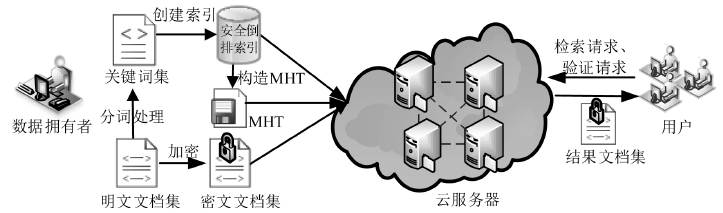
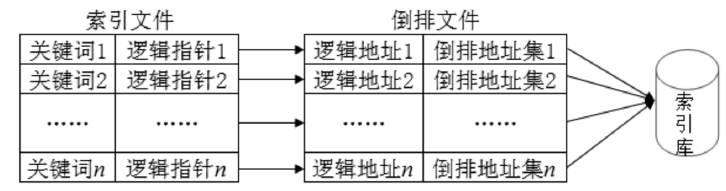
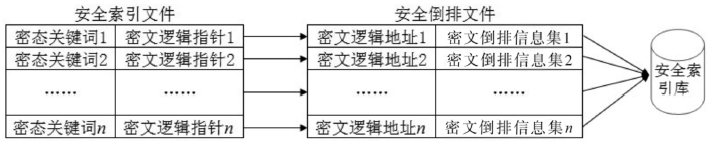
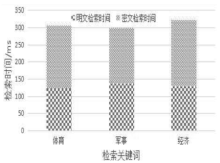
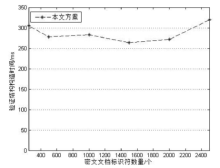
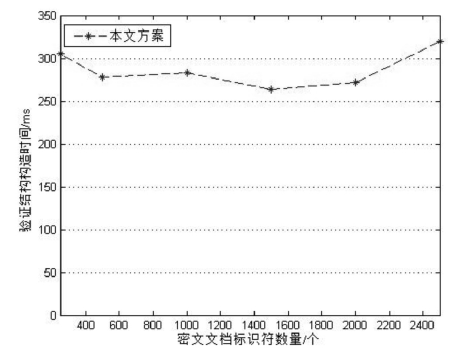
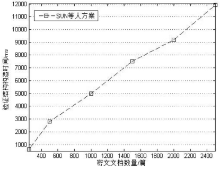
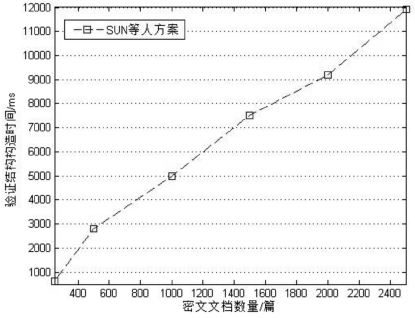
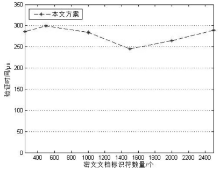
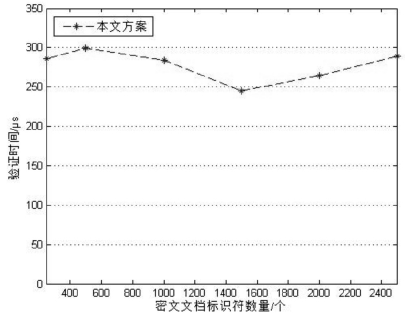
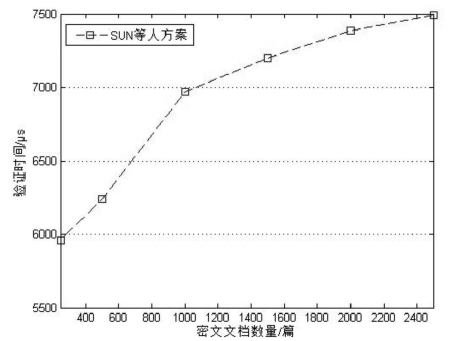
| [1] |
陈明奇,洪学海,王伟,等. 关于网络安全和信息技术发展态势的思考[J].信息网络安全,2015(4):1-4.
|
| [2] |
SONG D X, WAGNER D, PERRIG A.Practical Techniques for Searches on Encrypted Data[C]//IEEE.Proc. of SP '00, May 14-17, 2000. California, USA. NJ: IEEE, 2000: 44-55.
|
| [3] |
GOH E J. Secure Indexes[EB/OL]. , 2016-11-1.
|
| [4] |
CURTMOLA R, GARAY J, KAMARA S, et al.Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[J]. Journal of Computer Security, 2011, 19(5): 895-934.
|
| [5] |
李经纬, 贾春福, 刘哲理, 等. 可搜索加密技术研究综述[J]. 软件学报, 2015, 26(1): 109-128.
|
| [6] |
沈志荣, 薛巍, 舒继武. 可搜索加密机制研究与进展[J]. 软件学报, 2014, 25(4): 880-895
|
| [7] |
DAN B, CRESCENZO G D, OSTROVSKY R, et al.Public Key Encryption with Keyword Search[J]. Lecture Notes in Computer Science, 2004, 3027(16): 506-522.
|
| [8] |
赵洋,包文意,熊虎,等. 云计算里一种陷门无法识别的公钥搜索加密方案[J].信息网络安全,2016(1):1-5.
|
| [9] |
CHAI Qi, GONG Guang. Verifiable Symmetric Searchable Encryption for Semi-honest-but-curious Cloud Servers[EB/OL].,2016-11-1.
|
| [10] |
WANG Jianfeng, MA Hua, TANG Qiang, et al.A New Efficient Verifiable Fuzzy Keyword Search Scheme[J]. Journal of Wireless Mobile Networks, Ubiquitous Computing and Dependable Applications, 2012, 3(4): 61-71.
|
| [11] |
SUN Wenhai, WANG Bing, CAO Ning, et al.Verifiable Privacy-preserving Multi-keyword Text Search in the Cloud Supporting Similarity-based Ranking[J]. IEEE Transactions on Parallel & Distributed Systems, 2013, 99(11): 1-11.
|
| [12] |
MERKLE R C. Method of Providing Digital Signatures: U.S., Patent 4,309,569[P].1982-1-5.
|
| [13] |
MERKLE R C.A Certified Digital Signature[M]//Advances in Cryptology—CRYPTO’89 Proc. Heidelberg: Springer Berlin Heidelberg, 1990: 218-238.
|
| [14] |
HATCHER E, GOSPODNETIC O.Lucene in Action[M]. Greenwich:Manning Publications, 2004.
|
| [15] |
BAEZA-YATES R A, RIBEIRO-NETO B. Modern Information Retrieval[M].Boston: Addison-Wesley Longman Publishing Co., Inc. ,1999.
|
| [16] |
KAMARA S, PAPAMANTHOU C, ROEDER T.Dynamic Searchable Symmetric Encryption[C]//ACM. Proc. of the 2012 ACM Conference on Computer and Communications Security, October 16 - 18, 2012 . Raleigh, North Carolina, USA. New York: ACM, 2012: 965-976.
|
| [17] |
程思嘉,张昌宏,潘帅卿. 基于CP-ABE算法的云存储数据访问控制方案设计[J].信息网络安全,2016(2):1-6.
|
 ), Linbing QIU1,2
), Linbing QIU1,2