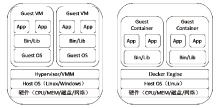
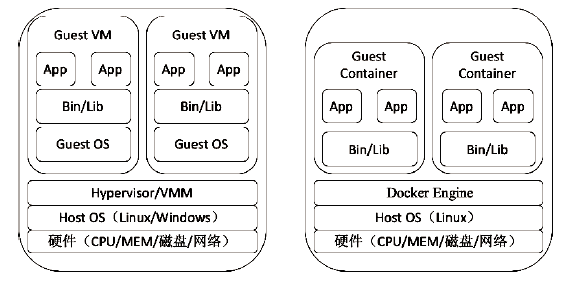
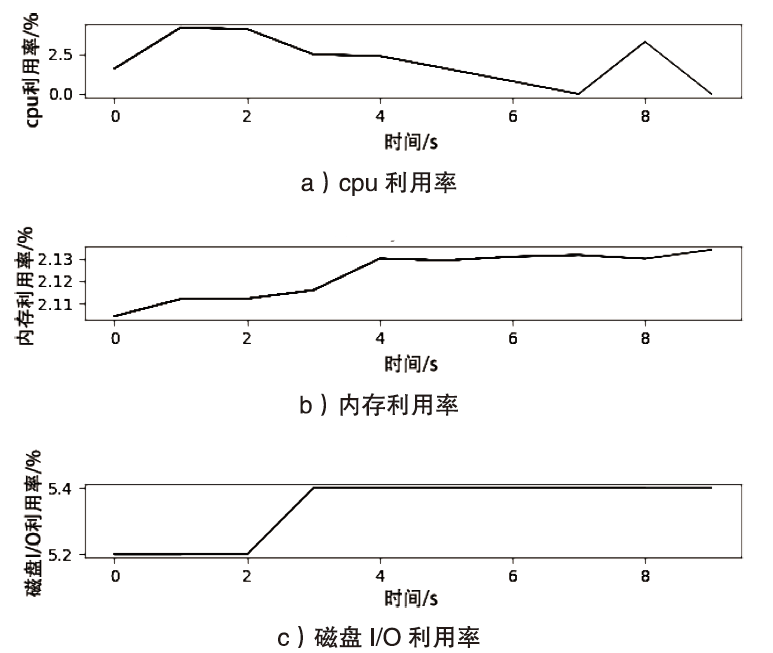
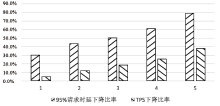
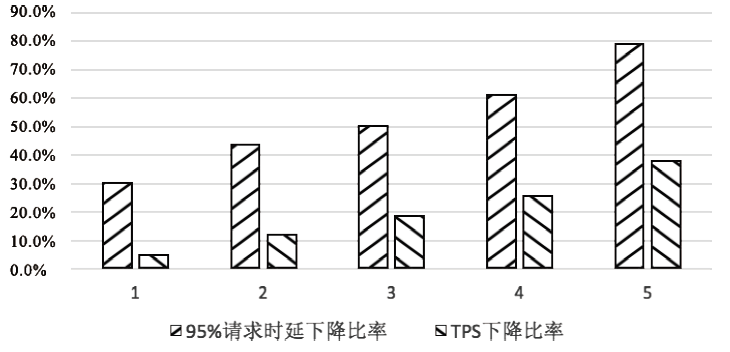
| [1] |
WANG Xiong. The History and Advantages of Cloud Computing[J]. Computer & Network, 2019,45(2):44.
|
|
王雄. 云计算的历史和优势[J]. 计算机与网络, 2019,45(2):44.
|
| [2] |
LI Wenjun. Analysis of Computer Cloud Computing Andits Implementation Technology[J]. Dual Use Technologies & Products, 2018,18(22):57-58.
|
|
李文军. 计算机云计算及其实现技术分析[J]. 军民两用技术与产品, 2018,18(22):57-58.
|
| [3] |
NSFOCUS Xingyunlab. ContainerSecurity Technical Report of NSFOCUS in 2018[EB/OL]. https://www.nsfocus.com.cn/upload/contents/2018/11/20181109100414_79051.pdf, 2018-11-9.
|
| [4] |
FORNI A A, MEULEN R. Gartner Identifies the Top Technologies for Security in 2017[EB/OL]. https://www.gartner.com/en/newsroom/press-releases/2017-06-14-gartner-identifies-the-top-technologies-for-security-in-2017, 2017-6-14.
|
| [5] |
YUNDING Lab, GEEK P. Report of Cloud Security in 2019[[EB/OL]. http://www.cbdio.com/image/site2/20191231/f42853157e261f75544321.pdf, 2019-12-31.
|
| [6] |
JUNAID K. Iron: Isolating Network-based CPU in Container Environments[C]// USENIX. 15th USENIX Symposium on Networked Systems Design and Implementation(NSDI 18), April 9-11, 2018, Renton, WA, USA. Berkeley: USENIX, 2018:312-328.
|
| [7] |
GAO Xing, GUZhongshu , KAYAALP M, et al. Container Leaks: Emerging Security Threats of Information Leakages in Container Clouds[C]// IEEE. 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks(DSN), June 26-29, 2017, Denver, CO, USA. New York: IEEE, 2017: 237-248.
|
| [8] |
MA Shiyao, JIANG Jingjie, LI Bo, et al. Maximizing Container-based Network Isolation in Parallel Computing Clusters[C]// IEEE. 2016 IEEE 24th International Conference onNetwork Protocols(ICNP), November 8-11, 2016, Singapore. New York: IEEE, 2016: 1-10.
|
| [9] |
XAVIERMG, NEVES M V, ROSSIF D, et al. Performance Evaluation of Container-based Virtualization for High Performance Computing Environments[C]// IEEE. 2013 21st Euromicro International Conference on Parallel, Distributed and Network-Based Processing(PDP), February 27-March 1, 2013, Belfast, UK. New York: IEEE, 2013: 233-240.
|
| [10] |
ARNAUTOV S, TRACH B, GREGOR F, et al. SCONE: Secure Linux Containers with Intel SGX[C]// USENIX. 12th USENIXSymposium on Operating Systems Design and Implementation(OSDI 16), November 2-4, 2016, Savannah, GA, USA. Berkeley: USENIX, 2016: 689-703.
|
| [11] |
MIRKOVIC J, REIHER P. A Taxonomy of DDoS Attack and DDoS Defense Mechanisms[J]. ACM SIGCOMM Computer Communication Review, 2004,34(2):39-53.
|
| [12] |
HUANG Jingwei, NICOL D M, CAMPELL R H. Denial-of-service Threat to Hadoop/YARN Clusters with Multi-tenancy[C]// IEEE. 2014 IEEE International Congress on Big Data, June 27-July 2, 2014, Anchorage, AK, USA. New York: IEEE, 2014: 48-55.
|
| [13] |
CHEN Fei, BI Xiaohong, WANG Jingjing, et al. Survey of DDoS Defense: Challenges and Directions[J]. Network and Information Security, 2017,3(10):16-24.
|
|
陈飞, 毕小红, 王晶晶, 等. DDoS攻击防御技术发展综述[J]. 网络与信息安全学报, 2017,3(10):16-24.
|
| [14] |
CROSBY S A, WALLACH D S. Denial of Service via Algorithmic Complexity Attacks[C]// USENIX. 12th Conferenceon USENIX Security Symposium, August 4-8, 2003, Washington, DC, USA. Berkeley: USENIX, 2003: 29-44.
|
| [15] |
CHELLADHURA J, CHELLIAH P R, KUMAR S A. Securing Docker Containers from Denial of Service(DoS) Attacks[C]// IEEE. 2016 IEEE International Conference on Services Computing(SCC), June 27-July 2, 2016, SanFrancisco, CA, USA. New York: IEEE, 2016: 856-859.
|
| [16] |
YAROM Y, FALKNER K. Flush Reload: A High Resolution, Low Noise, L3 Cache Side-channel Attack[C]// USENIX. 23rd USENIX Security Symposium(USENIX Security 14), June 20-22, 2014, Diego, CA, USA. Berkeley: USENIX, 2014: 719-732.
|
| [17] |
WU Zhenyu, XU Zhang, WANG Haining. Whispers in the Hyper-space: High-bandwidth and Reliable Covert Channel Attacks Inside the Cloud[J]. IEEE/ACM Transactions on Networking, 2014,23(2):603-615.
|
| [18] |
DELIMITROU C, KOZYRAKIS C. Bolt: I Know What You did Last Summer in the Cloud[J]. ACM SIGARCH Computer Architecture News, 2017,45(1):599-613.
|
| [19] |
DELIMITROU C, KOZYRAKIS C. iBench: Quantifying Interference for Datacenter Applications[C]// IEEE. 2013 IEEE International Symposium on Workload Characterization(IISWC), September 22-24, 2013, Portland, OR, USA. New York: IEEE, 2013: 23-33.
|
 )
)