Netinfo Security ›› 2020, Vol. 20 ›› Issue (6): 82-89.doi: 10.3969/j.issn.1671-1122.2020.06.010
Previous Articles Next Articles
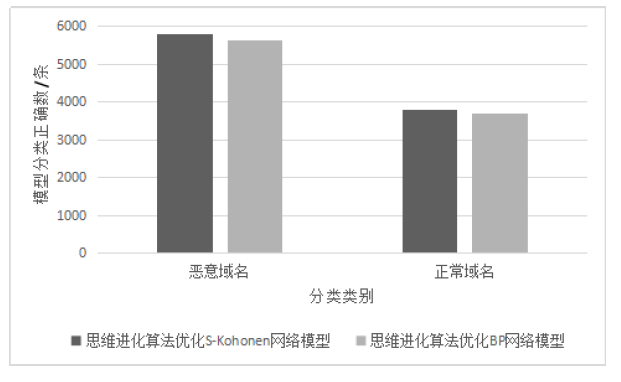
A Malicious Domain Name Detection Model Based on S-Kohonen Neural Network Optimized by Evolutionary Thinking Algorithm
- 1. The Third Research Institute of The Ministry of Public Security,Shanghai 200031, China
2. Cyber Security Team of Sichuan Provincial Public Security Department, Chengdu 610000, China
-
Received:2020-01-15Online:2020-06-10Published:2020-10-21 -
Contact:LUO Zheng E-mail:roger@cspec.org.cn
CLC Number:
Cite this article
LUO Zheng, ZHANG Xueqian. A Malicious Domain Name Detection Model Based on S-Kohonen Neural Network Optimized by Evolutionary Thinking Algorithm[J]. Netinfo Security, 2020, 20(6): 82-89.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.06.010
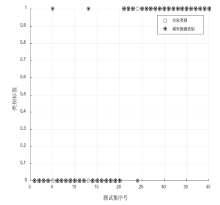
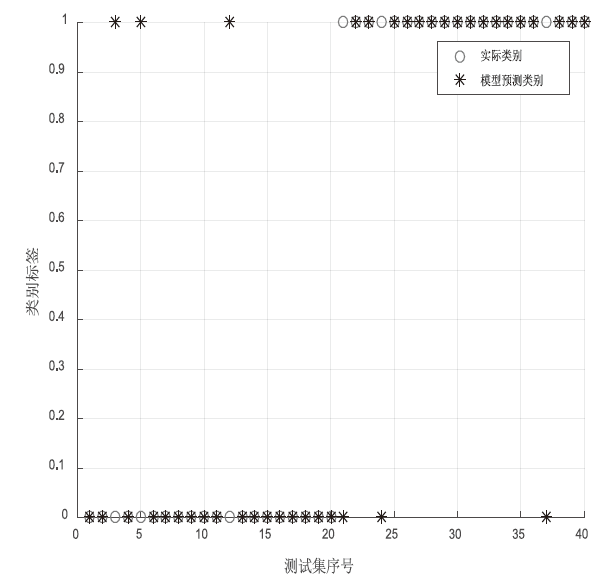
| 序号 | 思维进化算法优化 S-Kohonen网络 | 思维进化算法优化BP网络 | 测试集实际 类别 |
|---|---|---|---|
| 1 | 0 | 0 | 0 |
| 2 | 0 | 0 | 0 |
| 3 | 0 | 1 | 0 |
| 4 | 0 | 0 | 0 |
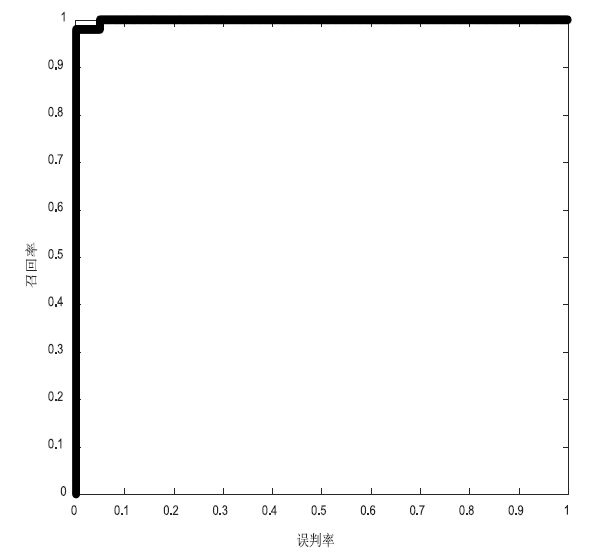
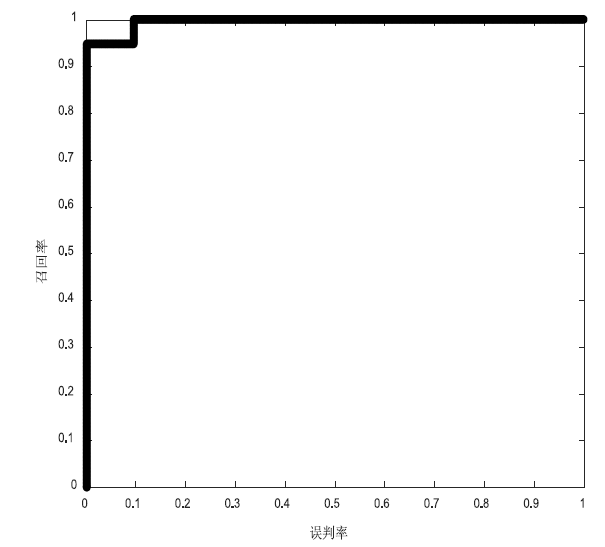
| 5 | 1 | 1 | 0 |
| 6 | 0 | 0 | 0 |
| 7 | 0 | 0 | 0 |
| 8 | 0 | 0 | 0 |
| 9 | 0 | 0 | 0 |
| 10 | 0 | 0 | 0 |
| 11 | 0 | 0 | 0 |
| 12 | 0 | 1 | 0 |
| 13 | 1 | 0 | 0 |
| 14 | 0 | 0 | 0 |
| 15 | 0 | 0 | 0 |
| 16 | 0 | 0 | 0 |
| 17 | 0 | 0 | 0 |
| 18 | 0 | 0 | 0 |
| 19 | 0 | 0 | 0 |
| 20 | 0 | 0 | 0 |
| 21 | 1 | 0 | 1 |
| 22 | 1 | 1 | 1 |
| 23 | 1 | 1 | 1 |
| 24 | 0 | 0 | 1 |
| 25 | 1 | 1 | 1 |
| 26 | 1 | 1 | 1 |
| 27 | 1 | 1 | 1 |
| 28 | 1 | 1 | 1 |
| 29 | 1 | 1 | 1 |
| 30 | 1 | 1 | 1 |
| 31 | 1 | 1 | 1 |
| 32 | 1 | 1 | 1 |
| 33 | 1 | 1 | 1 |
| 34 | 1 | 1 | 1 |
| 35 | 1 | 1 | 1 |
| 36 | 1 | 1 | 1 |
| 37 | 1 | 0 | 1 |
| 38 | 1 | 1 | 1 |
| 39 | 1 | 1 | 1 |
| 40 | 1 | 1 | 1 |
| [1] | YIN Congxian. Research And Implementation Of Malicious Domain Name Detection Technology Based On Big Data Analysis[D]. Beijing:Beijing University of Posts and Telecommunications, 2018. |
| 殷聪贤. 基于大数据分析的恶意域名检测技术研究与实现[D]. 北京:北京邮电大学, 2018. | |
| [2] | HONG Bo, GENG Guanggang, WANG Liming, et al. System to discover phishing attacks actively based on DNS[J]. Application Research of Computers, 2013,30(12):3771-3774. |
| 洪博, 耿光刚, 王利明, 等. 一种基于DNS主动检测钓鱼攻击的系统[J]. 计算机应用研究, 2013,30(12):3771-3774. | |
| [3] | ZHANG Y, HONG J I, CRANOR L F. Cantina: A Content-Based Approach to Detecting Phishing Web Sites[EB/OL]. http://www.researchgate.net/publication/221023659_CANTINA_A_content-based_approach_to_detecting_phishing_web_sites?_sg=w9ZhIXNv5TCQn_H9GIVF76s09HqBjnKpCuWsAoZDeGp7x_zIPjkrGs6f9KxeYK4Rt5dMk2vgdD6c0_2QuhHwwg, 2019-10-15. |
| [4] | CANALI D, COVA M, VIGNA G, et al. Prophiler: A Fast Filter for the Large-Scale Detection of Malicious Web Pages[EB/OL]. http://www.researchgate.net/publication/221023059_Prophiler_A_fast_filter_for_the_large-scale_detection_of_malicious_web_pages?ev=auth_pub, 2019-10-15. |
| [5] | CHOI H, ZHU B B, LEE H. Detecting Malicious Web Links and Identifying Their Attack Types[EB/OL]. Detecting Malicious Web Links and Identifying Their Attack Types, 2019 -10-15. |
| [6] | ZHANG Siyu. Malware Domain Name Mining Based on DNS Traffic[D]. Shanghai: Shanghai Jiao Tong University, 2014. |
| 章思宇. 基于DNS流量的恶意软件域名挖掘[D]. 上海:上海交通大学, 2014. | |
| [7] | LI Kunlun, DONG Ning, GUAN Liwei, et al. DoS Attack Detection Algorithm of the Improved Kohonen Network[J]. Journal of Chinese Computer Systems, 2017,38(3):450-454. |
| 李昆仑, 董宁, 关立伟, 等. 一种改进Kohonen网络的DoS攻击检测算法[J]. 小型微型计算机系统, 2017,38(3):450-454. | |
| [8] | DONG Ning. Research on Denial of Service Attack Detection Algorithm Based on S-Kohonen Neural Network[D]. Baoding: Hebei University, 2017. |
| 董宁. 基于S-Kohonen神经网络的拒绝服务攻击检测算法的研究[D]. 保定:河北大学, 2017. | |
| [9] | LU Peng, TANG Chao. Research on DoS Attack Detection Algorithm Based on S-Kohonen[J]. Computer Measurement & Control, 2018,26(10):165-169. |
| 卢鹏, 唐超. 基于S-Kohonen的DoS攻击检测算法研究[J]. 计算机测量与控制, 2018,26(10):165-169. | |
| [10] | MA Wei, MA Quanfu. Application of Supervised Kohonen Neural Network in Cancer Diagnosis[J]. Microelectronics & Computer, 2014,31(12):108-110, 113. |
| 马卫, 马全富. 有监督的Kohonen神经网络聚类算法在癌症诊断中的应用[J]. 微电子学与计算机, 2014,31(12):108-110,113. | |
| [11] | GUO Xin, WANG Lei, XUAN Bokai, et al. Gait Recognition Based on Supervised Kohonen Neural Network[J]. Acta Automatica Sinica, 2017,43(3):430-438. |
| 郭欣, 王蕾, 宣伯凯, 等. 基于有监督Kohonen神经网络的步态识别[J]. 自动化学报, 2017,43(3):430-438. | |
| [12] | LIU Wei. Research on the Utility of Grey Neural Network Model Based on Thought Evolution Algorithm in GDP Prediction[D]. Qinhuangdao: Yanshan University, 2018. |
| 刘伟. 基于思维进化算法的灰色神经网络模型预测GDP的效用研究[D]. 秦皇岛:燕山大学, 2018. | |
| [13] | HUANG Wei, CHANG Jun, SUN Zhibin. Characteristic Curve Prediction of Compressor Based on MEA-BP Neural Network[J]. Journal of Chongqing Institute of Technology, 2019,33(2):67-74. |
| 黄伟, 常俊, 孙智滨. 基于MEA-BP神经网络的压气机特性曲线预测[J]. 重庆理工大学学报, 2019,33(2):67-74. | |
| [14] | LIN Qilin, BAO Guangqing. Daily Power Load Forecasting Based on MEA-Elman Neural Network Model[J]. Industrial Instrumentation & Automation, 2017,17(3):7-10. |
| 林麒麟, 包广清. 基于MEA-Elman神经网络的电力日负荷预测[J]. 工业仪表与自动化装置, 2017,17(3):7-10. | |
| [15] | SONG Hongda, DONG Xin. Research and Implementation of Malicious Domain Name Detection Technology Based on Big Data Analysis[J]. Journal of Educational Institute of Jilin Province, 2014,30(12):142-144. |
| 宋泓达, 董鑫. 基于改进思维进化算法的神经网络负荷预测[J]. 吉林省教育学院学报, 2014,30(12):142-144. | |
| [16] | GAO Shuai, HU Hongping, LI YangAQI, et al. Prediction Based on Improved Mind Evolutionary Algorithm and BP Neural Network[J]. Mathematics in Practice and Theory, 2018,48(19):151-157. |
| 高帅, 胡红萍, 李洋, 等. 基于改进的思维进化算法与BP神经网络的AQI预测[J]. 数学的实践与认识, 2018,48(19):151-157. | |
| [17] | YU Jun, WANG Zhao, JI Tianming, et al. Wind Power Prediction Research Based on Mind Evolutionary Algorithm[J]. Computing Technology and Automation, 2017,36(2):95-99. |
| 俞俊, 王召, 籍天明, 等. 基于思维进化算法的风电功率预测研究[J]. 计算技术与自动化, 2017,36(2):95-99. | |
| [18] | WEN Yongjun, KONG Fanzhi, LI Xiaobo. Design of the Visit Statistic System for Web Site Based on the Alexa[J]. Journal Of Hunan City University(Natural Science), 2010,19(4):67-69. |
| 文勇军, 孔凡志, 李小波. 基于Alexa的网站访问统计系统的设计[J]. 湖南城市学院学报(自然科学版), 2010,19(4):67-69. | |
| [19] | LI Xiaobin. Research on Detection and Protection of Malicious Domain Name Based on SDN and Machine Learning[D]. Chongqing: Chongqing University, 2017. |
| 李小兵. 基于SDN和机器学习的恶意域名检测与防护的研究[D]. 重庆:重庆大学, 2017. | |
| [20] | ZOU Hongxia, QIN Feng, CHENG Zekai. Algorithm for Generating ROC Curve of Two-Classifier[J]. Computer Technology And Development, 2009,19(6):109-112. |
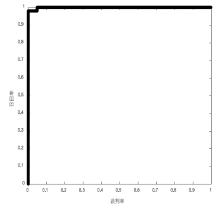
| 邹洪侠, 秦锋, 程泽凯, 等. 二类分类器的ROC曲线生成算法[J]. 计算机技术与发展, 2009,19(6):109-112. |
| [1] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [4] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [5] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [6] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [7] | HUANG Na, HE Jingsha, WU Yabiao, LI Jianguo. Method of Insider Threat Detection Based on LSTM Regression Model [J]. Netinfo Security, 2020, 20(9): 17-21. |
| [8] | ZHANG Runzi, LIU Wenmao, YOU Yang, XIE Feng. Research on AISecOps Automation Levels and Technology Trends [J]. Netinfo Security, 2020, 20(9): 22-26. |
| [9] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [10] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [11] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [12] | LIU Daheng, LI Hongling. Research on QR Code Phishing Detection [J]. Netinfo Security, 2020, 20(9): 42-46. |
| [13] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [14] | ZENG Yingming, WANG Bin, GUO Min. Research on Collaborative Defense Technology of Network Security Based on Swarm Intelligence [J]. Netinfo Security, 2020, 20(9): 52-56. |
| [15] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||