Netinfo Security ›› 2016, Vol. 16 ›› Issue (4): 55-60.doi: 10.3969/j.issn.1671-1122.2016.04.009
• Orginal Article • Previous Articles Next Articles
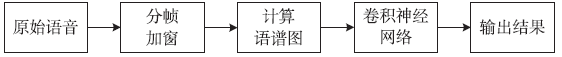
Speaker Recognition Algorithm Based on Convolutional Neural Networks
- 1. College of Big Data and Information Engineering, Guizhou University, Guiyang Guizhou 550025, China
2. Institute of Intelligent Information Processing, Guizhou University, Guiyang Guizhou 550025, China
-
Received:2016-01-18Online:2016-04-20Published:2020-05-13
CLC Number:
Cite this article
Qing HU, Benyong LIU. Speaker Recognition Algorithm Based on Convolutional Neural Networks[J]. Netinfo Security, 2016, 16(4): 55-60.
share this article
| [1] | 王韵琪,俞一彪.自适应高斯混合模型及说话人识别应用[J]. 通信技术, 2014, 47(7): 738-739. |
| [2] | 鲁晓倩. 基于VP树和GMM的说话人识别研究[D].合肥:中国科学技术大学,2014. |
| [3] | ATAL B S.Automatic Recognition of Speaker from Their Voices[J]. IEEE Transaction on Acoustics, Speech, and Signal Processing, 1976, 64(4): 460-475. |
| [4] | DAVIS S B, MERMELSTEIN P.Comparison of Parametric Representations for Monosyllabic Word Recognition in Continuously Spoken Sentences[J]. IEEE Transactions on Acoustics, Speech and Signal Processing, 1980, 28(4): 357-366. |
| [5] | LAWRENCE R.Fundamentals of Speech Recognition[M]. India:Pearson Education India, 2008. |
| [6] | DAVENPORT M R, GARUDADRI H.A Neural Net Acoustic Phonetic Feature Extractor Based on Wavelets[C]// IEEE. Pacific Rim Conference on Communications, Computers and Signal Processing, May 9-10, 1991, Victoria, B. C., CANADA. NJ: IEEE, 1991: 449-452. |
| [7] | 刘鸣,戴蓓倩,李辉,等.基于离散小波变换和感知频域滤波的语音特征参数.[J]电路与系统学报,2000,10(1):21-25. |
| [8] | NÁDAS A, NAHAMOO D, PICHENY M A. Speech Recognition Using Noise-adaptive Prototypes[J]. IEEE Transactions on Acoustics, Speech and Signal Processing, 1989, 37(10): 1495-1503. |
| [9] | COLOMBI J M, RUCK D W, ANDERSON T R, et al.Cohort Selection and Word Grammar Effects for Speaker Recognition[C]//IEEE. International Conference on Acoustics, Speech and Signal Processing, May 7-10, 1996, Atlanta, Georgia. NJ: IEEE, 1996: 85-88. |
| [10] | REYNOLDS D A, CARLSON B A.Text-dependent Speaker Verification Using Decoupled and Integrated Speaker and Speech Recognizers[C]//IEEE. 4th European Conference on Speech Communication and Technology. September 18-21, 1995, Madrid, Spain.NJ: IEEE, 1995: 2201-2204. |
| [11] | SEO J, HONG S, GU J, et al.New Speaker Recognition Feature Using Correlation Dimension[C]// IEEE. International Symposium on Industrial Electronics, June 12-16, 2001,Pusan, Korea.NJ: IEEE, 2001: 505-507. |
| [12] | HOSSAN M A, MEMON S, GREGORY M A.A Novel Approach for MFCC Feature Extraction[C]// IEEE. 4th International Conference on Signal Processing and Communication Systems, December 13-15, 2010, Gold Coast, Australia. NJ: IEEE, 2010: 1-5. |
| [13] | SAKOE H, CHIBA S.Dynamic Programming Algorithm Optimization for Spoken Word Recognition[J]. IEEE Transactions on Acoustics, Speech and Signal Processing, 1978, 26(1): 43-49. |
| [14] | SOONG F K, ROSENBERG A E, JUANG B H, et al.Report: A Vector Quantization Approach to Speaker Recognition[J]. AT&T Technical Journal, 1987, 66(2): 14-26. |
| [15] | RABINER L R.A Tutorial on Hidden Markov Models and Selected Applications in Speech Recognition[J]. Proceedings of the IEEE, 1989, 77(2): 257-286. |
| [16] | OGLESBY J, MASON J S.Optimisation of Neural Models for Speaker Identification[C]//IEEE. International Conference on Acoustics, Speech and Signal Processing, April 3-6, 1990, Albuquerque, New Mexico. NJ: IEEE, 1990: 261-264. |
| [17] | REYNOLDS D A, ROSE R C.Robust Text-independent Speaker Identification Using Gaussian Mixture Speaker Models[J]. IEEE Transactions on Speech and Audio Processing, 1995, 3(1): 72-83. |
| [18] | AUCKENTHALER R, PARRIS E S, CAREY M J.Improving a GMM Speaker Verification System by Phonetic Weighting[C]// IEEE, International Conference on Acoustics, Speech and Signal Processing, March 15-19, 1999, Phoenix, Arizona. NJ: IEEE, 1999: 313-316. |
| [19] | REYNOLDS D A, QUATIERI T F, DUNN R B.Speaker Verification Using Adapted Gaussian Mixture Models[J]. Digital Signal Processing, 2000, 10(1): 19-41. |
| [20] | WU D, LI J, WU H.α-gaussian Mixture Modelling for Speaker Recognition[J]. Pattern Recognition Letters, 2009, 30(6): 589-594. |
| [21] | VENTURINI A, ZAO L, COELHO R.On Speech Features Fusion, α-integration Gaussian Modeling and Multi-Style Training for Noise Robust Speaker Classification[J]. IEEE/ACM Transactions on Audio, Speech, and Language Processing, 2014, 22(12): 1951-1964. |
| [22] | WAN V, CAMPBELL W M.Support Vector Machines for Speaker Verification and Identification[C]//IEEE. Signal Processing Society Workshop, December 11-13, 2000, Sydney, Australia. NJ: IEEE, 2000: 775-784. |
| [23] | 蔡娟,蔡坚勇,廖晓东,等.基于卷积神经网络的手势识别初探[J]. 计算机系统应用,2015,24(4):113-117. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||