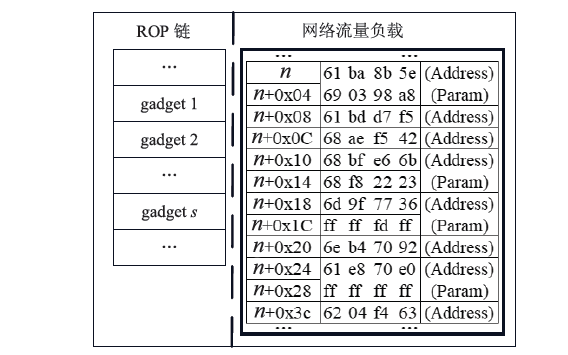
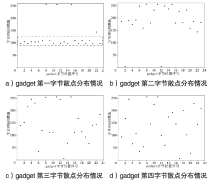
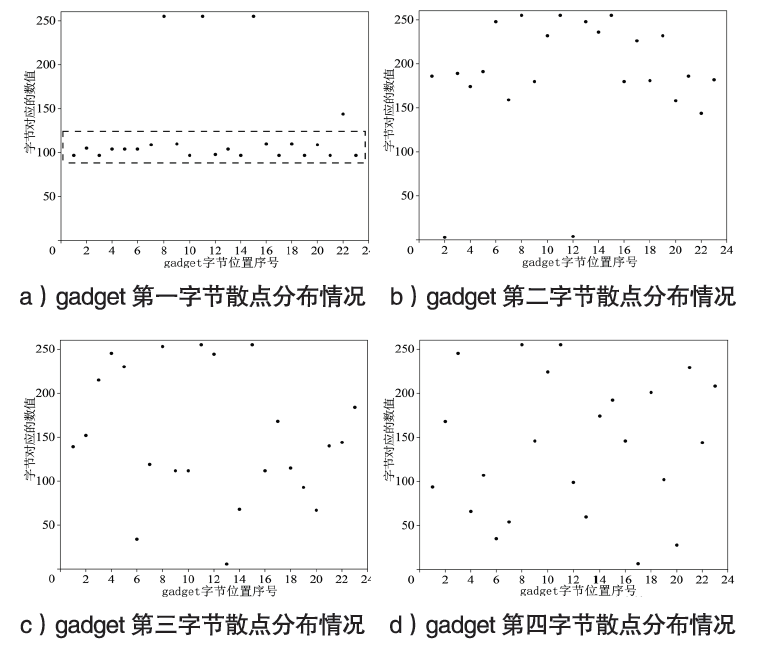
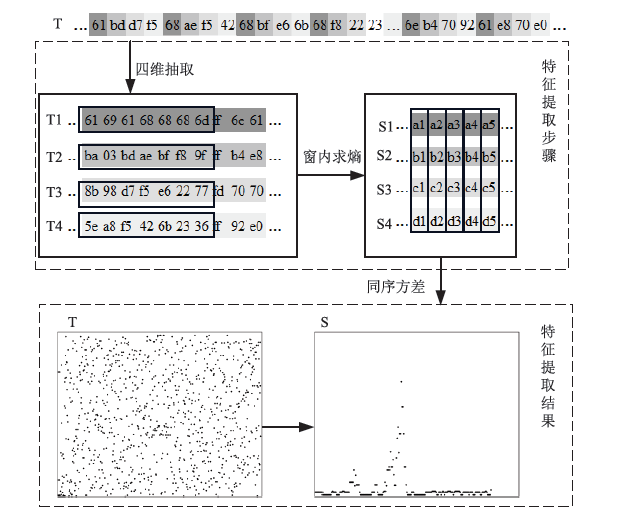
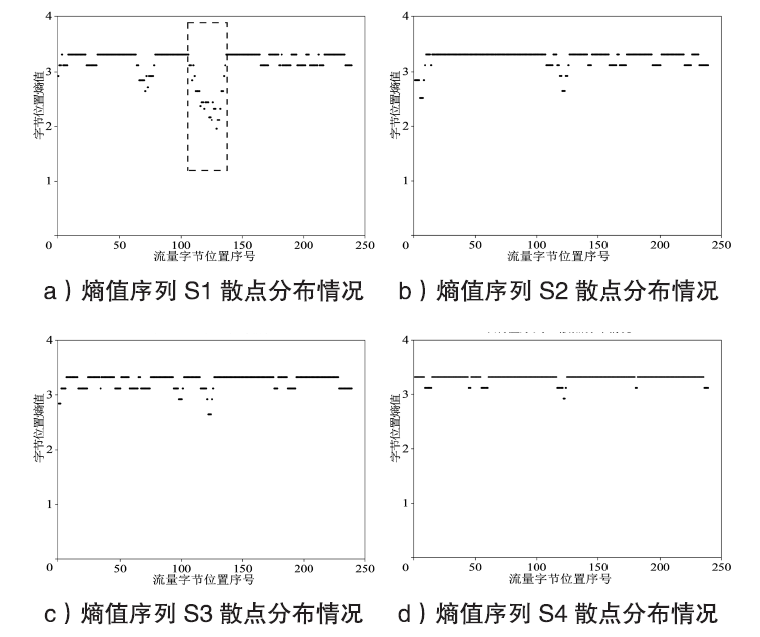
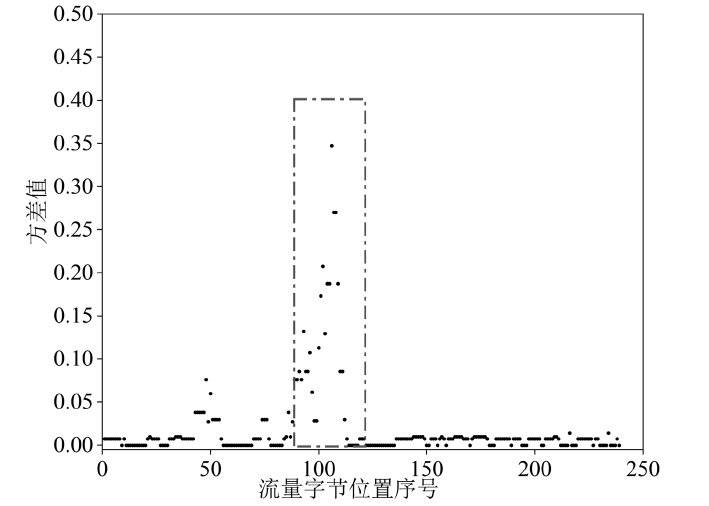
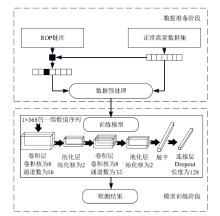
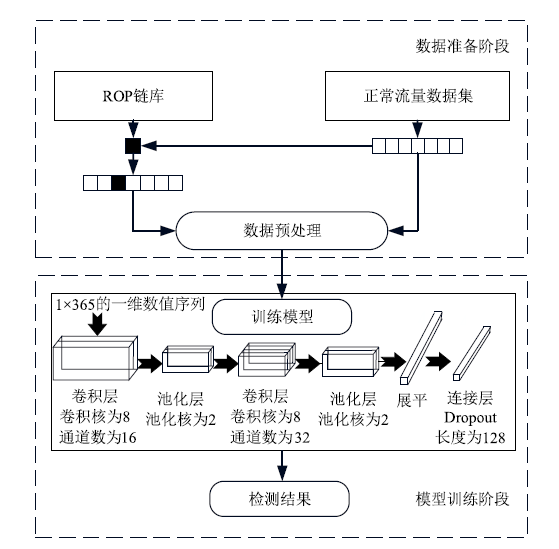
| [1] |
ANDERSEN S. Changes to Functionality in Microsoft Windows XP Service Pack 2: Part 3: Memory Protection Technologies[EB/OL]. (2004-11-04)[2021-12-22]. https://oriolrius.cat/article_fitxers/1901/winsock2.pdf.
|
| [2] |
BLETSCH T, JIANG Xuxian, FREEH V W, et al. Jump-Oriented Programming: A New Class of Code-Reuse Attack[C]// ACM. 6th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2011: 30-40.
|
| [3] |
CHECKOWAY S, DAVI L, DMITRIENKO A, et al. Return-Oriented Programming without Returns[C]// ACM. 17th ACM Conference on Computer and Communications Security. New York: ACM, 2010: 559-572.
|
| [4] |
ROEMER R, BUCHANAN E, SHACHAM H, et al. Return-Oriented Programming: Systems, Languages, and Applications[J]. ACM Transactions on Information and System Security (TISSEC), 2012, 15(1): 1-34.
|
| [5] |
SNOW K Z, MONROSE F, DAVI L, et al. Just-in-Time Code Reuse: on the Effectiveness of Fine-Grained Address Space Layout Randomization[C]// IEEE. 2013 IEEE Symposium on Security and Privacy. New York: IEEE, 2013: 574-588.
|
| [6] |
CHEN Ping, XIAO Hai, SHEN Xiaobin, et al. DROP: Detecting Return-Oriented Programming Malicious Code[C]// Springer. International Conference on Information Systems Security. Heidelberg: Springer, 2009: 163-177.
|
| [7] |
PAPPAS V, POLYCHRONAKIS M, KEROMYTIS A D. Transparent ROP Exploit Mitigation Using Indirect Branch Tracing[C]// USENIX. 22nd USENIX Security Symposium. Berkeley: USENIX, 2013: 447-462.
|
| [8] |
CHENG Yueqiang, ZHOU Zongwei, MIAO Yu, et al. ROPecker: A Generic and Practical Approach for Defending against ROP Attack[EB/OL]. (2014-02-23)[2021-11-26]. https://ink.library.smu.edu.sg/cgi/viewcontent.cgi?article=2972&context=sis_research.
|
| [9] |
ELSABAGH M, BARBARA D, FLECK D, et al. Detecting ROP with Statistical Learning of Program Characteristics[C]// ACM. 7th ACM on Conference on Data and Application Security and Privacy. New York: ACM, 2017: 219-226.
|
| [10] |
PFAFF D, HACK S, HAMMER C. Learning How to Prevent Return-Oriented Programming Efficiently[C]// Springer. International Symposium on Engineering Secure Software and Systems. Heidelberg: Springer, 2015: 68-85.
|
| [11] |
POLYCHRONAKIS M, KEROMYTIS A D. ROP Payload Detection Using Speculative Code Execution[C]// IEEE. 2011 6th International Conference on Malicious and Unwanted Software. New York: IEEE, 2011: 58-65.
|
| [12] |
USUI T, IKUSE T, OTSUKI Y, et al. ROPminer: Learning-Based Static Detection of ROP Chain Considering Linkability of ROP Gadgets[J]. IEICE Transactions on Information and Systems, 2020, 103(7): 1476-1492.
|
| [13] |
JÄMTHAGEN C, KARLSSON L, STANKOVSKI P, et al. EavesROP: Listening for ROP Payloads in Data Streams[C]// Springer. International Conference on Information Security. Heidelberg: Springer, 2014: 413-424.
|
| [14] |
TANAKA Y, GOTO A. N-ROPdetector: Proposal of a Method to Detect the ROP Attack Code on the Network[C]// ACM. 2014 Workshop on Cyber Security Analytics, Intelligence and Automation. New York: ACM, 2014: 33-36.
|
| [15] |
STANCILL B, SNOW K Z, OTTERNESS N, et al. Check My Profile: Leveraging Static Analysis for Fast and Accurate Detection of ROP Gadgets[C]// Springer. International Workshop on Recent Advances in Intrusion Detection. Heidelberg: Springer, 2013: 62-81.
|
| [16] |
LI Xusheng, HU Zhisheng, WANG Haizhou, et al. DeepReturn: A Deep Neural Network Can Learn How to Detect Previously-Unseen ROP Payloads without Using Any Heuristics[J]. Journal of Computer Security, 2020, 28(5): 499-523.
doi: 10.3233/JCS-191368
URL
|
| [17] |
RONG Zelin, XIE Peidai, WANG Jingyuan, et al. Clean the Scratch Registers: A Way to Mitigate Return-Oriented Programming Attacks[C]// IEEE. 2018 IEEE 29th International Conference on Application-Specific Systems, Architectures and Processors (ASAP). New York: IEEE, 2018: 1-8.
|
| [18] |
WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717.
|
 ), HUANG Kaijie, YANG Gang
), HUANG Kaijie, YANG Gang