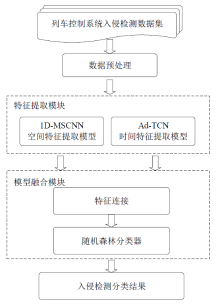
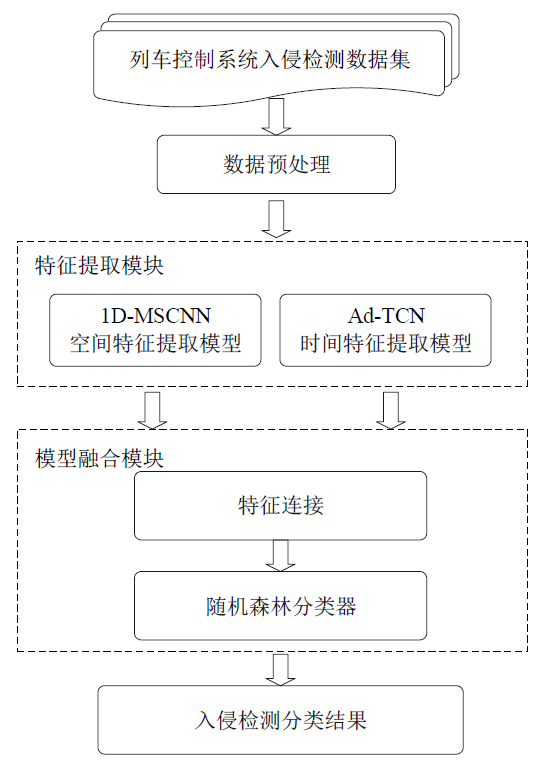
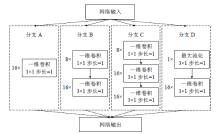
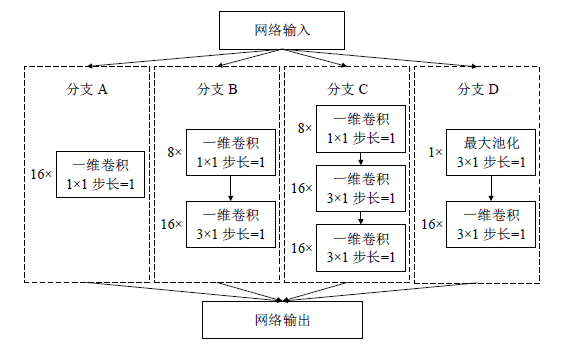
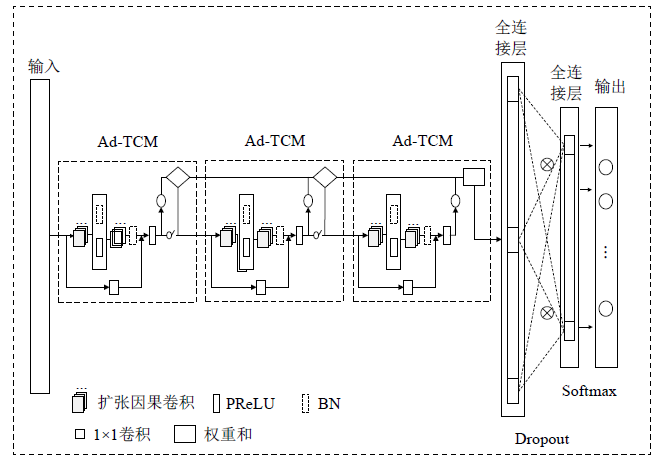
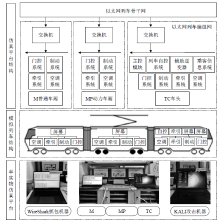
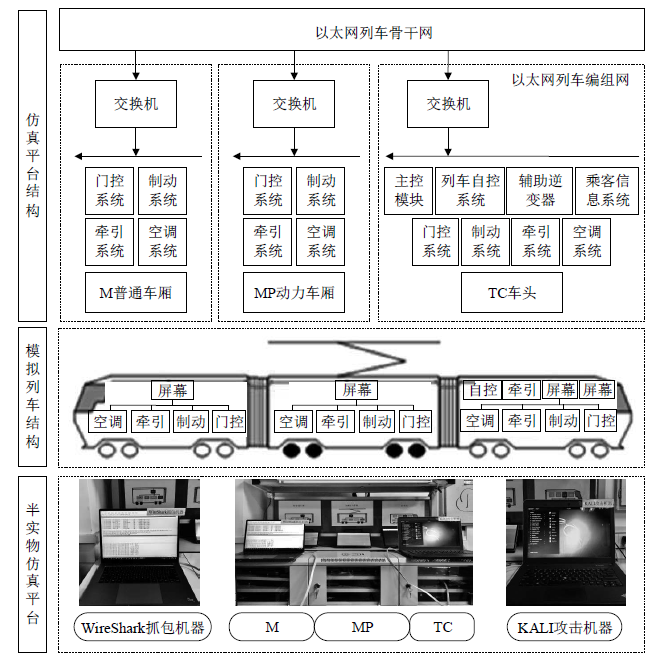
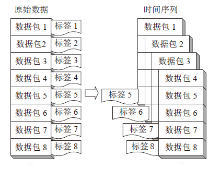
| [1] |
KIRRMANN H, ZUBER P A. The IEC/IEEE Train Communication Network[J]. IEEE Micro, 2001, 21(2): 81-92.
doi: 10.1109/40.918005
URL
|
| [2] |
LI Siyuan, ZOU Yuchi, YANG Manli. Research on Information Security Protection of Train Network Based on Real-Time Ethernet[J]. China New Telecommunication, 2021(7): 127-128.
|
|
李思源, 邹宇驰, 杨曼莉. 基于实时以太网的列车网络信息安全防护研究[J]. 中国新通信, 2021(7):127-128.
|
| [3] |
ANDERSON J P. Computer Security Threat Monitoring and Surveillance[EB/OL]. [2022-01-12]. https://www.mendeley.com/catalogue/0616cddb-7cb8-3132-85b2-aafd0deef6d5/.
|
| [4] |
TU Hao. Design and Implementation of Intrusion Detection System for Train Communication Network[D]. Wuhan: Huazhong University of Science and Technology, 2020.
|
|
涂浩. 列车通信网络入侵检测系统的设计和实现[D]. 武汉: 华中科技大学, 2020.
|
| [5] |
WU Jiajie, WU Shaoling, WANG Wei. An Anomaly Delection and Location Algorithm Based on TCN and Attention Mechanism[J]. Netinfo Security, 2021, 21(11): 85-94.
|
|
吴佳洁, 吴绍岭, 王伟. 基于TCN和注意力机制的异常检测和定位算法[J]. 信息网络安全, 2021, 21(11):85-94.
|
| [6] |
GAO Bing, BU Bing. A Novel Intrusion Detection Method in Train-Ground Communication System[J]. IEEE Access, 2019, 7: 178726-178743.
doi: 10.1109/ACCESS.2019.2958198
|
| [7] |
SONG Yajie, BU Bing, ZHU Li. A Novel Intrusion Detection Model Using a Fusion of Network and Device States for Communication-Based Train Control Systems[EB/OL]. (2020-01-18) [2021-12-22]. https://doi.org/10.3390/electronics9010181.
|
| [8] |
SAXENA S, VERBEEK J. Convolutional Neural Fabrics[EB/OL]. [2022-01-12]. https://proceedings.neurips.cc/paper/2016/hash/07811dc6c422334ce36a09ff5cd6fe71-Abstract.html.
|
| [9] |
BISWAS P, SAMANTA T. Anomaly Detection Using Ensemble Random Forest in Wireless Sensor Network[J]. International Journal of Information Technology, 2021, 13(5): 2043-2052.
doi: 10.1007/s41870-021-00717-8
URL
|
| [10] |
GRAVES A. Adaptive Computation Time for Recurrent Neural Networks[EB/OL]. [2022-01-22]. https://ui.adsabs.harvard.edu/abs/2016arXiv160308983G/abstract.
|
| [11] |
HUANG Jinchao, MA Yinghua, QI Kaiyue, et al. An Ensemble-Based Instrusion Detection Algorithm[J]. Journal of Shanghai Jiaotong University, 2018, 52(10): 1382-1387.
|
|
黄金超, 马颖华, 齐开悦, 等. 一种基于集成学习的入侵检测算法[J]. 上海交通大学学报, 2018, 52(10):1382-1387.
|
| [12] |
LIANG Jie, CHEN Jiahao, ZHANG Xueqin, et al. One-Hot Encoding and Convolutional Neural Network Based Anomaly Detection[J]. Journal of Tsinghua University(Science and Technology), 2019, 59(7): 523-529.
|
| [13] |
CHOONG A C H, LEE N K. Evaluation of Convolutionary Neural Networks Modeling of DNA Sequences Using Ordinal Versus One-Hot Encoding Method[C]// IEEE. 2017 International Conference on Computer and Drone Applications(IConDA). New Jersey: IEEE, 2017: 60-65.
|
| [14] |
LV Xuefeng, XIE Yaobin. An Anomaly Detection Method for Industrial Control Systems via State Transition Graph[J]. Acta Automatica Sinica, 2018, 44(9): 1662-1671.
|
|
吕雪峰, 谢耀滨. 一种基于状态迁移图的工业控制系统异常检测方法[J]. 自动化学报, 2018, 44(9):1662-1671.
|
 )
)