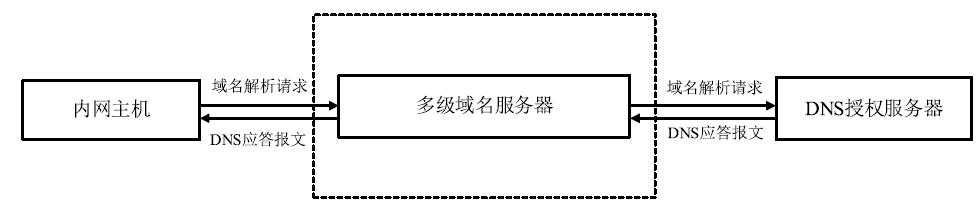
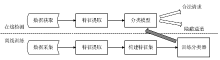
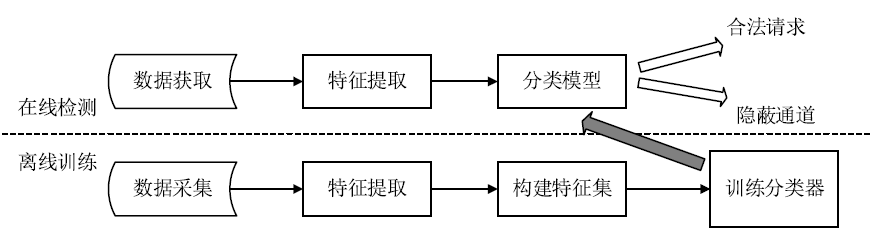
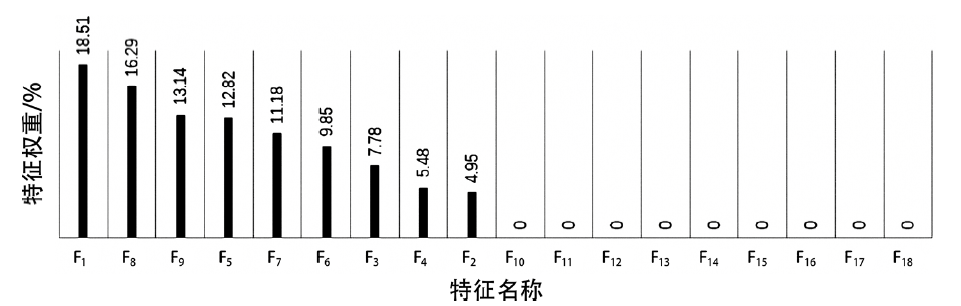
| [1] |
XU Kun.Research on DNS Convert Channel Detection Technology[D]. Chengdu: Southwest Jiaotong University, 2017.
|
|
徐琨. DNS隐蔽通道检测技术研究[D].成都:西南交通大学,2017.
|
| [2] |
SHERIDANS, KEANEA.Detection ofDNS Based Covert Channels[C]//ACM. 14th European Conference on Cyber Warfare and Security, July 2-3, 2015, Hatfield, UK. New York: ACM, 2015: 267-275.
|
| [3] |
DAS A, SHEN M Y, SHASHANKA M, et al.Detection of Exfiltration and Tunneling over DNS[C]//IEEE. 16th IEEE International Conference on Machine Learning and Applications, December 18-21, 2017, Cancun, Mexico. New York: IEEE, 2017: 737-742.
|
| [4] |
SHI Xiaomin, LIU Fei.Analysis of Covert Channel and Monitoring Technology Based on DNS Protocol[J]. Secrecy Science and Technology, 2011, 2(4): 61-65.
|
|
史晓敏,刘飞.浅析基于DNS协议的隐蔽通道及监测技术[J].保密科学技术,2011,2(4):61-65.
|
| [5] |
ELLENS W, ZURANIEWSKI P, SPEROTTO A, et al.Flow-Based Detection of DNS Tunnels[C]//Springer. Ifip International Conference on Autonomous Infrastructure, June 25-28, 2013, Barcelona, Spain. Berlin: Springer, 2013: 124-135.
|
| [6] |
AIELLO M, MONGELLI M, PAPALEO G.Supervised Learning Approaches with Majority Voting for DNSTunneling Detection[C]//Springer. International Joint Conference SOCO14-CISIS14-ICEUTE14, June 25-27, 2014, Bilbao, Spain. Berlin: Springer, 2014: 463-472.
|
| [7] |
WIELOGORSKAM, O’BRIEND.DNS Traffic Analysis for Botnet Detection[C]//CEUR-WS. 25th Irish Conference on Artificial Intelligence and Cognitive Science, December 7-8, 2017, Dublin, Ireland. Aachen: CEUR-WS, 2017: 261-271.
|
| [8] |
AIELLO M, MONGELLI M, PAPALEO G.DNS Tunneling Detection through Statistical Fingerprints of Protocol Messages and Machine Learning[J]. International Journal of Communication Systems, 2015, 28(14): 1987-2002.
|
| [9] |
BORN K, GUSTAFSON D.Ngviz: Detecting DNS Tunnels through N-Gram Visualization and Quantitative Analysis[C]//ACM. Proceedings of the Sixth Annual Workshop on Cyber Security and Information Intelligence Research, April 21-23, 2010, Oak Ridge, Tennessee, USA. New York: ACM, 2010: 47.
|
| [10] |
DAVUTH N, KIM S R.Classification of Malicious Domain Names Using Support Vector Machine and Bi-gram Method[J]. International Journal of Security and Its Applications, 2013, 7(1): 51-58.
|
| [11] |
QI C, CHEN X, XU C, et al. A Bigram based Real Time DNS Tunnel Detection Approach[EB/OL]. , 2019-3-23.
|
| [12] |
ZHAO G, XU K, XU L, et al. Detecting APT Malware Infections based on Malicious DNS and Traffic Analysis[EB/OL]. , 2015-6-13.
|
| [13] |
HUANG Kai, FU Jianming, HUNAG Jianwei, et al.A Malicious Domain Detection Approach Based on Character and Resolution Features[J]. Computer Simulation, 2018, 35(3): 287-292.
|
|
黄凯,傅建明,黄坚伟,等.一种基于字符及解析特征的恶意域名检测方法[J].计算机仿真,2018,35(3):287-292.
|
| [14] |
BRUTZKUS A, LEVIN R. Detecting Domain Name System (DNS) Tunneling Based on DNS Logs and Network Data: U.S. Patent Application 15/466, 300[P]. 2018-9-27.
|
| [15] |
SONG Jinwei, YANG Jin, LI Tao.Research on Domain Flux Botnet Domain Name Detection Method Based on Weighted Support Vector Machine[J]. Netinfo Security, 2018, 18(12): 66-71.
|
|
宋金伟,杨进,李涛.基于加权支持向量机的Domain Flux僵尸网络域名检测方法研究[J].信息网络安全,2018,18(12):66-71.
|
| [16] |
HOMEM I, PAPAPETROU P.Harnessing Predictive Models for Assisting Network Forensic Investigations of DNS Tunnels[C]//Bepress. Annual ADFSL Conference on Digital Forensics, Security and Law, May 15-15, 2017, Daytona Beach, Florida, USA. Berkeley, California: Bepress, 2017: 79-94.
|
| [17] |
YU B, OLUMOFIN F, SMITH L, et al.Behavior Analysis based DNS Tunneling Detection and Classification with Big Data Technologies[C]//SciTePress. Proceedings of the International Conference on Internet of Things and Big Data, April 23-25, 2016, Rome, Italy. Setúbal: SciTePress, 2016: 284-290.
|
| [18] |
WU Xihong, LIU Baoxu, YANG Peian.Analvsis Botnet Behavior Based on the Domain Name[J]. Netinfo Security, 2013, 13(9): 10-13.
|
|
巫锡洪,刘宝旭,杨沛安.基于域名的僵尸网络行为分析[J].信息网络安全,2013,13(9):10-13.
|
| [19] |
MITCHELL J.Learning Semantic Representations in a Bigram Language Model[C]//ACM. Proceedings of the 10th International Conference on Computational Semantics, March 19-22, 2013, University of Potsdam, Potsdam, Germany. New York: ACM, 2013: 362-368.
|
| [20] |
SHAFIEIAN S, SMITH D, ZULKERNINE M.Detecting DNS Tunneling Using Ensemble Learning[C]// Springer. International Conference on Network and System Security, August 21-23, 2017, Helsinki, Finland. Berlin: Springer, 2017: 112-127.
|
 )
)