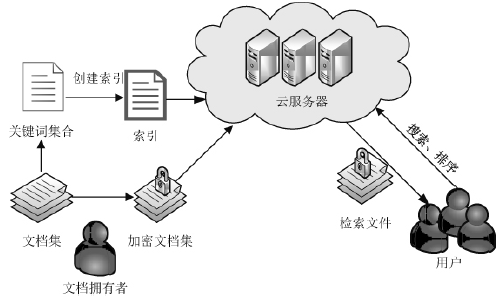
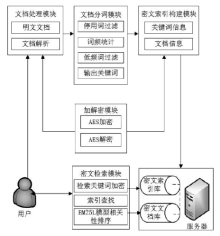
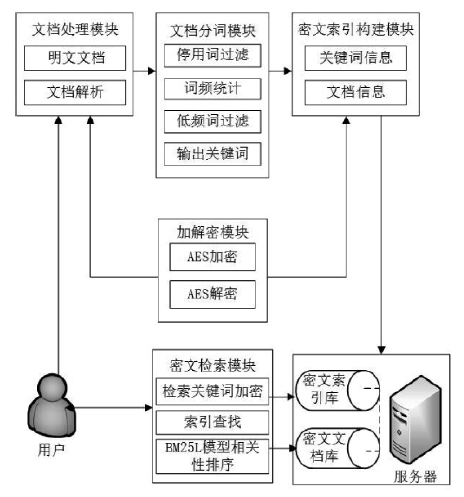
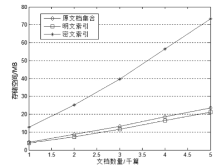
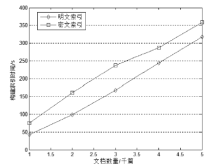
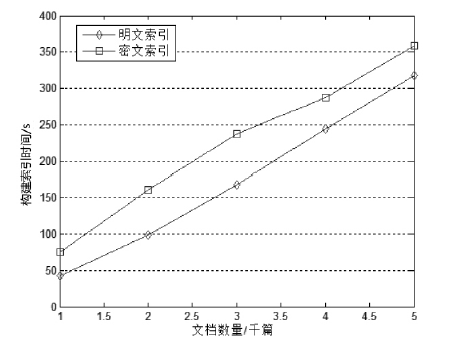
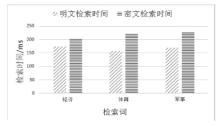
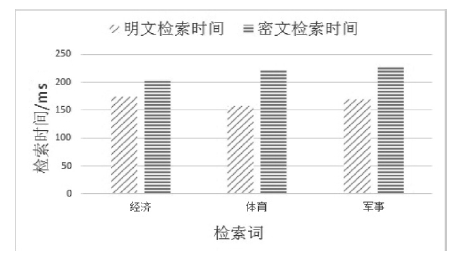
| [1] |
项军政,咸鹤群,田程亮,等. 加密数据库关键词快速检索方法研究[J].信息网络安全,2016(10):28-33.
|
| [2] |
SONG D X, WAGNER D, PERRIG A.Practical Techniques for Searches on Encrypted Data[C]//IEEE.Proc. of SP '00, May 14-17,2000.California,USA.NJ:IEEE, 2000: 44-55.
|
| [3] |
GOH E. J. Secure Indexes[EB/OL]. ,2016-11-1.
|
| [4] |
CHANG Yancheng, MITZENMACHER M.Privacy Preserving Keyword Searches on Remote Encrypted Data[M]// Applied Cryptography and Network Security. Heidelberg: Springer Berlin Heidelberg, 2005:442-455.
|
| [5] |
CURTMOLA R, GARAY J, KAMARA S, et al.Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[J]. Journal of Computer Security, 2011, 19(5):895-934.
|
| [6] |
KUROSAWA K, OHTAKI Y.UC-Secure Searchable Symmetric Encryption[J]. Lecture Notes in Computer Science, 2012(7397):258-274.
|
| [7] |
WANG Cong, CAO Ning, REN Kui, et al.Enabling Secure and Efficient Ranked Keyword Search over Outsourced Cloud Data[J]. IEEE Transactions on Parallel & Distributed Systems, 2012, 23(8):1467-1479.
|
| [8] |
LI Jin, WANG Qian, WANG Cong, et al.Fuzzy Keyword Search over Encrypted Data in Cloud Computing[J]. Infocom, 2010, 4(7):1-5.
|
| [9] |
WANG Cong, REN Kui, YU Shucheng,et al.Achieving Usable and Privacy- assured Similarity Search over Outsourced Cloud Data[C]//IEEE. Proc. of INFOCOM '2012, March 25-30, 2012. Orlando,Florida,USA. NJ:IEEE,2012: 451-459.
|
| [10] |
HUANG Ruwei,GUI Xiaolin,YU Si,et al.Privacy-Preserving Computable Encryption Scheme of Cloud Computing[J]. Chinese Journal of Computers, 2012, 34(12):2391-2402.
|
| [11] |
LIESDONK P V, SEDGHI S, DOUMEN J, et al.Computationally Efficient Searchable Symmetric Encryption[M]// Secure Data Management. Heidelberg :Springer Berlin Heidelberg,2010:87-100.
|
| [12] |
KAMARA S, PAPAMANTHOU C, ROEDER T.Dynamic Searchable Symmetric Encryption[C]//ACM.Proc. of CCS '2012, October 16 - 18, 2012. Raleigh, North Carolina, USA. New York:ACM,2012:965-976.
|
| [13] |
KAMARA S, PAPAMANTHOU C.Parallel and Dynamic Searchable Symmetric Encryption[M]// Financial Cryptography and Data Security. Heidelberg :Springer Berlin Heidelberg,2013:258-274.
|
| [14] |
HAHN F, KERSCHBAUM F.Searchable Encryption with Secure and Efficient Updates[C]//ACM.Proc. Of CCS '2014 , November 3 - 7, 2014. Scottsdale, Arizona, USA. New York:ACM,2014:310-320.
|
| [15] |
STEFANOV E, PAPAMANTHOU C, SHI E. Practical Dynamic Searchable Symmetric Encryption with Small Leakage[EB/OL]. , 2016-11-1.
|
| [16] |
KUROSAWA K, OHTAKI Y.How to Update Documents Verifiably, in Searchable Symmetric Encryption[M]// Cryptology and Network Security.Switzerland:Springer International Publishing, 2013:309-328.
|
| [17] |
NAVEED M, PRABHAKARAN M, GUNTER C A. Dynamic Searchable Encryption via Blind Storage[EB/OL].,2016-11-1.
|
| [18] |
CAO Ning, WANG Cong, LI Ming,et al.Privacy-preserving Multi-keyword Ranked Search over Encrypted Cloud Data[C]//IEEE.Proc. of INFOCOM '2011, April 10-15,2011.Shanghai,China.NJ:IEEE,2011:829-837.
|
| [19] |
SUN Wenhai,WANG Bing,CAO Ning, et al.Privacy-preserving Multi-keyword Text Search in the Cloud Supporting Similarity-based Ranking[J]. IEEE Transactions on Parallel & Distributed Systems, 2013, 25(11):71-81.
|
| [20] |
MOATAZ T, SHIKFA A.Boolean Symmetric Searchable Encryption[C]//ACM.Proc. of ASIACCS '2013, May 8 - 10, 2013. Hangzhou, China.New York:ACM,2013:265-276.
|
| [21] |
王尚平, 刘利军, 张亚玲. 一个高效的基于连接关键词的可搜索加密方案[J]. 电子与信息学报,2013,35(9): 2266-2271.
|
| [22] |
沈志荣, 薛巍, 舒继武. 可搜索加密机制研究与进展[J]. 软件学报, 2014,25(4): 880-895.
|
| [23] |
李经纬, 贾春福, 刘哲理, 等. 可搜索加密技术研究综述[J]. 软件学报, 2015,26(1):109-128.
|
| [24] |
秦志光,包文意,赵洋,等. 云存储中一种模糊关键字搜索加密方案[J]. 信息网络安全,2015(6):7-12.
|
| [25] |
罗刚. 解密搜索引擎技术实战:Lucene&Java精华版[M]. 北京:电子工业出版社,2011.
|
| [26] |
LV Yuanhua,ZHAI Chengxiang.When Documents Are Very Long.Bm25 Fails![C]//ACM. Proc. of SIGIR. 2011, July 24 - 28, 2011. Beijing, China.New York:ACM,2011: 1103-1104.
|
| [27] |
宋衍,周庆,张国双,等. 一种基于数据库服务的密文检索实现[J]. 信息网络安全,2015(9):10-14.
|
 )
)