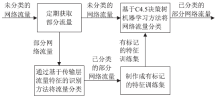
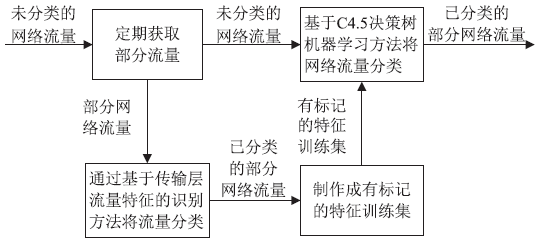
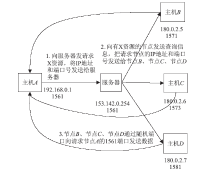
| [1] |
WANG J, ZHOU Y, YANG Y, et al.Classify the majority of the total bytes on the Internet[C]//Information Processing (ISIP), 2008 International Symposiums on, Moscow, 2008.
|
| [2] |
KIM M S, KANG H J, HONG J W.Towards peer-to-peer traffic analysis using flows[C]//Self-Managing Distributed Systems, LNCS 2867. Berlin: Springer, 2004: 55-67.
|
| [3] |
鲁刚,张宏莉,叶麟. P2P流量识别[J]. 软件学报,2011,22(6):1281-1298.
|
| [4] |
KARAGIANNIS T, BROIDO A, FALOUTSOS M.Transport layer identification of P2P traffic[C]//New York, NY, USA: ACM, 2004: 121-134.
|
| [5] |
HAFFNER P, SEN S, SPATSCHECK O, et al.ACAS: Automated construction of application signatures[C]//SIGCOMM’05 Workshops, New York, 2005: 197-202.
|
| [6] |
BASET S, SCHUNZRINNE H G.An analysis of the Skype peer-to-peer Internet telephony protocol[C]//Proceedings of the 25th IEEE International Conference on Computer Communications, USA: INFOCOM, 2006: 1-11.
|
| [7] |
袁雪美,王晖. P2P流量识别技术综述[J]. 计算机应用,2009,29(5):12-13.
|
| [8] |
MARIOS I, PAPPU P, FALOUTSOS M. Network Traffic Analysis using Traffic Dispersion Graphs (TDGs):Techniques and Hardware Implementation[J]. Technical Report, 2007, UCR-CS-2007-05001: 15-18.
|
| [9] |
GU CHENGJIE, ZHANG SHUNYI, XUE XIAOZHEN.Encrypted Internet Traffic Classification Method based on Host Behavior[J]. Internet Journal of Digital Content Technology and its Applications, 2011, 5(3): 167-174.
|
| [10] |
BRANCH P A, HEYDE A, ARMITAGE G J.Rapid identification of Skype traffic flows[C]//NOSSDAV’09. USA: Virginia, 2009: 91-96.
|
| [11] |
FREIRE E P, ARTUR Z, RONALDO M.On Metrics to Distinguish Skype flows from HTTP traffic[J]. Journal of Network and Systems Management, 2009, 17(1-2): 57-66.
|
| [12] |
EHLERT S, SANDRINE PETGAND.Analysis and Signature of Skype VoIP Session Traffic[C]//Fraunhofer FOKUS Technical Report NGNI-SKYPE-06b, 2006:14-15.
|
| [13] |
IDREESS F, UZMA A K.A generic technique for Voice over Internet Protocol(VoIP) traffic detection[J]. IJCSNS International Journal of Computer Science and Network Security, 2008, 8(2): 52-59.
|
| [14] |
ROUGHAN M,SEN S,SPATSCHECK O.Class-of-service mapping for QoS: a statistical signature-based approach to IP traffic classification[C]//Proceedings of the 4th ACM SIG- COMM conference on Internet measurement. Taormina, Sicily, Italy: ACM, 2004: 135-148.
|
| [15] |
CONSTANTINOU F, MAVROMMATIS P.Identifying Known and Unknown Peer-to-Peer Traffic[J]. NCA, 2006: 93-102.
|
| [16] |
SEN S, WANG J.Analyzing peer-to-peer traffic across large networks[J]. IEEE-ACM TRANSACTIONS ON NETWORKING, 2004, 12(2): 219-232.
|
| [17] |
KARAGIANNIS T,PAPAGIANNAKI K,FALOUTSOS M.BLINC: multilevel traffic classification in the dark[C]// SIGCOMM’05, New York, 2005: 229-240.
|
| [18] |
ALSHAMMARI R, LICHODZIJEWSKI P, HEYWOOD M, et al.Classifying SSH Encrypted Traffic with Minimum Packet Header Features using Genetic Programming[C]//Defense applications of computational intelligence workshop, USA: GECCO, 2009: 2539-2546.
|
| [19] |
THANH V V, FUKUDA K, CHAN H N, et al.A study on P2P traffic characteristics evaluation in the WIDE backbone[C]//The 6th ICITA, USA, 2009: 286-291.
|
| [20] |
ESTEVES A F, INACIO P, PEREIRA M, et al.On-line Detection of Encrypted Traffic Generated by Mesh-Based Peer-to-Peer Live Streaming Applications: The Case of GoalBit[C]//IEEE 10th International Symposium on Network Computing and Applications, 2011: 223-228.
|
| [21] |
ROSSI D, VALENTI S.Fine-grained traffic classification with Netflow data[C]//IWCMC, France, 2010: 479-483.
|
| [22] |
Gomes J V P, INACIO P, FREIER M, et al. Analysis of Peer-to-Peer Traffic Using a Behavioural Method Based on Entropy[C]//The 27th IEEE IPCCC, USA, 2008: 201-208.
|
| [23] |
鲁刚,张宏莉. P2P流量分类研究[J]. 智能计算机与应用,2013,3(3):2-3.
|
| [24] |
MUNZ G, HECKMULLER S, BRAUN L, et al.Improving Markov-based TCP Traffic Classification[C]//17th GI/ITC Conference on Communication in Distributed Systems, Viet nam, 2010: 61-72.
|
| [25] |
MOORE A W, ZUEV D.Internet Traffic Classification Using Bayesian Analysis Techniques[C]//SIGMETRICS’05, Canada: ACM, 2005: 50-60.
|
| [26] |
ERMAN J, ARLITT M F, MAHANTI A.Traffic classification using clustering algorithms[J]. MineNet, 2006: 281-286.
|
| [27] |
ERMAN J, MAHANTI A, ARLITT M F.Byte me: a case for byte accuracy in traffic classification[J]. MineNet, 2007: 35-38.
|
| [28] |
ABI P S.Efficient Detection of VoIP calls Hidden in Web Traffic[J]. IJTES, 2011, 2(1): 1-4.
|
| [29] |
AULD T, MOORE A W, GULL S F.Bayesian Neural networks for Internet Traffic Classification[J].IEEE Transactions on neural networks, 2007, 18(1): 223-239.
|
| [30] |
YUAN R X, LI Z, GUAN X H, et al.An SVM-based machine learning method for accurate internet traffic classification[J]. Information Systems Frontiers, 2010, 12(2): 149-156.
|
| [31] |
戴磊. 流分类技术研究[D]. 北京:中科院计算所,2009.
|
| [32] |
SALGARELLI L, GRINGOLI F, KARAGIANNIS T.Comparing Traffic Classifiers[J]. ACM SIGCOMM Computer Communication Review, 2007, 37(3): 65-68.
|
| [33] |
KIM H, CLAFFY K, FOMENKOV M.Internet traffic Classification Demystified: Myths, Caveats and the Best Practices[C]//CoNEXT 2008, Madrid: ACM 2008: 10-12.
|
| [34] |
WILLIAMS N, ZANDER S, ARMITAGE G J.A preliminary performance comparison of five machine learning algorithms for practical IP traffic flow classification[J]. Computer Communication Review, 2006, 36(5): 5-16.
|
| [35] |
KIM H, BARMAN D, KWON T T, et al.NeTraMark: a network traffic classification benchmark[J]. Computer Communication Review, 2011, 41(1): 22-30.
|
| [36] |
COLLINS M, REITER M.Finding peer-to-peer file-sharing using coarse network behaviors[C]//The European Symposium on Research in Computer Security, Germany, 2006: 73-75.
|
| [37] |
DAINOTTI A, PESCAPE A, ROSSI P S.Internet traffic modeling by means of Hidden Markov Models[J]. Computer Networks, 2008, (52): 2645-2662.
|
 ), WU Jin1, XU Shu-juan2
), WU Jin1, XU Shu-juan2