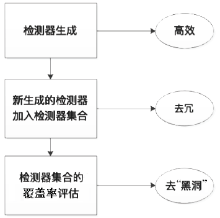
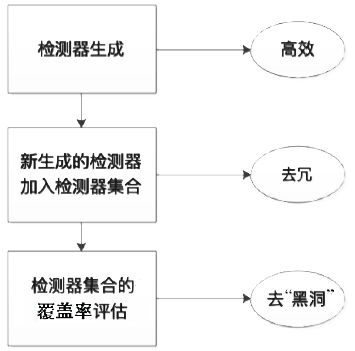
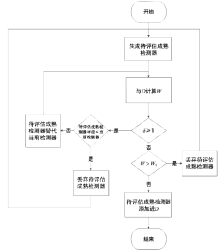
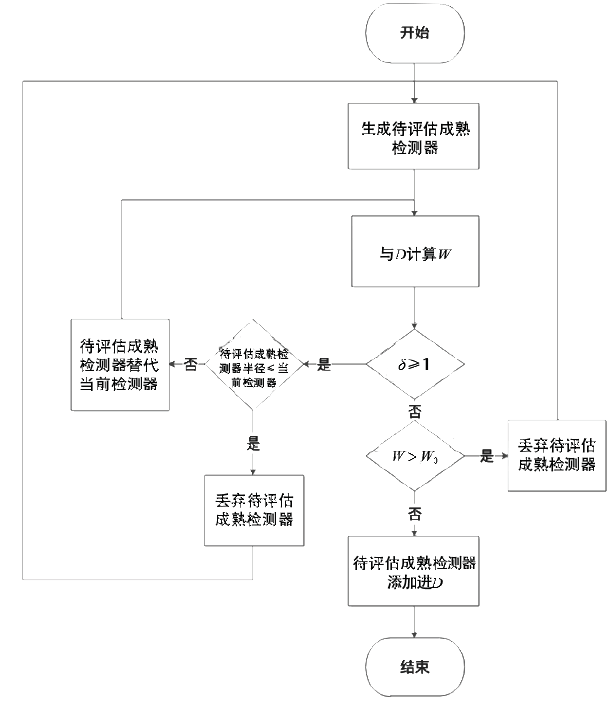
| [1] |
LIU A X, GOUDA M G. Diverse Firewall Design[J]. IEEE Transactions on Parallel and Distributed Systems, 2008,19(9):1237-1251.
|
| [2] |
METTU N, SASIKALA T. Intrusion Detection in Wireless Sensor Networks[C]// IEEE. 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT), April 20-21, 2018, Coimbatore, India. NJ: IEEE, 2018: 84-89.
|
| [3] |
SHAHRESTANI S A. Soft Computing in Network Intrusion Detection[EB/OL]. https://researchdirect.westernsydney.edu.au/islandora/object/uws:6925, 2020-05-25.
|
| [4] |
UMER M F, SHER M, BI Yaxin. A Two-stage Flow-based Intrusion Detection Model for Next-generation Networks[EB/OL]. https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0180945, 2020-05-25.
|
| [5] |
LI Jianguo, YANG Yi. Survey of Intrusion Detection System[J]. Science&Technology Vision, 2016, 6(18) 19, 36.
|
|
李建国, 杨忆. 入侵检测系统研究综述[J]. 科技视界, 2016,6(18) 19, 36.
|
| [6] |
FU Longtian, YU Yumei. Research on An Improved Immune Algorithm[J]. Bulletin of Science and Technology, 2018,34(6):219-222.
|
|
傅龙天, 余玉梅. 一种改进的免疫算法的研究[J]. 科技通报, 2018,34(6):219-222.
|
| [7] |
LIU Pengfei, LIU Ting. Physical Intrusion Detection for Industrial Control System[C]// IEEE. 2018 IEEE Conference on Communications and Network Security (CNS), May 30-June 1, 2018, Beijing, China. NJ: IEEE, 2018: 1-2.
|
| [8] |
PODDEBNIAK D, SOMOROVSKY J, SCHINZEL S, et al. Attacking Deterministic Signature Schemes Using Fault Attacks[EB/OL]. https://www.researchgate.net/publication/326276966_Attacking_Deterministic_Signature_Schemes_Using_Fault_Attacks, 2020-05-25.
|
| [9] |
ULLAH I, MAHMOUD Q H. A Hybrid Model for Anomaly-based Intrusion Detection in SCADA Networks[C]// IEEE. 2017 IEEE International Conference on Big Data, December 11-14, 2017, Boston, MA, USA. NJ: IEEE, 2018: 2160-2167.
|
| [10] |
CHOUDHARY S, KESSWANI N. A Survey: Intrusion Detection Techniques for Internet of Things[J]. International Journal of Information Security & Privacy, 2019,13(1):86-105.
|
| [11] |
FORREST S, PERELSON A S, ALLEN L, et al. Self-nonself Discrimination in a Computer[C]// IEEE. 1994 IEEE Computer Society Symposium on Research in Security and Privacy, May 16-18, 1994, Oakland, CA, USA. NJ: IEEE, 1994: 202-212.
|
| [12] |
JI Zhou, DASGUPTA D. Real-valued Negative Selection Algorithm with Variable-sized Detectors[M]// Springer. Genetic and Evolutionary Computation. Heidelberg: Springer, 2004: 287-298.
|
| [13] |
HART E, TIMMIS J. Application Areas of AIS: The Past, The Present and The Future[J]. Applied Soft Computing, 2008,8(1):191-201.
doi: 10.1016/j.asoc.2006.12.004
URL
|
| [14] |
GONZALEZ F A, DASGUPTA D. Anomaly Detection Using Real-valued Negative Selection[J]. Genetic Programming & Evolvable Machines, 2003,4(4):383-403.
|
| [15] |
JI Zhou, DASGUPTA D. V-detector: An Efficient Negative Selection Algorithm with "Probably Adequate" Detector Coverage[J]. Information Sciences, 2009,179(10):1390-1406.
|
| [16] |
DE CASTRO L N, VON ZUBEN F J. Learning and Optimization Using the Clonal Selection Principle[J]. IEEE Transactions on Evolutionary Computation, 2002,6(3):239-251.
|
| [17] |
LIU Haiyan, LI Yuqi. The Theory of Probability and Statistics[M]. Beijing: National Defense Industry Press, 2001.
|
|
刘海燕, 李裕奇. 概率论与数理统计[M]. 北京: 国防工业出版社, 2001.
|
| [18] |
DHANABAL L, SHANTHARAJAH S. A Study on NSL-KDD Dataset for Intrusion Detection System Based on Classification Algorithms[J]. International Journal of Advanced Research in Computer and Communication Engineering, 2015,4(6):446-452.
|
| [19] |
INGRE B, YADAV A, SONI A K. Decision Tree-based Intrusion Detection System for NSL-KDD Dataset[M]// Springer. Information & Communication Technology for Intelligent Systems. Cham: Springer, Cham, 2017: 207-218.
|
| [20] |
LEI Shihua, DING Lei, LI Jianfeng, et al. Improved Intrusion Detection Algorithm Based on DCA[J]. Journal of Jishou University, 2015,36(6):27-29.
|
 ), ZHU Nafei1, GE Jiake3
), ZHU Nafei1, GE Jiake3