Netinfo Security ›› 2024, Vol. 24 ›› Issue (5): 657-666.doi: 10.3969/j.issn.1671-1122.2024.05.001
Previous Articles Next Articles
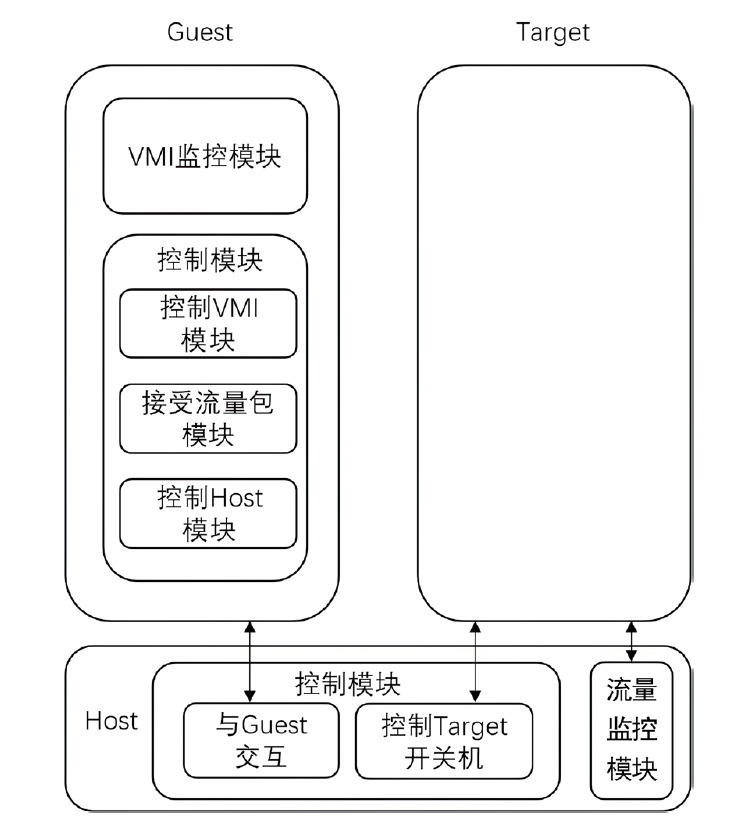
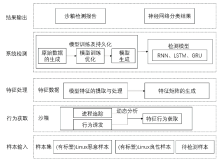
Linux Malicious Application Detection Scheme Based on Virtual Machine Introspection
WEN Weiping( ), ZHANG Shichen, WANG Han, SHI Lin
), ZHANG Shichen, WANG Han, SHI Lin
- School of Software and Microelectronics, Peking University, Beijing 100871, China
-
Received:2023-08-15Online:2024-05-10Published:2024-06-24 -
Contact:WEN Weiping E-mail:weipingwen@pku.edu.cn
CLC Number:
Cite this article
WEN Weiping, ZHANG Shichen, WANG Han, SHI Lin. Linux Malicious Application Detection Scheme Based on Virtual Machine Introspection[J]. Netinfo Security, 2024, 24(5): 657-666.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.05.001
| ROOTKIT | 微步 | 阿里云 沙箱 | VMI Sandbox |
|---|---|---|---|
| Kopycat | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| Subversive | 根据杀毒引擎判别为恶意,但无恶意行为 | 未检测到 | 良性,无恶意行为 |
| Sutekh | 良性,无恶意行为 | 未检测到 | 恶意,修改内核系统调用表 |
| Zero | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| Fops | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| Xor128 | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| spy | 根据杀毒引擎判别为恶意,但无恶意行为 | 未检测到 | 良性,无恶意行为 |
| Diamorphine | 根据杀毒引擎判别为恶意,但无恶意行为 | 未检测到 | 恶意,修改内核系统调用表 |
| Puszek-Rootkit | 良性,无恶意行为 | 未检测到 | 恶意,修改内核系统调用表 |
| LilyOfTheValley | 根据杀毒引擎判别为恶意,但无恶意行为 | 未检测到 | 良性,无恶意行为 |
| Reptile | 良性,无恶意行为 | 未检测到 | 恶意,修改了内核inet_ioctl、load_elf_binary、vfs_read、next_tgid、vfs_statx、audit_alloc符号对应的区域 |
| module.c | 根据杀毒引擎判别为恶意,但无恶意行为 | 未检测到 | 恶意,修改了内核inet_ioctl、load_elf_binary、vfs_read、next_tgid、vfs_statx、audit_alloc符号对应的区域 |
| lkm2_sys_call_table | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| lkm3_backdoor | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| lkm4_hideFile | 良性,无恶意行为 | 未检测到 | 恶意,修改了内核ext4_dir_operations符号对应的区域 |
| lkm5_hide_process | 良性,无恶意行为 | 未检测到 | 良性,无恶意行为 |
| lkm6_hideMod | 良性,无恶意行为 | 未检测到 | 恶意,修改了内核modules_op、kernfs_dir_fops符号对应的区域 |
| [1] | CNCERT/CC. 2020 China Internet Network Security Report[EB/OL]. (2021-07-21)[2023-08-01]. http://www.cac.gov.cn/2021-07/21/c_1628454189500041.htm. |
| 国家计算机网络应急技术处理协调中心. 2020年中国互联网网络安全报告[EB/OL]. (2021-07-21)[2023-08-01]. http://www.cac.gov.cn/2021-07/21/c_1628454189500041.htm. | |
| [2] | CNCERT/CC. Overview of China’s Internet Network Security Situation in 2020[EB/OL]. (2021-05-26)[2023-08-01]. http://www.cac.gov.cn/2021-05/26/c_1623610314656045.htm. |
| 国家计算机网络应急技术处理协调中心. 2020年我国互联网网络安全态势综述[EB/OL]. (2021-05-26)[2023-08-01]. http://www.cac.gov.cn/2021-05/26/c_1623610314656045.htm. | |
| [3] | FANG Zhan, LIU Jun, HUANG Ribian, et al. Research on Multi-Model Android Malicious Application Detection Based on Feature Fusion[C]// IEEE. 2021 4th International Conference on Robotics, Control and Automation Engineering (RCAE). New York: IEEE, 2021: 318-325. |
| [4] | QIU Hongyuan, FERNANDO C. COLON O. Static Malware Detection with Segmented Sandboxing[EB/OL]. (2013-10-22)[2023-08-01]. https://ieeexplore.ieee.org/document/6703695. |
| [5] | ALKHATEEB E M S. Dynamic Malware Detection Using API Similarity[EB/OL]. (2017-09-14)[2023-08-01]. https://ieeexplore.ieee.org/document/8031489. |
| [6] | KEDZIORA M, GAWIN P, SZCZEPANIK M, et al. Malware Detection Using Machine Learning Algorithms and Reverse Engineering of Android Java Code[EB/OL]. (2019-01-29)[2023-08-01]. https://www.researchgate.net/publication/331245836_Malware_Detection_Using_Machine_Learning_Algorithms_and_Reverse_Engineering_of_Android_Java_Code. |
| [7] | BAUMAN E, AYOADE G, LIN Zhiqiang. A Survey on Hypervisor-Based Monitoring: Approaches, Applications, and Evolutions[J]. ACM Computing Surveys (CSUR), 2015, 48(1): 1-33. |
| [8] | LI Baohui, XU Kefu, ZHANG Peng, et al. Research and Application Progress of Virtual Machine Introspection Technology[J]. Journal of Software, 2016, 27(6): 1384-1401. |
| [9] | ROSENBLUM M, GARFINKEL T. Virtual Machine Monitors: Current Technology and Future Trends[J]. Computer, 2005, 38(5): 39-47. |
| [10] |
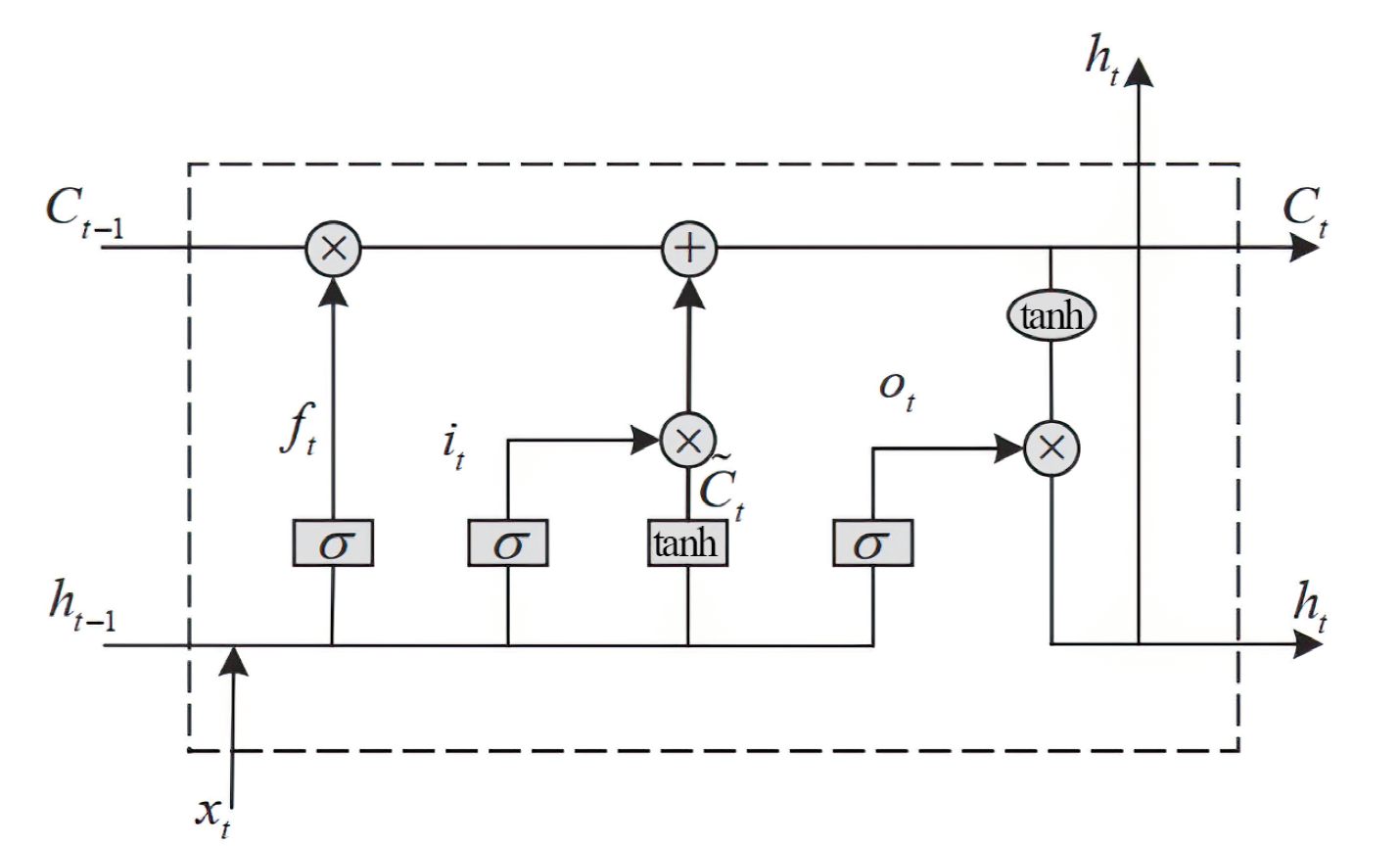
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
doi: 10.1162/neco.1997.9.8.1735 pmid: 9377276 |
| [11] | TAN Liuyan, RUAN Shuhua, YANG Min, et al. Educational Data Classification Based on Deep Learning[J]. Netinfo Security, 2023, 23(3): 96-102. |
| [12] | DEY R, SALEM F M. Gate-Variants of Gated Recurrent Unit (GRU) Neural Networks[EB/OL]. (2017-10-02)[2023-08-01]. https://ieeexplore.ieee.org/document/8053243. |
| [13] | KUMAR R, CHARU S. An Importance of Using Virtualization Technology in Cloud Computing[J]. Global Journal of Computers & Technology, 2015, 1(2): 2623-2634. |
| [14] | ZHANG Jixin, ZHANG Kehuan, QIN Zheng, et al. Sensitive System Calls Based Packed Malware Variants Detection Using Principal Component Initialized Multilayers Neural Networks[J]. Cybersecurity, 2018(10): 21-34. |
| [15] | RABADI D, TEO S G. Advanced Windows Methods on Malware Detection and Classification[C]// ACM. The 36th Annual Computer Security Applications Conference (ACSAC’20). New York: ACM, 2020: 54-68. |
| [1] | HUANG Zilong, ZHAN Dongyang, YE Lin, ZHANG Hongli. A Secure Container Management Approach Based on Virtual Machine Introspection [J]. Netinfo Security, 2022, 22(11): 55-61. |
| [2] | REN Shixuan, WANG Maoyu, ZHAO Hui. An Improved Method of Backdoor Attack in DNN [J]. Netinfo Security, 2021, 21(5): 82-89. |
| [3] | LIU Heng, WU Dexin, XU Jian. Generating Universal Adversarial Perturbations with Generative Adversarial Networks [J]. Netinfo Security, 2020, 20(5): 57-64. |
| [4] | Jinghao LIU, Siping MAO, Xiaomei FU. Intrusion Detection Model Based on ICA Algorithm and Deep Neural Network [J]. Netinfo Security, 2019, 19(3): 1-10. |
| [5] | Jian ZHANG, Wenzhen LI, Liangyi GONG. Research on Malicious E-mail Detection Technology [J]. Netinfo Security, 2018, 18(9): 80-85. |
| [6] | Jian ZHANG, Cheng GAO, Liangyi GONG, Zhaojun GU. Research on Virtual Machine Introspection Technology [J]. Netinfo Security, 2017, 17(9): 63-68. |
| [7] | Khan Safi Qamas GUL, Jize YIN, Limin PAN, Senlin LUO. Research on the Algorithm of Named Entity Recognition Based on Deep Neural Network [J]. Netinfo Security, 2017, 17(10): 29-35. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||