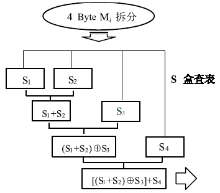
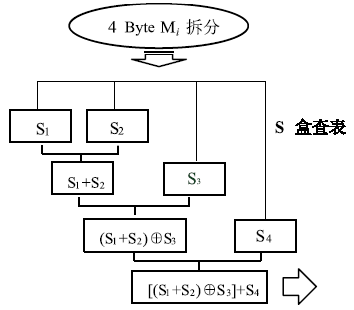
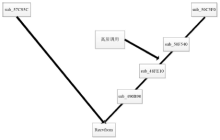
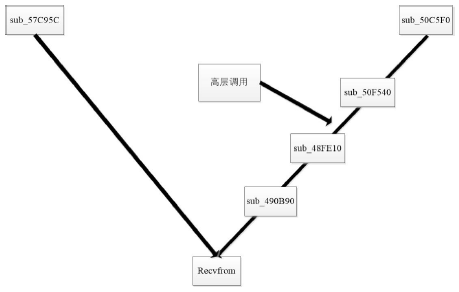
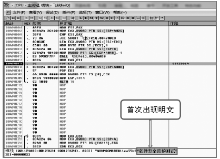
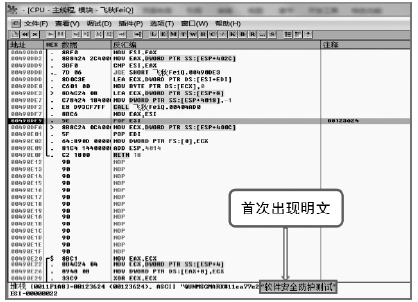
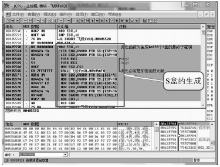
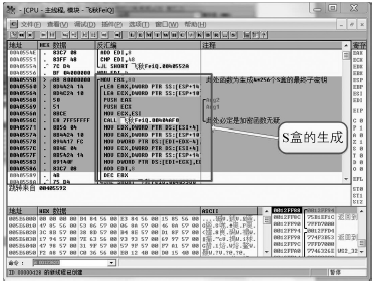
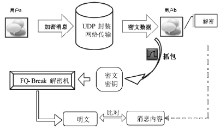
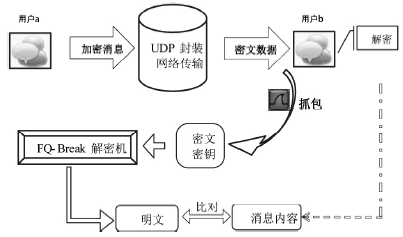
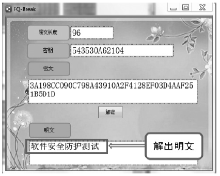
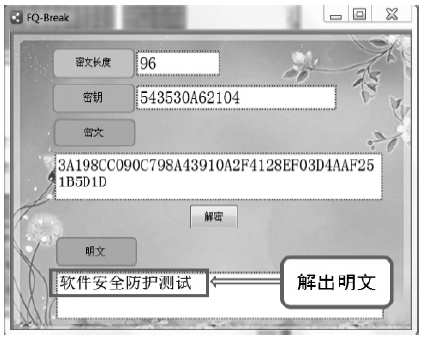
Netinfo Security ›› 2018, Vol. 18 ›› Issue (11): 73-80.doi: 10.3969/j.issn.1671-1122.2018.11.010
• 技术研究 • Previous Articles Next Articles
Analysis of Data Hijacking in Instant Communication Network
Qingjun YUAN1, Siqi LU1,2( ), Zhongxing WEI1, Jie GOU3
), Zhongxing WEI1, Jie GOU3
- 1. PLA University of Information Engineering, Zhengzhou Henan 450000, China
2. State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
3. 31011 PLA Troops, Beijing 100093, China
-
Received:2018-04-15Online:2018-11-10Published:2020-05-11
CLC Number:
Cite this article
Qingjun YUAN, Siqi LU, Zhongxing WEI, Jie GOU. Analysis of Data Hijacking in Instant Communication Network[J]. Netinfo Security, 2018, 18(11): 73-80.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2018.11.010
| [1] | LI Qiang, LIU Baoxu, JIANG Zhengwei, et al.Analysis of Model of QQ Forensic in Android System[J]. Netinfo Security, 2016,16(1):40-44. |
| 李强, 刘宝旭, 姜政伟, 等. 一种Android系统下的QQ取证模型分析[J]. 信息网络安全, 2016,16(1):40-44. | |
| [2] | PEDIY.Research on Communication Encryption of FeiQ[EB/OL]. , 2016-10-8. |
| [3] | SCHNEIER B.Description of a New Variable-length Key, 64-bit Block Cipher (Blowfish)[EB/OL]. ,2018-2-15. |
| [4] | PATEL P, PATEL R, PATEL N.Integrated ECC and Blowfish for Smartphone Security[J].Procedia Computer Science, 2016, 78(3): 210-216. |
| [5] | RUBAB S, JAVED Y.Efficient Image Steganogrphic Algorithms Utilizing Transforms: Wavelet and Contourlet with Blowfish Encryption[J]. International Journal of Computer Network & Information Security, 2015, 7(2): 15-24. |
| [6] | PATIL P, NARAYANKAR P, NARAYAN D G, et al. A Comprehensive Evaluation of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish[EB/OL]. ,2018-2-15. |
| [7] | GAO Junfeng, ZHANG Yuefeng, LUO Senlin, et al.Research on Reverse Analysis Method of Network Coding Protocol Taint Backtracking[J]. Netinfo Security, 2017,17(1):68-76. |
| 高君丰, 张岳峰, 罗森林,等.网络编码协议污点回溯逆向分析方法研究[J]. 信息网络安全, 2017,17(1):68-76. | |
| [8] | LIU Yu, WANG Minghua, SU Purui, et al.Communication Protocol Reverse Engineering of Malware Using Dynamic Taint Analysis[J]. Electronic Journal,2012,40(4):661-668. |
| 刘豫, 王明华, 苏璞睿,等. 基于动态污点分析的恶意代码通信协议逆向分析方法[J]. 电子学报, 2012, 40(4): 661-668. | |
| [9] | ZHENG Lifen, XIN Yang.Analysis and Implementation of QQ Software Protocol Based on DPI Technology[J]. Netinfo Security,2016,16(1):51-58. |
| 郑丽芬,辛阳. 基于DPI的即时通信软件协议分析与实现[J]. 信息网络安全, 2016,16(1):51-58. | |
| [10] | BANERJEE U, VASHISHTHA A, SAXENA M.Evaluation of the Capabilities of WireShark as a Tool for Intrusion Detection[J]. International Journal of Computer Applications, 2010, 6(7): 1-5. |
| [11] | PADARYAN V A, LEDOVSKIKH I N.On the Representation of Results of Binary Code Reverse Engineering[J]. Programming & Computer Software, 2018, 44(3):200-206. |
| [12] | CHEN Jiaying. Reverse Engineering for Binary Protocol Based on Network Traces[EB/OL]. ,2018-2-15. |
| [13] | WANG Jiagang, GU Guochang,MA Chunguang,et al.Efficient and Configurable Transmission Protocol Based on UDP in Grid Computing[J].Frontiers of Electrical and Electronic Engineering, 2009, 4(1): 35-42. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||