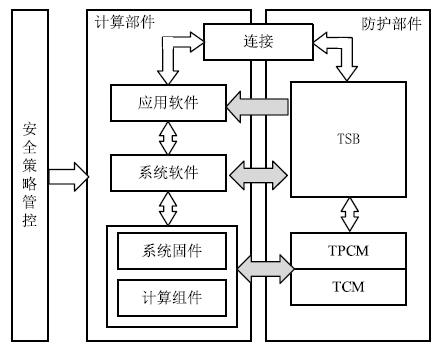
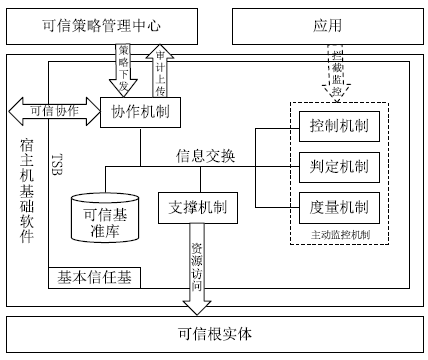
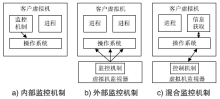
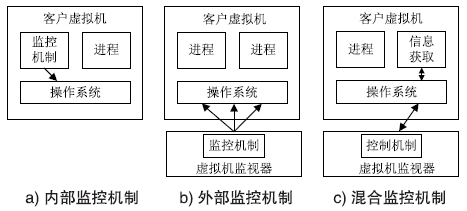
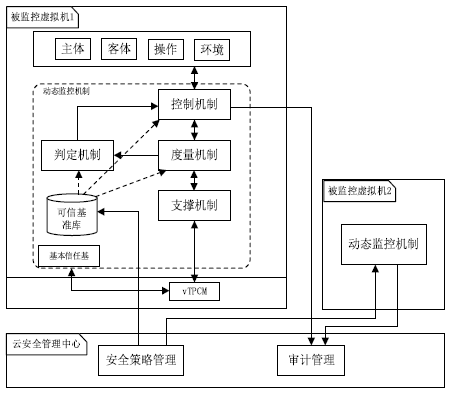
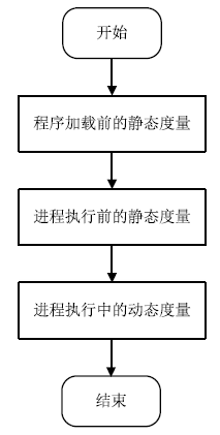
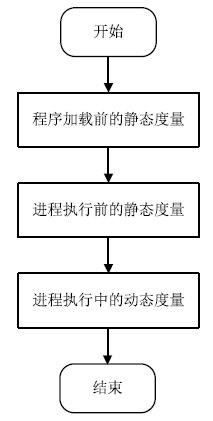
| [1] |
KADHIM Q K, YUSOF R, MAHDI H S, et al. A Review Study on Cloud Computing Issues[EB/OL]. ,2019-9-20.
|
| [2] |
ALI M, KHAN S U, VASILAKOS A V.Security in Cloud Computin: Opportunities and Challenges[J]. Information Sciences, 2015, 305(1): 357-383.
|
| [3] |
ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al.Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348.
|
|
张玉清,王晓菲,刘雪峰,等.云计算环境安全综述[J]. 软件学报,2016,27(6):1328-1348.
|
| [4] |
FENG Dengguo, ZHANG Min, ZHANG Yan, et al.Study on Cloud Computing Security[J]. Journal of Software, 2011, 22(1): 71-83.
|
|
冯登国,张敏,张妍,等.云计算安全研究[J]. 软件学报,2011,22(1):71-83.
|
| [5] |
OLIVERO I, HOLTMANNS S, MICHE Y, et al.Experiences in Trusted Cloud Computing[M]//Springer. Network and System Security. Cham: Springer, 2017: 19-30.
|
| [6] |
DU Ruizhong, PAN Wangyang, TIAN Junfeng.Dynamic Integrity Measurement Model Based on vTPM[J]. China Communications, 2018, 15(2): 88-99.
|
| [7] |
LIU Chuanyi, LIN Jie, TANG Bo.Dynamic Trustworthiness Verification Mechanism for Trusted Cloud Execution Environment[J]. Journal of Software, 2014, 25(3): 662-674.
|
|
刘川意,林杰,唐博.面向云计算模式运行环境可信性动态验证机制[J]. 软件学报,2014,25(3):662-674.
|
| [8] |
KUMAR P, SEHGAL V K, CHAUHAN D S, et al.Effective Ways of Secure, Private and Trusted Cloud Computing[J]. International Journal of Computer Science Issues, 2011, 8(3): 412-421.
|
| [9] |
SANTOS N, GUMMADI K P, RODRIGUES R. Towards Trusted Cloud Computing[EB/OL]. , 2019-9-20.
|
| [10] |
SHEN Changxiang.Constructing the Security System of Active Defense through Trusted Computing[J]. Information Security and Communications Privacy, 2016(6): 34.
|
|
沈昌祥. 可信计算构筑主动防御的安全体系[J]. 信息安全与通信保密, 2016(6):34.
|
| [11] |
SHEN Changxiang.Using Active Immune Trusted Computing 3.0 to Build a Strong Network Security Defense and Create a Clear Network Space[J]. Journal of Information Security Research, 2018, 4(4): 282-302.
|
|
沈昌祥. 用主动免疫可信计算3.0筑牢网络安全防线营造清朗的网络空间[J]. 信息安全研究,2018,4(4):282-302.
|
| [12] |
SHEN Changxiang, CHEN Xingshu.Construction of the Information Security Infrastructure Based on Trusted Computing[J]. Journal of Sichuan University: Engineering Science Edition, 2014, 46(1): 1-7
|
|
沈昌祥,陈兴蜀.基于可信计算构建纵深防御的信息安全保障体系[J]. 四川大学学报:工程科学版,2014,46(1):1-7.
|
| [13] |
SHARIF M I, LEE W, CUI Weidong, et al. Secure in-vm Monitoring Using Hardware Virtualization[EB/OL]. , 2019-9-20.
|
| [14] |
GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. , 2019-9-20
|
| [15] |
HEBBAL Y, LANIEPCE S, MENAUD J M.Virtual Machine Introspection: Techniques and Applications[C]//IEEE. 2015 10th International Conference on Availability, Reliability and Security, August 24-27, 2015, Toulouse, France. NJ: IEEE, 2015: 676-685.
|
| [16] |
BAUMAN E, AYOADE G, LIN Zhiqiang.A Survey on Hypervisor-based Monitoring: Approaches, Applications, and Evolutions[J]. ACM Computing Surveys(CSUR), 2015, 48(1): 1-33.
|
| [17] |
LI Baohui, XU Kefu, ZHANG Peng, et al.Research and Application Progress of Virtual Machine Introspection Technology[J]. Journal of Software, 2016, 27(6): 1384-1401.
|
|
李保珲,徐克付,张鹏,等.虚拟机自省技术研究与应用进展[J]. 软件学报,2016,27(6):1384-1401.
|
| [18] |
LIN Jie, LIU Chuanyi, FANG Binxing.IVirt: Integrity Measurement Mechanism for Running Environment Based on Virtual Machine Introspection[J]. Chinese Journal of Computers. 2015, 38(1): 191-203.
|
|
林杰,刘川意,方滨兴. IVirt:基于虚拟机自省的运行环境完整性度量机制[J]. 计算机学报,2015,38(1):191-203.
|
| [19] |
PAYNE B D, CARBONE M, SHARIF M, et al.Lares: An Architecture for Secure Active Monitoring Using Virtualization[C]//IEEE. 2008 IEEE Symposium on Security and Privacy, May 18-22, 2008, Oakland, CA, USA. NJ: IEEE, 2008: 233-247.
|
| [20] |
WU Xiaolong, GAO Yunwei, TIAN Xinhui, et al.SecMon: A Secure Introspection Framework for Hardware Virtualization[C]//IEEE. 2013 21st Euromicro International Conference on Parallel, Distributed, and Network-Based Processing, February 27- March 1, Belfast, UK. NJ: IEEE, 2013: 282-286.
|
| [21] |
WANG Xueyang, KARRI R.Numchecker: Detecting Kernel Control-flow Modifying Rootkits by Using Hardware Performance Counters[C]//IEEE. 2013 50th ACM/EDAC/IEEE Design Automation Conference(DAC), May 29-June 7, 2013, Austin, TX, USA. NJ: IEEE, 2013: 1-7.
|
 )
)