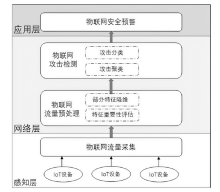
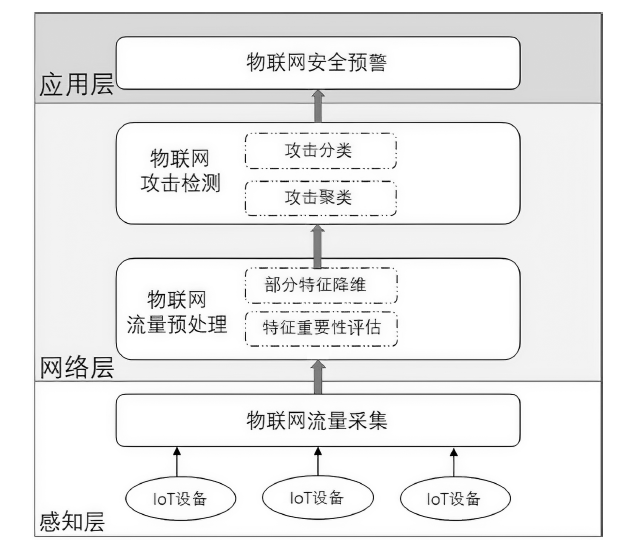
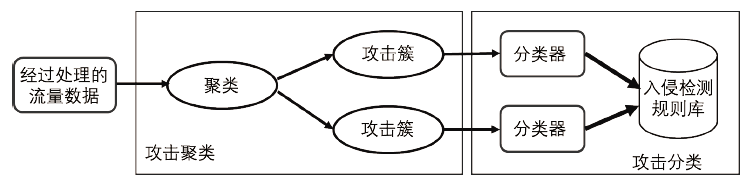
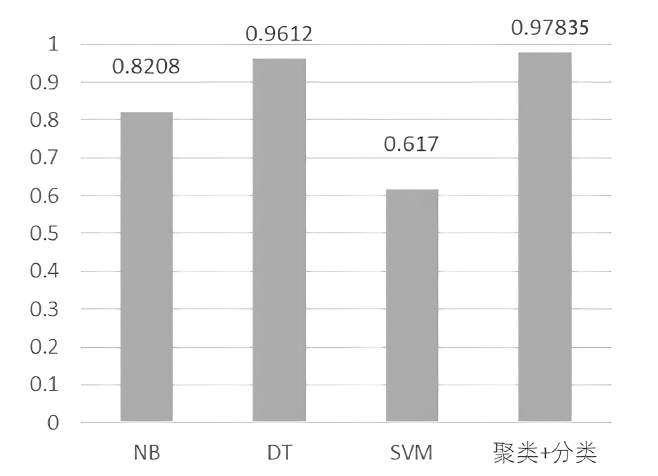
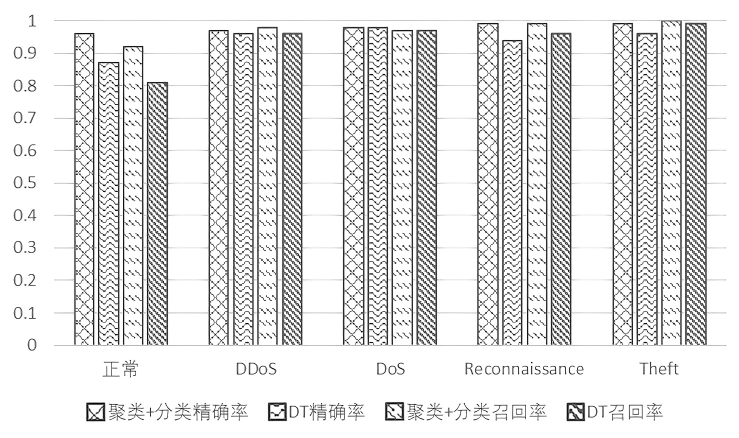
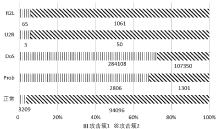
| [1] |
JAVED F, AFZAL M K, SHARIF M, et al. Internet of Things(IoT) Operating Systems Support, Networking Technologies, Applications, and Challenges: A Comparative Review[J]. IEEE Communications Surveys & Tutorials, 2018, 20(3):2062-2100.
|
| [2] |
CHEN Hongsong, CHEN Jingjiu. Statistical Based Distributed Denial of Service Attack Detection Research in Internet of Things[J]. Journal of Jilin University: Engineering and Technology Edition, 2020, 50(5):1894-1904.
|
|
陈红松, 陈京九. 基于统计的物联网分布式拒绝服务攻击检测[J]. 吉林大学学报(工学版), 2020, 50(5):1894-1904.
|
| [3] |
LIU Xiangju, LIU Pengcheng, XU Hui, et al. Distributed Denial of Service Attack Detection Method Based on Software Defined Internet of Things[J]. Journal of Computer Applications, 2020, 40(3):753-759.
|
|
刘向举, 刘鹏程, 徐辉, 等. 基于软件定义物联网的分布式拒绝服务攻击检测方法[J]. 计算机应用, 2020, 40(3):753-759.
|
| [4] |
RAY S, JIN Y, RAYCHOWDHURY A. The Changing Computing Paradigm with Internet of Things: A Tutorial Introduction[J]. IEEE Design & Test, 2016, 33(2):76-96.
|
| [5] |
BERTINO E, ISLAM N. Botnets and Internet of Things Security[J]. Computer, 2017, 50(2):76-79.
|
| [6] |
BEHAL S, KUMAR K. Detection of DDoS Attacks and Flash Events Using Information Theory Metrics—An Empirical Investigation[J]. Computer Communications, 2017(103):18-28.
|
| [7] |
ALABA F A, OTHMAN M, HASHEM I A T, et al. Internet of Things Securit: A Survey[J]. Journal of Network and Computer Applications, 2017, 88(6):10-28.
doi: 10.1016/j.jnca.2017.04.002
URL
|
| [8] |
AL-GARADI M A, MOHAMED A, AL-ALI A, et al. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security[J]. IEEE Communications Surveys & Tutorials, 2020, 22(3):1646-1685.
|
| [9] |
XU Wenya. Research on Network Intrusion Detection Based on Machine Learning[D]. Beijing: Beijing Jiaotong University, 2018.
|
|
徐温雅. 基于机器学习的网络入侵检测研究[D]. 北京:北京交通大学, 2018.
|
| [10] |
PAJOUH H H, JAVIDAN R, KHAYAMI R, et al. A Two-layer Dimension Reduction and Two-tier Classification Model for Anomaly-based Intrusion Detection in IoT Backbone Networks[J]. IEEE Transactions on Emerging Topics in Computing, 2019, 7(2):314-323.
doi: 10.1109/TETC.6245516
URL
|
| [11] |
AL-HAWAWREH M, MOUSTAFA N, SITNIKOVA E. Identification of Malicious Activities in Industrial Internet of Things Based on Deep Learning Models[J]. Information Security Technical Report, 2018, 41(8):1-11.
|
| [12] |
MEIDAN Y, BOHADANA M, SHABTAI A, et al. ProfilIoT: A Machine Learning Approach for IoT Device Identification Based on Network Traffic Analysis[C]//ACM. The 32nd ACM Symposium on Applied Computing, April 3-7, 2017, Marrakech, Morocco. New York: ACM, 2017: 506-509.
|
| [13] |
AMINANTO M E, KIM K. Improving Detection of Wi-Fi Impersonation by Fully Unsupervised Deep Learning[C]//Springer. 2017 Information Security Applications, August 24-26, 2017, Jeju Island, Korea. Cham: Springer, 2017: 212-223.
|
 ), WANG Chao1
), WANG Chao1