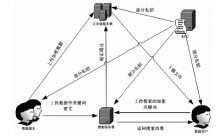
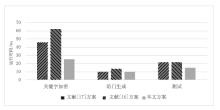
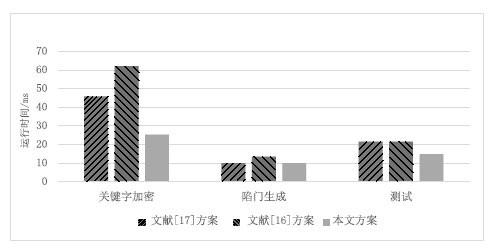
| [1] |
MELL T, GRANCE P.Draft NIST Working Definition of Cloud Computing[J]. Emergency Medicine Journal, 2009, 53(6): 50.
|
| [2] |
LI Jingwei, JIA Chunfu, LIU Zheli,et al.Survey on the Searchable Encryption[J]. Journal of Software,2015, 26(1): 109-128.
|
|
李经纬,贾春福,刘哲理,等.可搜索加密技术研究综述[J].软件学报,2015,26(1):109-128.
|
| [3] |
LU Haining.Searchable Symmetric Encryption with Hidden Search Pattern[J]. Netinfo Security, 2017,17(1): 38-42.
|
|
陆海宁. 可隐藏搜索模式的对称可搜索加密方案[J].信息网络安全,2017,17(1):38-42.
|
| [4] |
SONG D X, WAGNER D, PERRIG A.Practical Techniques for Searches on Encrypted Data[C]//IEEE. Proceeding 2000 IEEE Symposium on Security and Privacy, May 14-17, 2000, Berkeley, CA, USA.Washington DC: IEEE, 2000: 44-55.
|
| [5] |
BONEH D, CRESECNEO G D, OSTROVSKY R, et al.Public Key Encryption with Keyword Search[C]//Springer. International Conference on the Theory and Applications of Cryptographic Techniques, May 2-6, 2004, Interlaken, Switzerland. Berlin: Springer,2004:506-522.
|
| [6] |
BAEK J, SAFAVINAINI R, SUSILO W.Public Key Encryption with Keyword Search Revisited[C]//Springer. Proceeding Sof the International Conference on Computational Science and ITS Applications, June 30-July 3, 2008, Perugia, Italy. Berlin: Springer,2008:1249-1259.
|
| [7] |
SHAMIR A.Identity-Based Cryptosystems and Signature Schemes[C]//Springer. The Workshop on the Theory and Application of Cryptographic Techniques, April 9-11, 1984, Santa Barbara, California, USA. Berlin: Springer,1985:47-53.
|
| [8] |
Al-RIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[C]//Springer. Proceedings of the 9th International Conference on the Theory and Application of Cryptology and Information Security, December 3-7, 2003, Taipei, China. Berlin: Springer,2003:452-473.
|
| [9] |
PENG Yanguo, CUI Jiangtao, et al.Certificateless Public Key Encryption with Keyword Search[J]. China Communications, 2014, 11(11): 100-113.
|
| [10] |
WU Tsuyang, MENG Fanya, CHEN Chienming, et al.On the Security of a Certificateless Searchable Public Key Encryption Scheme[C]//Springer. Proceedings of the 10th International Conference on Genetic and Evolutionary Computing, November 7-9, 2016, Fuzhou, Fujian, China. Berlin: Springer, 2016: 113-119.
|
| [11] |
ISLAM S H, OBAIDAT M S, RAJEEV V, et al.Design of A Certificateless Designated Server Based Searchable Public Key Encryption Scheme[C]//Springer. International Conference on Mathematics and Computing, January 17-21, 2017, Haldia, India. Berlin: Springer, 2017: 3-15.
|
| [12] |
ZHANG Nan, CHEN Lanxiang.Research on An Efficient Ranked Keywords Searchable Encryption System[J]. Netinfo Security, 2017, 17(2): 43-50.
|
|
张楠,陈兰香.一种高效的支持排序的关键词可搜索加密系统研究[J].信息网络安全,2017,17(2):43-50.
|
| [13] |
WU Qiying, MA Jianfeng, LI Hui, et al.Certificateless Conjunctive Keyword Search over Encrypted Data[J]. Journal of Xidian University(Natural Science), 2017, 44(3): 55-60.
|
|
伍祈应,马建峰,李辉,等.无证书连接关键字密文检索[J].西安电子科技大学学报(自然科学版),2017,44(3):55-60.
|
| [14] |
WANG Baomin, HE Zhiling, LUO Wenjun.An Efifcient Scheme of Multi-user Searchable Encryption with Keyword in Cloud Storage[J]. Netinfo Security, 2013, 13(12): 33-36.
|
|
王保民,何智灵,罗文俊.基于云存储的多用户可搜索加密方案[J].信息网络安全,2013,13(12):33-36.
|
| [15] |
HUANG Haiping, DU Jianpeng, et al, WANG Ruchuan. Multi-sever Multi-keyword Searchable Encryption Scheme Based on Cloud Storage[J]. Journal of Electronics and Information Technology, 2017, 39(2): 389-396.
|
|
黄海平,杜建澎,戴华,等.一种基于云存储的多服务器多关键词可搜索加密方案[J].电子与信息学报,2017,39(2):389-396.
|
| [16] |
XIANG Shunbo, LI Yunhe, XU Bing.Certificateless Searchable Encryption Scheme for Cloud Storage[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science), 2017, 37(6): 90-97.
|
|
项顺伯,李云鹤,徐兵.面向云存储的无证书可搜索加密方案[J].南京邮电大学学报(自然科学版),2017,37(6):90-97.
|
| [17] |
MA Mimi, HE Debiao, KUMAR N, et al.Certificateless Searchable Public Key Encryption Scheme for Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2018, 14(2):759-767.
|
 ), Xiaoli LANG, Caifen WANG
), Xiaoli LANG, Caifen WANG