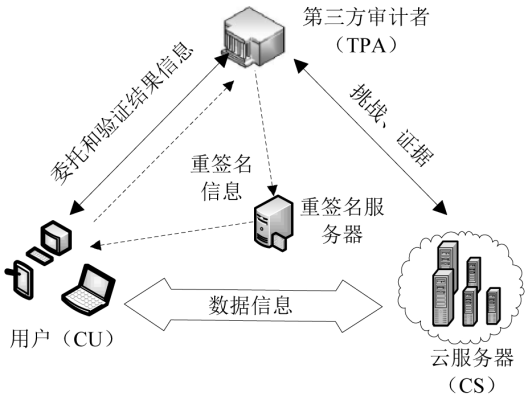
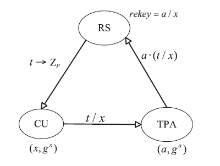
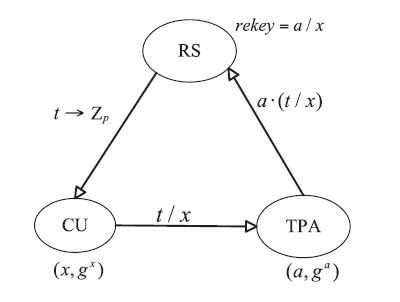
| [1] |
DESWARTE Y, QUISQUATER J J, SAÏDANE A. Remote integrity checking[M]. Integrity and Internal Control in Information Systems VI, Springer US, 2004: 1-11.
|
| [2] |
OPREA A, REITER M K, YANG K.Space-Efficient Block Storage Integrity[C]//Proceedings of the Network and Distributed System Security Symposium, NDSS 2005, California, USA, 2005.
|
| [3] |
GAZZONI FILHO D L, BARRETO P S L M. Demonstrating data possession and uncheatable data transfer[R]. IACR Cryptology ePrint Archive, 2006, 2006: 150.
|
| [4] |
SEBE F, MARTINEZ-BALLESTE A, DESWARTE Y, et al.Time-bounded remote file integrity checking[R]. Technical Report 04429, LAAS, 2004.
|
| [5] |
SCHWARZ T S J, MILLER E L. Store, forget, and check: Using algebraic signatures to check remotely administered storage[C]//IEEE International Conference on Distributed Computing Systems. IEEE Computer Society, 2006: 12.
|
| [6] |
ATENIESE G, KAMARA S, KATZ J.Proofs of storage from homomorphic identification protocols[M]. Advances in Cryptology-ASIACRYPT 2009, Springer Berlin Heidelberg, 2009: 319-333.
|
| [7] |
ATENIESE G, BURNS R, CURTMOLA R, et al.Provable data possession at untrusted stores[C]//Proceedings of the 14th ACM conference on Computer and communications security. Acm, 2007: 598-609.
|
| [8] |
JUELS A, KALISKI JR B S. PORs: Proofs of retrievability for large files[C]//Proceedings of the 14th ACM conference on Computer and communications security. Acm, 2007: 584-597.
|
| [9] |
ATENIESE G, DI PIETRO R, MANCINI L V, et al.Scalable and efficient provable data possession[C]//Proceedings of the 4th international conference on Security and privacy in communication netowrks. ACM, 2008: 9.
|
| [10] |
ERWAY C, KÜPÇÜ A, PAPAMANTHOU C, et al. Dynamic provable data possession[C]//Proceedings of the 16th ACM conference on Computer and communications security. Acm, 2009: 213-222.
|
| [11] |
WANG C, WANG Q, REN K, et al.Privacy-preserving public auditing for data storage security in cloud computing[C]//INFOCOM, 2010 Proceedings IEEE. Ieee, 2010: 1-9.
|
| [12] |
WANG Q, WANG C, LI J, et al.Enabling public verifiability and data dynamics for storage security in cloud computing[M]. Computer Security-ESORICS 2009. Springer Berlin Heidelberg, 2009: 355-370.
|
| [13] |
ZHU Y, WANG H, HU Z, et al.Dynamic audit services for integrity verification of outsourced storages in clouds[C]//Proceedings of the 2011 ACM Symposium on Applied Computing. ACM, 2011: 1550-1557.
|
| [14] |
YANG K, JIA X.An efficient and secure dynamic auditing protocol for data storage in cloud computing[J]. Parallel and Distributed Systems, IEEE Transactions on, 2013, 24(9): 1717-1726.
|
| [15] |
CHANG E C, XU J.Remote integrity check with dishonest storage server[M]. Computer Security-ESORICS 2008. Springer Berlin Heidelberg, 2008: 223-237.
|
| [16] |
SHAH M A, SWAMINATHAN R, BAKER M.Privacy-Preserving Audit and Extraction of Digital Contents[J]. IACR Cryptology ePrint Archive, 2008, 2008: 186.
|
| [17] |
秦志光,吴世坤,熊虎. 云存储服务中数据完整性审计方案综述[J]. 信息网络安全,2014,(7):1-6.
|
| [18] |
SHACHAM H, WATERS B.Compact proofs of retrievability[M].Advances in Cryptology-ASIACRYPT 2008. Springer Berlin Heidelberg, 2008: 90-107.
|
| [19] |
BOWERS K D, JUELS A, OPREA A.HAIL: a high-availability and integrity layer for cloud storage[C]//Proceedings of the 16th ACM conference on Computer and communications security. ACM, 2009: 187-198.
|
| [20] |
BOWERS K D, JUELS A, OPREA A.Proofs of retrievability: Theory and implementation[C]//Proceedings of the 2009 ACM workshop on Cloud computing security. ACM, 2009: 43-54.
|
| [21] |
BONEH D, LYNN B, SHACHAM H.Short signatures from the Weil pairing[M]. Advances in Cryptology—ASIACRYPT 2001. Springer Berlin Heidelberg, 2001: 514-532.
|
| [22] |
MERKLE R C.Protocols for public key cryptosystems[C]//2012 IEEE Symposium on Security and Privacy. IEEE Computer Society, 1980: 122-122.
|
| [23] |
陈亮,陈性元,孙奕,等. 代理重签名研究进展[J]. 计算机应用研究,2014,31(1):23-27.
|
| [24] |
FABER J.Measuring cooperation, conflict, and the social network of nations[J]. Journal of Conflict Resolution, 1987, 31(3): 438-464.
|
 ), XIONG Hu, CHEN Yang
), XIONG Hu, CHEN Yang