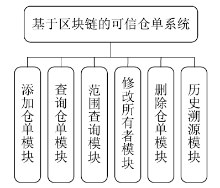
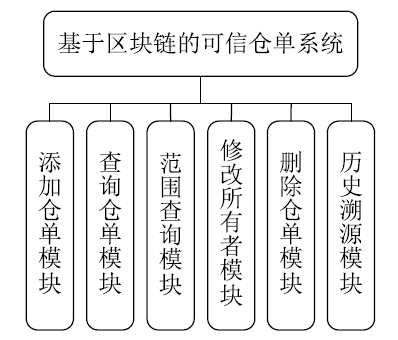
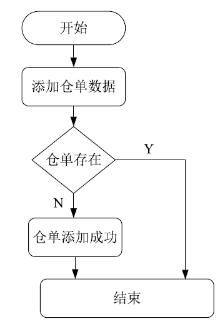
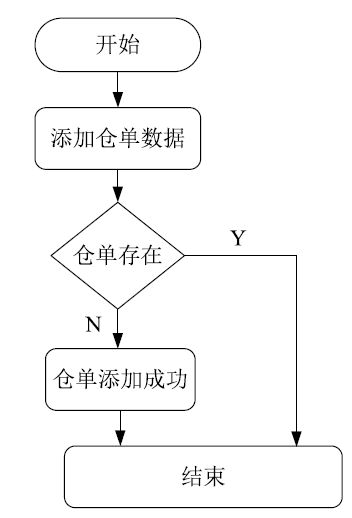
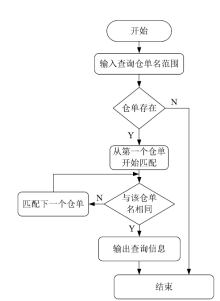
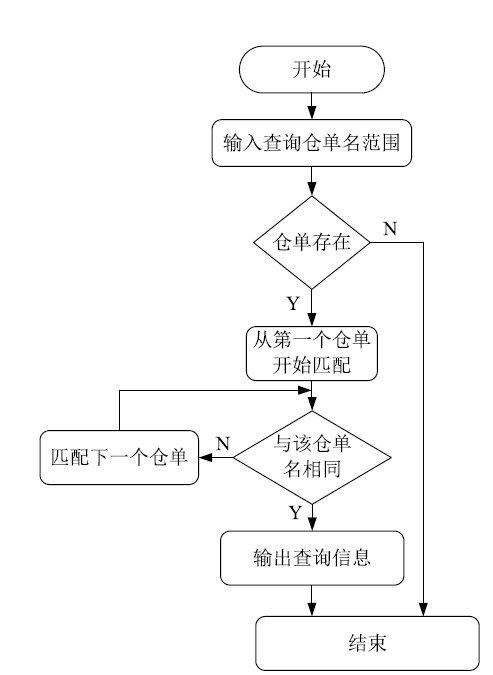
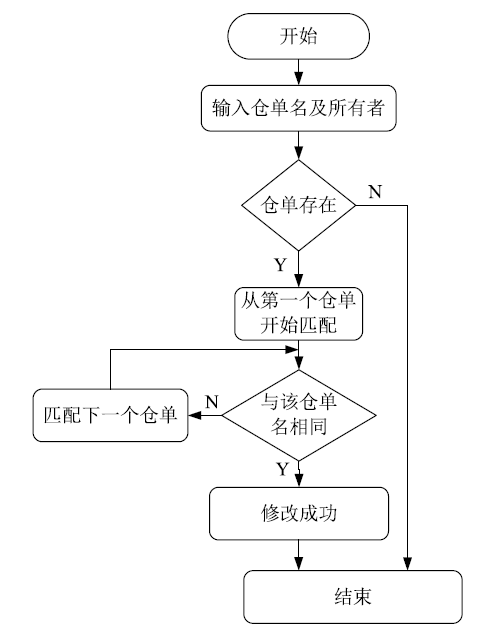
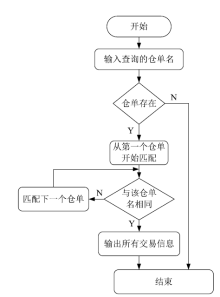
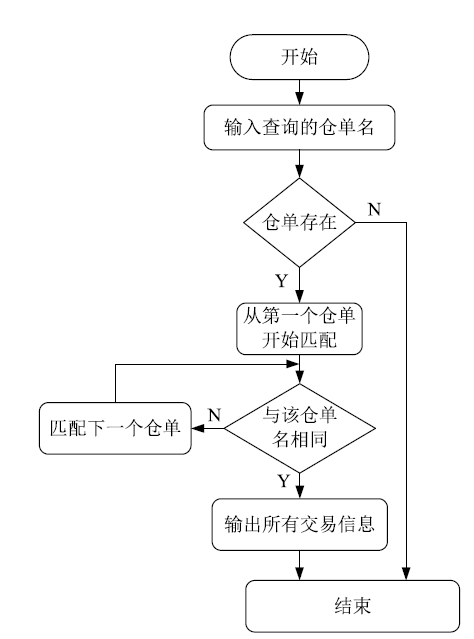
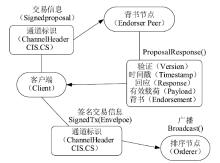
| [1] |
ZHANG Yu, WEN Jiangtao.The IoT Electric Business Model: Using Blockchain Technology for the Internet of Things[J]. Peer-to-peer Networking and Applications, 2017, 10(4): 983-994.
|
| [2] |
CHUNG H, SHEU H J, HSU S. Trading Platform, Market Volatility and Pricing Efficiency in the Floor-traded and E-mini Index Futures Markets[J]. International Review of Economics & Finance, 2010, 19(4): 742-754.
|
| [3] |
XU Weili.Research on Third-party Logistics Companies to Develop Online Financial Services Supply Chain[J]. Logistics Engineering and Management, 2014, 36(11): 66-68.
|
|
徐维莉. 第三方物流企业开发线上供应链金融服务研究[J].物流工程与管理,2014,36(11):66-68.
|
| [4] |
JIANG Dongdong, SHANG Yulin, TIAN Ye, et al.The Construction of Electronic Warehouse Receipts Circulation Platform Based on Blockchain[J]. Journal of Xi’an Polytechnic University, 2017(6): 828-834.
|
|
蒋东东,商玉林,田野,等.基于区块链的电子仓单流转平台建设[J].西安工程大学学报,2017(6):828-834.
|
| [5] |
UNDERWOOD S.Blockchain beyond Bitcoin[J]. Communications of the ACM, 2016, 59(11): 15-17.
|
| [6] |
NAKAMOTO S. Bitcoin: A Peer-to-peer Electronic Cash System[EB/OL]. https://news.ycombinator.com/item?id=15883186, 2018-1-11.
|
| [7] |
NEUDECKER T, ANDELFINGER P, HARTENSTEIN H.A Simulation Model for Analysis of Attacks on the Bitcoin Peer-to-peer Network[C]//IEEE. 2015 IFIP/IEEE International Symposium on Integrated Network Management, May 11-15, 2015, Ottawa, ON, Canada. New Jersey: IEEE, 2015: 1327-1332.
|
| [8] |
XIE Hui, WANG Jian.Study on Block Chain Technology and its Applications[J]. Netinfo Security, 2016, 16(9): 192-195.
|
|
谢辉,王健.区块链技术及其应用研[J].信息网络安全,2016,16(9)192-195.
|
| [9] |
AITZHAN N Z, SVETINOVIC D.Security and Privacy in Decentralized Energy Trading through Multi-signatures, Blockchain and Anonymous Messaging Streams[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(5): 840-852.
|
| [10] |
LIN I C, LIAO T C.A Survey of Blockchain Security Issues and Challenges[J]. International Journal of Network Security, 2017, 19(5): 653-659.
|
| [11] |
HAN Xuan, LIU Yamin.Research on the Consensus Mechanisms of Blockchain Technology[J]. Netinfo Security, 2017, 17(9): 147-152.
|
|
韩璇,刘亚敏.区块链技术中的共识机制研究[J].信息网络安全,2017,17(9):147-152.
|
| [12] |
KOSBA A, MILLER A, SHI E, et al.Hawk: the Blockchain Model of Cryptography and Privacy-preserving Smart Contracts[C]//IEEE. 2016 IEEE Symposium on Security and Privacy, May 22-26, 2016, San Jose, CA, USA. New Jersey: IEEE, 2016: 839-858.
|
| [13] |
WANG Hao, SONG Xiangfu, KE Junming, et al.Blockchain and Privacy Preserving Mechanisms in Cryptocurrency[J]. Netinfo Security, 2017, 17(7): 32-39.
|
|
王皓,宋祥福,柯俊明,等.数字货币中的区块链及其隐私保护机制[J].信息网络安全,2017,17(7):32-39.
|
| [14] |
DINH T T A, LIU R, ZHANG M, et al. Untangling Blockchain: A Data Processing View of Blockchain Systems[J]. IEEE Transactions on Knowledge and Data Engineering, 2018, 30(7): 1366-1385.
|
| [15] |
TURNER C H, COWIN S C, RHO J Y, et al.The Fabric Dependence of the Orthotropic Elastic Constants of Cancellous Bone[J]. Journal of Biomechanics, 1990, 23(6): 549-561.
|
| [16] |
BHASKARAN K, ILFRICH P, LIFFMAN D, et al.Double-blind Consent-driven Data Sharing on Blockchain[C]//IEEE. 2018 IEEE International Conference on Cloud Engineering, April 17-20, 2018, Orlando, FL, USA. New Jersey: IEEE, 2018: 385-391.
|
| [17] |
PECK M.A Blockchain Currency that Beats Bitcoin on Privacy[J]. IEEE Spectrum, 2016, 53(12): 11-13.
|
| [18] |
NOFER M, GOMBER P, HINZ O, et al.Blockchain[J]. Business & Information Systems Engineering, 2017, 59(3): 183-187.
|
| [19] |
IANSITI M, LAKHANI K R.The Truth about Blockchain[J]. Harvard Business Review, 2017, 95(1): 118-127.
|
| [20] |
YIN Wei, WEN Qiaojian, LI Wenmin, et al.An Anti-quantum Transaction Authentication Approach in Blockchain[J]. IEEE Access, 2018, 6(99): 5393-5401.
|
 ), Dongmei QING, Yining LIU, Songzhan LV
), Dongmei QING, Yining LIU, Songzhan LV