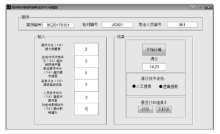
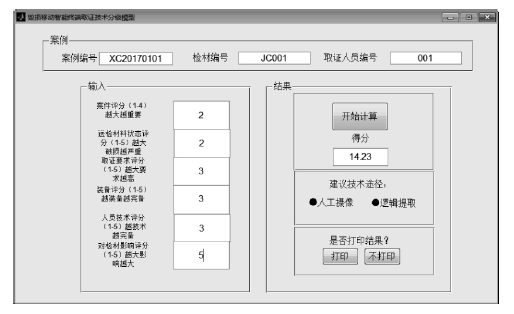
Netinfo Security ›› 2017, Vol. 17 ›› Issue (2): 29-34.doi: 10.3969/j.issn.1671-1122.2017.02.005
• Orginal Article • Previous Articles Next Articles
Research on Hierarchical Model for Defective Mobile Intelligent Teminal Forensic Technology
- 1. Net Supervise Place of Chongqing Municipal Public Security Bureau, Chongqing 401121, China
2. Chongqing University, Chongqing 400044, China
3. Key Lab of Information Network Security of Ministry of Public Security (The Third Research Institute of Ministry of Public Security), Shanghai 201204, China
-
Received:2016-11-01Online:2017-02-20Published:2020-05-12
CLC Number:
Cite this article
Qingyi TIAN, Hong GUO. Research on Hierarchical Model for Defective Mobile Intelligent Teminal Forensic Technology[J]. Netinfo Security, 2017, 17(2): 29-34.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2017.02.005
| [1] | 刘浩阳. Android设备取证研究[J].信息网络安全,2015(9):29-32. |
| [2] | 曹家. 智能移动终端数字取证系统的设计与实现[D]. 北京:北京大学,2012. |
| [3] | Wen-Shen Wuen.Mobile Communications[J]. Security and Privacy, 2006, 6(4): 67-70. |
| [4] | 张笑鲁. Android移动设备的数字取证关键问题研究[D]. 长春:吉林大学,2016. |
| [5] | 杨新宇,王健. 对微云的网络取证研究[J].信息网络安全,2015(3):69-73. |
| [6] | RICK A, AAMBrothers, WAYNE J.NIST Special Publication 8000-101 Revision1[J]. Guidelines on Mobile Device Forensic, 2014 7(8): 15-20. |
| [7] | BREEUWSMA M F.. Forensic Imaging of Embedded Systems Using JTAG (boundary-scan)[J]. Digital Investigation, 2006(3): 32-42. |
| [8] | JANSEN W, DELAITRE A, MOENNER L. Overcoming Impediments to Cell Phone Forensics [C]//IEEE. the 41st Hawaii International Conference on System Sciences 2008,Wailoloa Big Island Hawaii USA, January 7-10, 2008.New York: IEEE, 1530-1605. |
| [9] | 尚士泽,孔祥维,尤新刚. 伪造变造文件数字被动无损取证技术综述[J].信息网络安全,2015(4):62-67. |
| [10] | 郑冬亚. 基于Android平台的手机取证方法研究[D]. 南京:南京邮电大学,2014. |
| [11] | YATES M, CHI H.. A Framework for Designing Benchmarks of Investigating Digital Forensics Tools for Mobile Device[J].Southeast Regional Conference, 2011( 3):179-184. |
| [12] | 刘红,郑健. 基于Android SDK技术的Android智能手机取证系统[J]. 上海电机学院学报, 2015,18(4):244-248. |
| [13] | 顾荣荣. 基于协议逆向分析的智能移动终端通信数据主动取证研究[D].南京:东南大学, 2015. |
| [14] | 金波,吴松洋,熊雄,等. 新型智能终端取证技术研究[J].信息安全学报,2016,1(3):37-51. |
| [15] | 王东. 基于Android的智能终端取证系统设计[D].上海:复旦大学,2013. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||