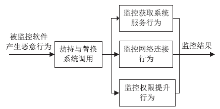
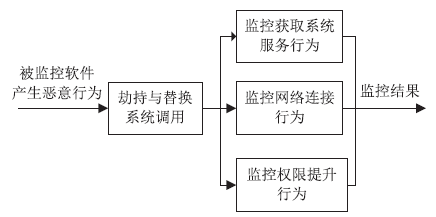
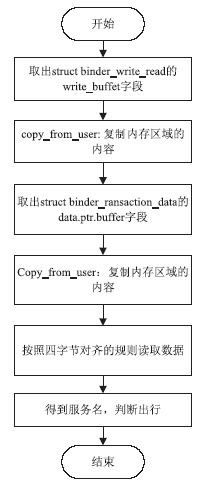
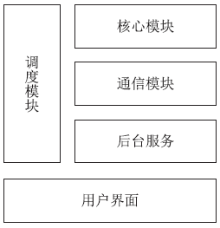
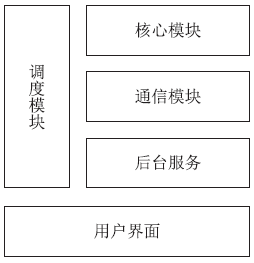
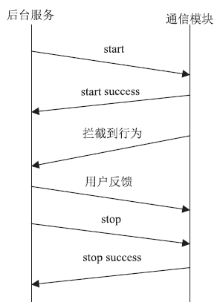
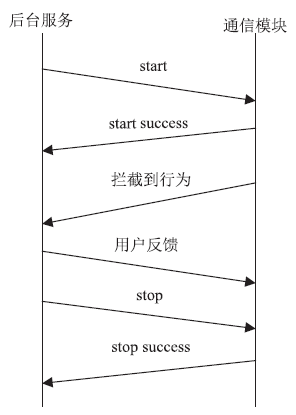
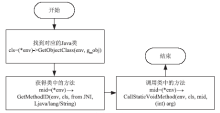
| [1] |
腾讯移动安全实验室. 2015年上半年手机安全报告[EB/OL]. , 2016-02-18.
|
| [2] |
朱筱赟,胡爱群,邢月秀,等. 基于Android平台的移动办公安全方案综述[J]. 信息网络安全,2015(1):76-83.
|
| [3] |
DAI Shuaifu, WEI Tao, ZOU Wei.DroidLogger: Reveal Suspicious Behavior of Android Applications via Instrumentation[C]//IEEE. 7th International Conference on Computing and Convergence Technology, December 3-5, 2012, Seoul. New Jersey: IEEE, 2012: 550-555.
|
| [4] |
BATYUK L, HERPICH M, CAMTEPE S A, et al.Using Static Analysis for Automatic Assessment and Mitigation of Unwanted and Malicious Activities within Android Applications[C]//ACM. 6th International Conference on Malicious and Unwanted Software, October 18-19, 2011, Fajardo. New York: ACM, 2011: 66-72.
|
| [5] |
XU Rubin, SAÏDI H, ANDERSON R. Aurasium: Practical Policy Enforcement for Android Applications[C]//USENIX. 21st USENIX Conference on Security Symposium, August 8-10, 2012, Bellevue. New York: ACM, 2012: 27.
|
| [6] |
PENG Guojun, SHAO Yuru, WANG Taige, et al.Research on Android Malware Detection and Interception Based on Behavior Monitoring[J]. Wuhan University Journal of Natural Sciences, 2012, 17(5): 421-427.
|
| [7] |
张磊,陈兴蜀,任益,等. 一种基于VMM的内核级Rootkit检测技术[J]. 信息网络安全,2015(4):56-61.
|
| [8] |
ISOHARA T, TAKEMORI K, KUBOTA A.Kernel-based Behavior Analysis for Android Malware Detection[C]//Guangdong University of Technology, Beijing Normal University, Hainan Province Institution of Computing. 7th International Conference on Computational Intelligence and Security, December 3-4, 2011, Hainan. New Jersey: IEEE, 2011: 1011-1015.
|
| [9] |
ZHOU Yajin, JIANG Xuxian.Dissecting Android Malware: Characterization and Evolution[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco. New Jersey: IEEE, 2012: 95-109.
|
| [10] |
李汶洋. Android操作系统恶意软件检测技术研究[J]. 信息网络安全,2015(9):62-65.
|
| [11] |
Google. 官方Android开发文档[EB/OL]. , 2016-2-18.
|
| [12] |
DAVIS B, SANDERS B, KHODAVERDIAN A, et al. I-ARM-Droid: A Rewriting Framework for In-App Reference Monitors for Android Applications[EB/OL]. , 2016-1-22.
|
| [13] |
赵光泽,李晖,孟杨. Android平台WebView组件安全及应用加固研究[J]. 信息网络安全,2015(10):61-65.
|
 )
)