Netinfo Security ›› 2021, Vol. 21 ›› Issue (9): 16-24.doi: 10.3969/j.issn.1671-1122.2021.09.003
Previous Articles Next Articles
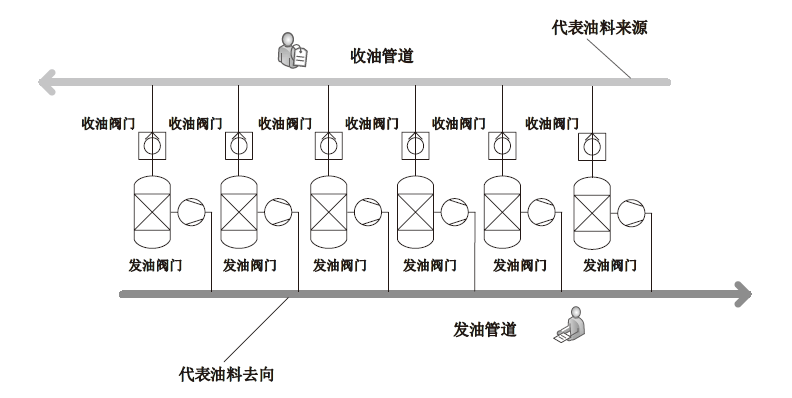
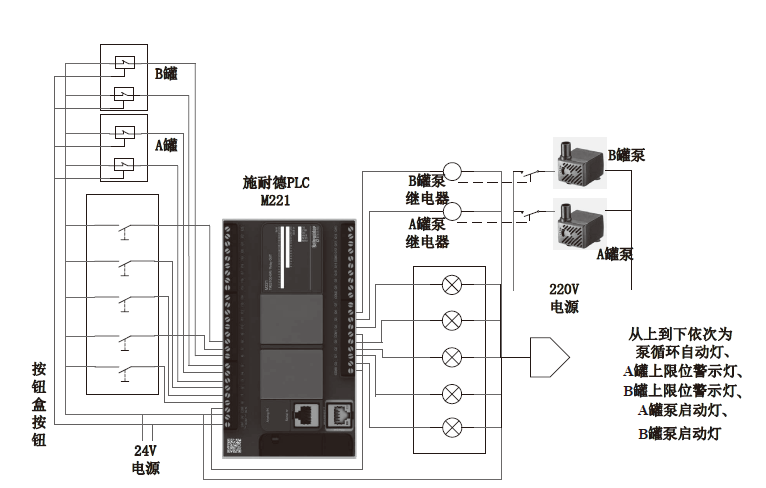
Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object
GU Zhaojun1,2, YAO Feng1,2, DING Lei3, SUI He4( )
)
- 1. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
2. School of Computer Science and Technology, Civil Aviation University of China, Tianjin 300300, China
3. Information Center, Civil Aviation Administration of China, Beijing 100710, China
4. School of Aeronautical Engineering, Civil Aviation University of China, Tianjin 300300, China
-
Received:2021-04-15Online:2021-09-10Published:2021-09-22 -
Contact:SUI He E-mail:hsui@caucedu.cn
CLC Number:
Cite this article
GU Zhaojun, YAO Feng, DING Lei, SUI He. Network Security Test of Airport Fuel Supply Automatic Control System Based on Semi-physical Object[J]. Netinfo Security, 2021, 21(9): 16-24.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.09.003
| [1] | ZHAO Hongyi. Research on the Safety Protection of Modern Enterprise Industrial Control Network[J]. Information Recording Materials, 2020, 21(4): 211-212. |
| 赵弘毅. 现代企业工业控制网络的安全防护探究[J]. 信息记录材料, 2020, 21(4): 211-212. | |
| [2] | GALLOWAY B, HANCKE G P. Introduction to Industrial Control Networks[J]. IEEE Communications Surveys & Tutorials, 2013, 15(2): 860-880. |
| [3] | XIONG Qi, PENG Yong, DAI Zhonghua, et al. Safety Risk Assessment of Industrial Control System[J]. China Information Security, 2012(3): 57-59. |
| 熊琦, 彭勇, 戴忠华, 等. 工业控制系统的安全风险评估[J]. 中国信息安全, 2012(3): 57-59. | |
| [4] |
LIU Huazhong, LAURENCE T Y, CHEN Jinjun, et al. Multivariate Multi-order Markov Multi-modal Prediction with Its Application in Network Traffic Management[J]. IEEE Transactions on Network and Service Management, 2019, 16(3): 828-841.
doi: 10.1109/TNSM.4275028 URL |
| [5] | QU Xiaofei, YANG Lin, GUO Kai, et al. Entropy-defined Direct Batch Growing Hierarchical Self-organizing Mapping for Efficient Network Anomaly Detection[J]. IEEE Access, 2021, 3(99): 38522-38530. |
| [6] |
LIU Hongqing. Quantitative Situational Awareness Algorithm of Land State Network Based on Neutral Statistics[J]. Journal of Ambient Intelligence and Humanized Computing, 2021, 1(3): 1-11.
doi: 10.1007/s12652-010-0009-z URL |
| [7] | NI Zengchao, LIU Hongqi, CHEN Yuanping, et al. Research and Implementation of a Method for Web Log Analysis Template Extraction[J]. Procedia Computer Science, 2019(162): 673-681. |
| [8] |
HE Daojing, QIAO Qi, GAO Jiahao, et al. Simulation Design for Security Testing of Integrated Electronic Systems[J]. IEEE Network, 2020, 34(1): 159-165.
doi: 10.1109/MNET.65 URL |
| [9] | OUYANG Jinsong, DING Lu. Review on IEC62443 Industrial Control Network & System Security Standardization[J]. Information Technology & Standardization, 2012(3): 26-29. |
| 欧阳劲松, 丁露. IEC62443工控网络与系统信息安全标准综述[J]. 信息技术与标准化, 2012(3): 26-29. | |
| [10] | HENG Wenqi. Suggestions for the Development of Cyber Security Services in the Civil Aviation Industry[J]. China Information Security, 2020, 130(10): 50-51. |
| 衡闻琦. 对民航业网络安全服务发展的建议[J]. 中国信息安全, 2020, 130(10): 50-51. | |
| [11] | MA Jun. Design and Application of Automatic Control System in Airport Oil Depot[J]. Chemical Enterprise Management, 2021(10): 180-181. |
| 马骏. 自控系统在机场油库中的设计应用[J]. 化工管理, 2021(10): 180-181. | |
| [12] | WU Gaohui, WANG Shengjiang, WANG Fang. Analysis of Abnormal Fuel Supply in Aviation Fuel for an Airport in Recent Ten Years[J]. Journal of Civil Aviation Flight University of China, 2020, 31(2): 24-29. |
| 伍高辉, 王胜江, 王芳. 某机场航空油料十年来供油不正常事件分析[J]. 中国民航飞行学院学报, 2020, 31(2): 24-29. | |
| [13] |
PUDAR S, MANIMARAN G, LIU C C. PENET: A Practical Method and Tool for Integrated Modeling of Security Attacks and Countermeasures[J]. Computers & Security, 2009, 28(8): 754-771.
doi: 10.1016/j.cose.2009.05.007 URL |
| [14] | ZHOU Xiaomin. Design and Implementation of Hardware-in-the-loop Simulation Experiment Platform for Cyber-security of Industrial Control Systems[D]. Wuhan: Huazhong University of Science and Technology, 2015. |
| 周晓敏. 工业控制系统信息安全半实物仿真实验平台设计与实现[D]. 武汉:华中科技大学, 2015. | |
| [15] | TEIXEIRA A, SHAMES I, SANDBERG H, et al. A Secure Control Framework for Resource-limited Adversaries[J]. Automatica, 2015, 10(51): 135-148. |
| [16] | TANG Yang. Network Security Simulation Research Based on Hardware-in-the-loop Simulation[D]. Zhengzhou: Information Engineering University, 2009. |
| 唐杨. 基于HILS的网络安全仿真研究[D]. 郑州:解放军信息工程大学, 2009. | |
| [17] | YAN Shi, TANG Huidong, LUAN Dejie, et al. Study on the LKJ Simulation System Applicable for STP Simulation Test Platform[J]. Railway Transport and Economy, 2021, 43(3): 50-56. |
| 闫石, 唐汇东, 栾德杰, 等. 适用于STP仿真测试平台的LKJ模拟系统研究[J]. 铁道运输与经济, 2021, 43(3): 50-56. | |
| [18] | ZHANG Dahua, QIU Lihua, WANG Zongxue, et al. Design and Realization of Airport Refueling Automatic System Based on DCS[J]. Journal of Beijing University of Aeronautics and Astronautics, 2003, 29(8): 659-662. |
| 张大华, 裘丽华, 王宗学, 等. 基于DCS机理的机场供油自动化系统的设计与实现[J]. 北京航空航天大学学报, 2003, 29(8): 659-662. | |
| [19] | ZHANG Dahua, CHEN Yuanfu, QIU Lihua, et al. Pressure-control in the Airport Refueling System with Multi-parallel Pumps, One of Which is Powered by a Frequency Converter[J]. Acta Aeronautica ET Astronautica Sinica, 2003, 24(2): 170-173. |
| 张大华, 陈远富, 裘丽华, 等. 采用多泵并联变频调速技术实现机场恒压供油[J]. 航空学报, 2003, 24(2): 170-173. | |
| [20] | CHEN Qi, CHEN Shihui, WANG Biao, et al. Reliability Factors Analysis and Testing Technology Research on Distributed Control System[J]. Inner Mongolia Electric Power, 2013, 31(6): 43-46. |
| 陈起, 陈世慧, 王彪, 等. 分散控制系统可靠性影响因素分析及测试技术[J]. 内蒙古电力技术, 2013, 31(6): 43-46. | |
| [21] | XU Haizhou. Design and Realization of Information Security Protection of Industrial Control System Based on SDN[D]. Wuhan: Huazhong University of Science and Technology, 2019. |
| 徐海洲. 基于软件定义网络的工业控制系统信息安全防护设计及实现[D]. 武汉:华中科技大学, 2019. | |
| [22] | LI Hang, DONG Wei, ZHU Guangyu. Research on Industrial Control Protocol Vulnerability Mining Technology Based on Fuzzing Test[J]. Application of Electronic Technique, 2016, 42(7): 79-82. |
| 李航, 董伟, 朱广宇. 基于Fuzzing测试的工业控制协议漏洞挖掘技术研究[J]. 电子技术应用, 2016, 42(7): 79-82. | |
| [23] | ZHANG Renbin, ZHAO Jixiang, YANG Jian, et al. Research on Lightweight ICS Cyber Security Testbed Based on Container[J]. Application Research of Computers, 2021, 38(2): 506-509. |
| 张仁斌, 赵季翔, 杨戬, 等. 基于容器的轻量级工业控制系统网络安全测试床研究[J]. 计算机应用研究, 2021, 38(2): 506-509. | |
| [24] |
GOLDENBERG N, WOOL A. Accurate Modeling of Modbus/TCP for Intrusion Detection in SCADA Systems[J]. International Journal of Critical Infrastructure Protection, 2013, 6(2): 63-75.
doi: 10.1016/j.ijcip.2013.05.001 URL |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||