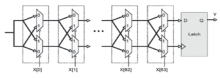
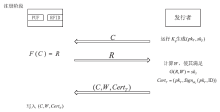
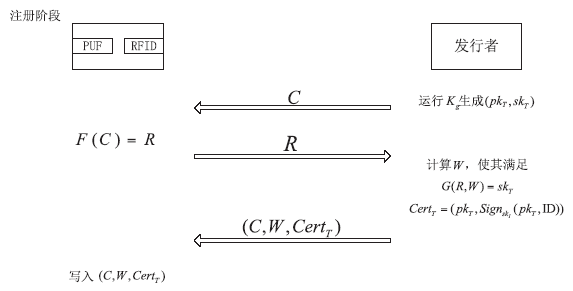
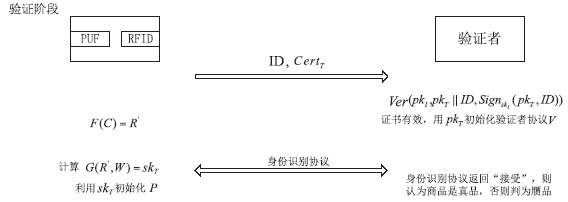
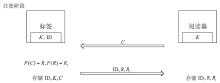
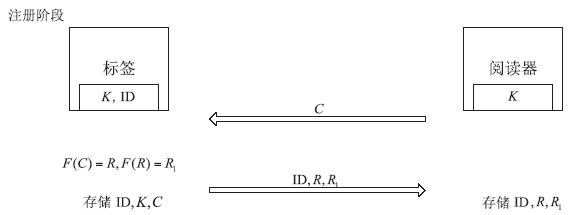
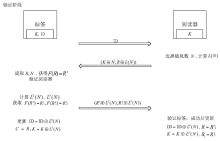
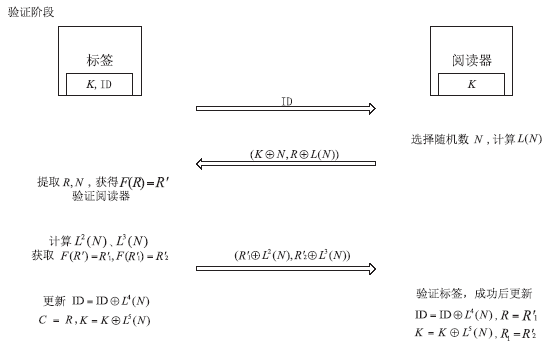
| [1] |
BERNARDI P, GANDINO F, LAMBERTI F, et al.An Anti-counterfeit Mechanism for the Application Layer in Low-cost RFID Devices[C]// IEEE.Circuits and Systems for Communications, 2008. ECCSC 2008. 4th European Conference on, July 10-11,2008. Bucharest, Romania.NJ:IEEE, 2008: 227-231.
|
| [2] |
PAPPU R, RECHT B, TAYLOR J, et al.Physical One-way Functions[J]. Science, 2002, 297(5589): 2026-2030.
|
| [3] |
DEVADAS S, SUH E, PARAL S, et al.Design and Implementation of PUF-based" unclonable" RFID ICs for Anti-counterfeiting and Security Applications[C]// IEEE.RFID, 2008 IEEE International Conference on,April 16-17,2008. Las Vegas, NV,USA.NJ:IEEE, 2008: 58-64.
|
| [4] |
TUYLS P, SCHRIJEN G J, ŠKORIĆ B, et al.Read-proof Hardware from Protective Coatings[J]. Ches, 2006 (4249):369-383.
|
| [5] |
KUMAR S S, GUAJARDO J, MAES R, et al.The Butterfly PUF Protecting IP on Every FPGA[C]// IEEE.Hardware-Oriented Security and Trust, 2008. HOST 2008. IEEE International Workshop on, June 9-9,2008. Anaheim, CA,USA.NJ:IEEE, 2008: 67-70.
|
| [6] |
CHEN Z, ZENG Y, HEFFERMAN G.FiberID: Molecular-level Secret for Identification of Things[C]// IEEE.Parallel Computing Technologies (Parcomptech), 2015 National Conference on, December 3-5,2014.Atlanta, GA,USA.NJ:IEEE, 2015: 84-88.
|
| [7] |
LEE Y K, BATINA L, SINGELEE D, et al. Anti-counterfeiting, Untraceability and Other Security Challenges for RFID Systems: Public-key-based Protocols and Hardware[EB/OL]. , 2010-10-12.
|
| [8] |
OZTIIRK E, HAMMOURI G, SUNAR B.Towards Robust Low Cost Authentication for Pervasive Devices[C]// IEEE.PERCOM '08 Proceedings of the 2008 Sixth Annual IEEE International Conference on Pervasive Computing and Communications, March 17-21, 2008. Hong Kong ,China. Washington:IEEE, 2008: 170-178.
|
| [9] |
BATINA L, GUAJARDO J, KERINS T, et al.Public-key Cryptography for RFID-Tags[C]// IEEE.Pervasive Computing and Communications Workshops, 2007. PerCom Workshops' 07. Fifth Annual IEEE International Conference on, March 19-23,2007. White Plains, NY,USA. Washington:IEEE, 2007: 217-222.
|
| [10] |
TUYLS P, BATINA L. RFID-tags for Anti-Counterfeiting[EB/OL]. ,2015-12-1.
|
| [11] |
JIANG D, CHONG C N.Anti-counterfeiting Using Phosphor PUF[C]//IEEE.Anti-counterfeiting, Security and Identification, 2008. ASID 2008. 2nd International Conference on,August 20-23,2008. Guiyang,China.NJ:IEEE, 2008: 59-62.
|
| [12] |
CHONG C N, JIANG D, ZHANG J, et al.Anti-counterfeiting with a Random Pattern[C]// IEEE.Emerging Security Information, Systems and Technologies, 2008. SECURWARE'08. Second International Conference on, August.25-31,2008. Cap Esterel,France. Washington:IEEE, 2008: 146-153.
|
| [13] |
张紫楠, 刘威, 郭渊博. 物理不可克隆函数综述[J]. 计算机应用, 2012, 32(11): 3115-3120.
|
| [14] |
JIN Yongming, XIN Wei , SUN Huiping ,et al .PUF-based RFID Authentication Protocol against Secret Key Leakage[EB/OL]. ,2015-12-1.
|
| [15] |
DIORIO C J, COOPER S A. RFID Tag Authentication with Public-key Cryptography: U.S. Patent 8,941,469[P].2015-1-27.
|
| [16] |
MOLNAR D, WAGNER D.Privacy and Security in Library RFID: Issues, Practices, and Architectures[C]//ACM.Proceedings of the 11th ACM Conference on Computer and Communications Security,October 25-29,2004. Washington,DC,USA.New York:ACM, 2004: 210-219.
|
| [17] |
JUELS A.RFID Security and Privacy: A research Survey[J]. Selected Areas in Communications, 2006, 24(2): 381-394.
|
| [18] |
XU Xuguang, OU Yuyi, JIE Ling, et al.Lightweight RFID Secure Authentication Protocol Based on PUF[J]. Computer Applications and Software, 2014(11): 78.
|
| [19] |
HE Z, ZOU L.High-efficient Rfid Authentication Protocol Based on Physical Unclonable Function[C]// IEEE.Wireless Communications, Networking and Mobile Computing (WiCOM), 2012 8th International Conference on, September 21-23,2012. Shanghai ,China.NJ:IEEE, 2012: 1-4.
|
| [20] |
LEE Y S, KIM T Y, LEE H J.Mutual Authentication Protocol for Enhanced RFID Security and Anti-counterfeiting[C]// IEEE.Advanced Information Networking and Applications Workshops (WAINA), 2012 26th International Conference on, March 26-29,2012. Fukuoka,Japan. Washington:IEEE, 2012: 558-563.
|
| [21] |
XU Y, HE Z.Design of a Security Protocol for Low-cost Rfid[C]// IEEE.Wireless Communications, Networking and Mobile Computing (WiCOM), 2012 8th International Conference on, September 21-23,2012. Shanghai, China .NJ:IEEE, 2012: 1-3.
|
| [22] |
KARDAŞ S L, ÇELIK S, YILDIZ M, et al.PUF-enhanced Offline RFID Security and Privacy[J]. Journal of Network and Computer Applications, 2012, 35(6): 2059-2067.
|
| [23] |
LEE Y K, BATINA L, VERBAUWHEDE I. EC-RAC (ECDLP Based Randomized Access Control): Provably Secure RFID Authentication Protocol[C]// IEEE.RFID, 2008 IEEE International Conference on, April 16-17,2008. Las Vegas, NV,USA.NJ: IEEE, 2008: 97-104.
|
| [24] |
BRINGER J, CHABANNE H, ICART T. Cryptanalysis of EC-RAC, a RFID Identification Protocol[EB/OL].,2015-12-1.
|
| [25] |
MEHMANDOUST S, ATANI R E.Application of PUF-enabled RFID Tags in Electronic Banking[J]. International Journal of Computer Science & Information Technology, 2011, 3(2): 191-202.
|
| [26] |
BASSIL R, EL-BEAINO W, ITANI W, et al.PUMAP: A PUF-based Ultra-lightweight Mutual-authentication RFID Protocol[J]. International Journal of RFID Security and Cryptography, 2012, 1(1/2): 58-66.
|
| [27] |
SAFKHANI M, BAGHERI N, NADERI M.Security Analysis of a PUF-based RFID Authentication Protocol[J]. IACR Cryptology ePrint Archive, 2011(2011):704.
|
| [28] |
RAY B, CHOWDHURY M, ABAWAIY J.PUF-based Secure Checker Protocol for Networked RFID Systems[C]// IEEE.Open Systems (ICOS), 2014 IEEE Conference on, October 26-28,2014. Subang,Malaysia.NJ: IEEE, 2014: 78-83.
|
 )
)