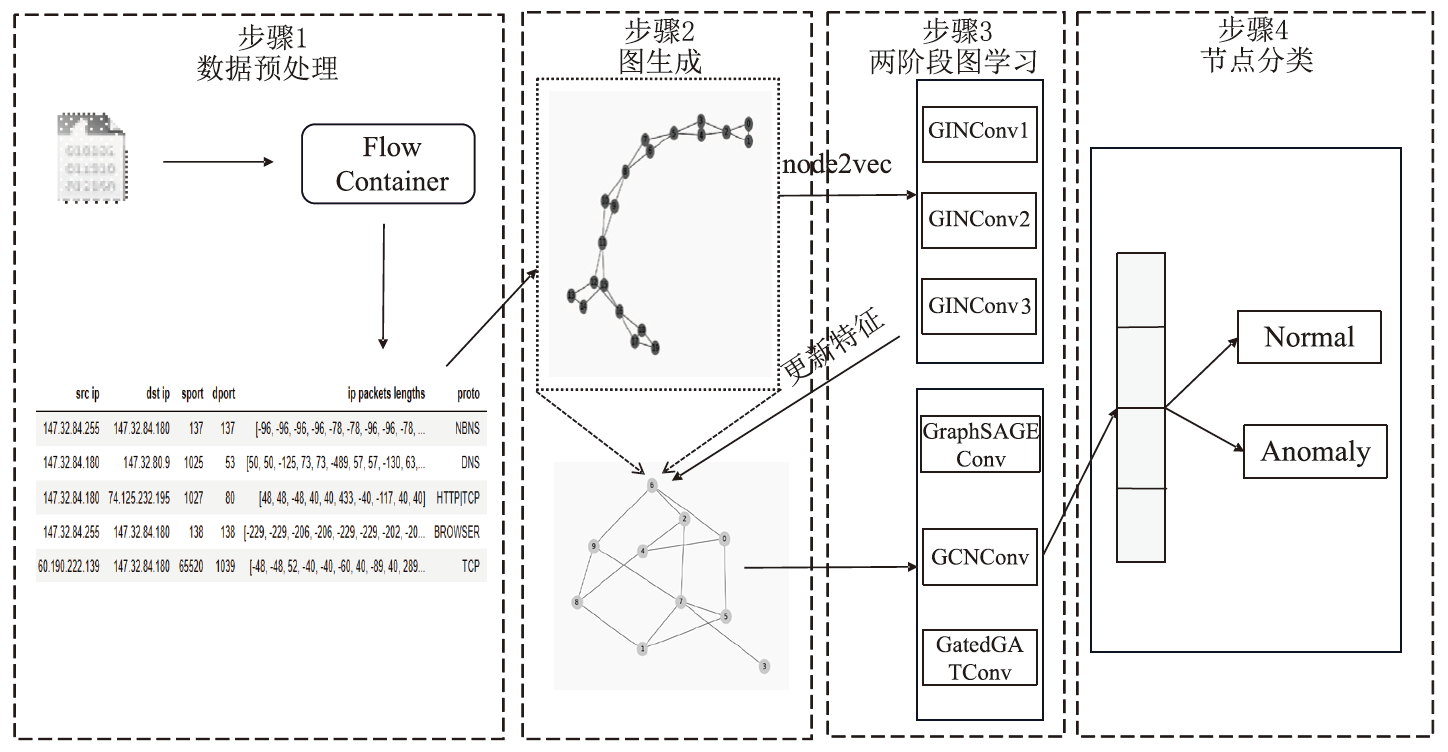
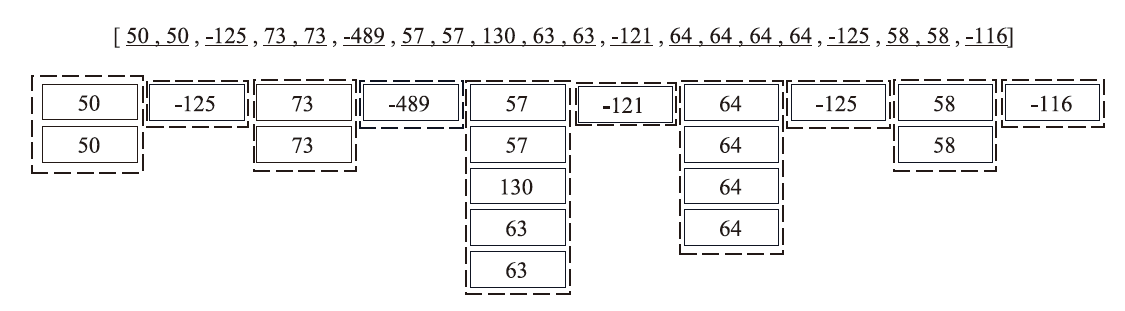
Netinfo Security ›› 2024, Vol. 24 ›› Issue (12): 1933-1947.doi: 10.3969/j.issn.1671-1122.2024.12.011
Previous Articles Next Articles
Automated Botnet Detection Method Based on Two-Stage Graph Learning
ZHANG Xuan1,2, WAN Liang1,2( ), LUO Heng1,2, YANG Yang1,2
), LUO Heng1,2, YANG Yang1,2
- 1. College of Computer Science and Technology, Guizhou University, Guiyang 550025, China
2. State Key Laboratory of Public Big Data, Guizhou University, Guiyang 550025, China
-
Received:2024-09-11Online:2024-12-10Published:2025-01-10
CLC Number:
Cite this article
ZHANG Xuan, WAN Liang, LUO Heng, YANG Yang. Automated Botnet Detection Method Based on Two-Stage Graph Learning[J]. Netinfo Security, 2024, 24(12): 1933-1947.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.12.011
| 序号 | 持续时间/hrs | 数据包/个 | 网络流/条 | 数据大小/GB | 僵尸网络 |
|---|---|---|---|---|---|
| 1 | 6.15 | 71971482 | 2824637 | 52.0 | Neris |
| 2 | 4.21 | 71851300 | 1808123 | 60.0 | Neris |
| 3 | 66.85 | 167730395 | 4710639 | 121.0 | Rbot |
| 4 | 4.21 | 62089135 | 1121077 | 53.0 | Rbot |
| 5 | 11.63 | 4481167 | 129833 | 37.6 | Virut |
| 6 | 2.18 | 38764357 | 558920 | 30.0 | Menti |
| 7 | 0.38 | 7467139 | 114078 | 5.8 | Sogou |
| 8 | 19.50 | 155207799 | 2954231 | 123.0 | Murlo |
| 9 | 5.18 | 115415321 | 2753885 | 94.0 | Neris |
| 10 | 4.75 | 90389782 | 1309792 | 73.0 | Rbot |
| 11 | 0.26 | 6337202 | 107252 | 5.2 | Rbot |
| 12 | 1.21 | 13212268 | 325472 | 8.3 | NSIS.ay |
| 13 | 16.36 | 50888256 | 1925150 | 34.0 | Virut |
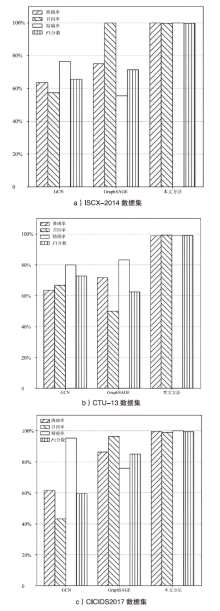
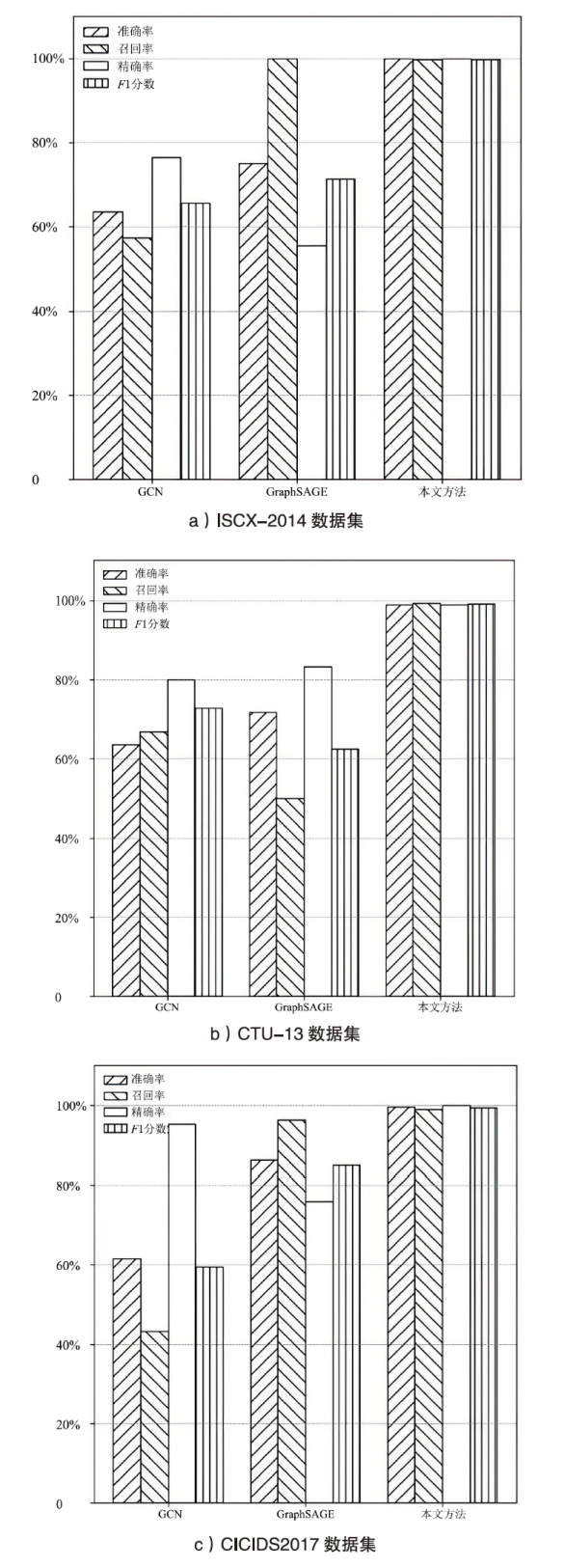
| 数据集 | 方法 | 准确率 | 召回率 | 精确率 | F1分数 |
|---|---|---|---|---|---|
| ISCX-2014 数据集 | No-Flowgraph | 95.90% | 92.93% | 98.20% | 95.49% |
| No-Commgraph | 91.14% | 94.05% | 96.10% | 95.06% | |
| 本文方法 | 99.88% | 99.76% | 99.88% | 99.72% | |
| 场景1,2,9(CTU-13) | No-Flowgraph | 92.66% | 96.30% | 94.70% | 95.49% |
| No-Commgraph | 96.28% | 97.03% | 98.44% | 97.73% | |
| 本文方法 | 98.81% | 99.26% | 98.82% | 99.04% | |
| 场景3,4,10,11(CTU-13) | No-Flowgraph | 92.45% | 92.11% | 94.21% | 93.15% |
| No-Commgraph | 95.58% | 98.38% | 91.55% | 94.84% | |
| 本文方法 | 98.62% | 97.10% | 96.63% | 96.87% | |
| 场景5,13 (CTU-13) | No-Flowgraph | 81.00% | 81.12% | 79.68% | 80.40% |
| No-Commgraph | 85.56% | 89.18% | 87.33% | 88.24% | |
| 本文方法 | 91.97% | 93.66% | 91.63% | 92.64% | |
| 场景6 (CTU-13) | No-Flowgraph | 77.44% | 76.50% | 86.08% | 81.01% |
| No-Commgraph | 78.94% | 86.25% | 85.41% | 85.83% | |
| 本文方法 | 89.13% | 89.70% | 88.65% | 89.17% | |
| 场景7 (CTU-13) | No-Flowgraph | 92.40% | 94.44% | 94.17% | 94.31% |
| No-Commgraph | 95.44% | 96.59% | 94.36% | 95.46% | |
| 本文方法 | 97.65% | 98.27% | 97.77% | 98.02% | |
| 场景8 (CTU-13) | No-Flowgraph | 91.47% | 97.53% | 92.58% | 94.99% |
| No-Commgraph | 96.42% | 96.01% | 97.14% | 96.57% | |
| 本文方法 | 97.77% | 98.00% | 97.39% | 97.70% | |
| 场景12 (CTU-13) | No-Flowgraph | 79.38% | 76.48% | 80.03% | 78.22% |
| No-Commgraph | 86.30% | 80.94% | 83.53% | 86.30% | |
| 本文方法 | 92.90% | 95.82% | 92.77% | 94.27% | |
| CICIDS2017 数据集 | No-Flowgraph | 97.77% | 98.00% | 97.39% | 97.70% |
| No-Commgraph | 99.48% | 98.80% | 99.66% | 99.21% | |
| 本文方法 | 99.59% | 98.87% | 99.92% | 99.38% |
| 数据集 | 方法 | 准确率 | 召回率 | 精确率 | F1分数 |
|---|---|---|---|---|---|
| ISCX-2014 数据集 | LSTM-RF[ | — | 98.00% | 98.00% | 98.00% |
| BiLSTM-GAN[ | 85.51% | 82.38% | 91.55% | 86.72% | |
| NNM[ | 89.38% | — | 92.50% | 88.97% | |
| CNN_LSTM[ | 92.81% | — | 85.67% | 92.25% | |
| GCN-ATT[ | 99.08% | 99.09% | 98.18% | — | |
| 本文方法 | 99.88% | 99.76% | 99.88% | 99.72% | |
| CTU-13 数据集 | FFS-HTTP[ | 98.03% | 97.26% | 98.79% | 97.93% |
| k-NN[ | 92.20% | 90.00% | 93.00% | 91.51% | |
| SVM-RBF[ | 86.95% | 84.87% | 85.03% | 84.95% | |
| MLP[ | 84.58% | 86.91% | 81.95% | 83.88% | |
| bot-DL[ | 96.80% | 96.30% | 96.60% | 96.40% | |
| 本文方法 | 98.81% | 99.26% | 98.82% | 99.04% |
| [1] | XING Ying, SHU Hui, ZHAO Hao, et al. Survey on Botnet Detection Techniques: Classification, Methods, and Evaluation[J]. Mathematical Problems in Engineering, 2021, 2021: 1-24. |
| [2] | SHARAFALDIN I, GHARIB A, LASHKARI A H, et al. BotViz: A Memory Forensic-Based Botnet Detection and Visualization Approach[C]// IEEE. 2017 International Carnahan Conference on Security Technology (ICCST). New York: IEEE, 2017: 1-8. |
| [3] | CREECH G, HU Jiankun. A Semantic Approach to Host-Based Intrusion Detection Systems Using Contiguousand Discontiguous System Call Patterns[J]. IEEE Transactions on Computers, 2014, 63(4): 807-819. |
| [4] | GARRE J T, GILPÉREZ M, RUIZ-MARTÍNEZ A. A Novel Machine Learning-Based Approach for the Detection of SSH Botnet Infection[J]. Future Generation Computer Systems, 2021, 115: 387-396. |
| [5] | HOSSAIN M I, ESHRAK S, AUVIK M J, et al. Efficient Feature Selection for Detecting Botnets Based on Network Traffic and Behavior Analysis[C]// ACM. 7th International Conference on Networking, Systems and Security. New York: ACM, 2020: 56-62. |
| [6] | XIA Qinyu, DONG Shi, PENG Tao. An Abnormal Traffic Detection Method for IoT Devices Based on Federated Learning and Depthwise Separable Convolutional Neural Networks[C]// IEEE. 2022 IEEE International Performance, Computing, and Communications Conference (IPCCC). New York: IEEE, 2022: 352-359. |
| [7] | ZHOU Jiawei, XU Zhiying, RUSH A M, et al. Automating Botnet Detection with Graph Neural Networks[EB/OL]. (2020-03-13)[2024-03-04]. https://arxiv.org/abs/2003.06344v1. |
| [8] | HU Xiaoyan, GAO Wenjie, CHENG Guang, et al. Toward Early and Accurate Network Intrusion Detection Using Graph Embedding[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5817-5831. |
| [9] | VELASCO-MATA J, GONZÁLEZ-CASTRO V, FIDALGO E, et al. Real-Time Botnet Detection on Large Network Bandwidths Using Machine Learning[EB/OL]. (2023-03-15)[2024-03-04]. https://pubmed.ncbi.nlm.nih.gov/36922641/. |
| [10] | BANSAL A, MAHAPATRA S. A Comparative Analysis of Machine Learning Techniques for Botnet Detection[C]// ACM. Proceedings of the 10th International Conference on Security of Information and Networks. New York: ACM, 2017: 91-98. |
| [11] | LETTERI I, DELLA PENNA G, CAIANIELLO P. Feature Selection Strategies for HTTP Botnet Traffic Detection[C]// IEEE. 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW). New York: IEEE, 2019: 202-210. |
| [12] | IBRAHIM W N H, ANUAR S, SELAMAT A, et al. Multilayer Framework for Botnet Detection Using Machine Learning Algorithms[J]. IEEE Access, 2021, 9: 48753-48768. |
| [13] | SHAHHOSSEINI M, MASHAYEKHI H, REZVANI M. A Deep Learning Approach for Botnet Detection Using Raw Network Traffic Data[EB/OL]. [2024-03-04]. https://link.springer.com/article/10.1007/s10922-022-09655-7. |
| [14] | LUO Fuhua, ZHANG Aixin. Botnet Detection Technology Based on Deep Learning[J]. Communications Technology, 2020, 53(1): 174-179. |
| 罗扶华, 张爱新. 基于深度学习的僵尸网络检测技术研究[J]. 通信技术, 2020, 53(1): 174-179. | |
| [15] |
ZOU Futai, TAN Yue, WANG Lin, et al. Botnet Detection Based on Generative Adversarial Network[J]. Journal on Communications, 2021, 42(7): 95-106.
doi: 10.11959/j.issn.1000-436x.2021082 |
|
邹福泰, 谭越, 王林, 等. 基于生成对抗网络的僵尸网络检测[J]. 通信学报, 2021, 42(7): 95-106.
doi: 10.11959/j.issn.1000-436x.2021082 |
|
| [16] | XIA Yuanjun, DONG Shi, PENG Tao, et al. Wireless Network Abnormal Traffic Detection Method Based on Deep Transfer Reinforcement Learning[C]// IEEE. 2021 17th International Conference on Mobility, Sensing and Networking (MSN). New York: IEEE, 2021: 528-535. |
| [17] | DONG Shi, XIA Yuanjun, PENG Tao. Network Abnormal Traffic Detection Model Based on Semi-Supervised Deep Reinforcement Learning[J]. IEEE Transactions on Network and Service Management, 2021, 18(4): 4197-4212. |
| [18] | PEKTAŞ A, ACARMAN T. Botnet Detection Based on Network Flow Summary and Deep Learning[EB/OL]. (2018-07-25)[2024-03-04]. https://doi.org/10.1002/nem.2039. |
| [19] | WANG Wei, SHANG Yaoyao, HE Yongzhong, et al. BotMark: Automated Botnet Detection with Hybrid Analysis of Flow-Based and Graph-Based Traffic Behaviors[J]. Information Sciences, 2020, 511: 284-296. |
| [20] | LIN Honggang, ZHANG Yunli, GUO Nanxin, et al. P2P Botnet Detection Method Based on Graph Neural Network[J]. Advanced Engineering Sciences, 2022, 54(2): 65-72. |
| 林宏刚, 张运理, 郭楠馨, 等. 基于图神经网络的P2P僵尸网络检测方法[J]. 工程科学与技术, 2022, 54(2): 65-72. | |
| [21] | GITHUB. FlowContainer[EB/OL]. [2024-03-04]. https://github.com/jmhIcoding/flowcontainer. |
| [22] | AL-NAAMI K, CHANDRA S, MUSTAFA A, et al. Adaptive Encrypted Traffic Fingerprinting with Bi-Directional Dependence[C]// ACM. Proceedings of the 32nd Annual Conference on Computer Security Applications. New York: ACM, 2016: 177-188. |
| [23] | GROVER A, LESKOVEC J. Node2vec: Scalable Feature Learning for Networks[C]// ACM. Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2016: 855-864. |
| [24] | BIGLAR B E, HADIAN J H, STAKHANOVA N, et al. Towards Effective Feature Selection in Machine Learning-Based Botnet Detection Approaches[C]// IEEE. 2014 IEEE Conference on Communications and Network Security. New York: IEEE, 2014: 247-255. |
| [25] | GARCÍA S, GRILL M, STIBOREK J, et al. An Empirical Comparison of Botnet Detection Methods[J]. Computers & Security, 2014, 45: 100-123. |
| [26] | SHARAFALDIN I, HABIBI LASHKARI A, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[C]// IEEE. International Conference on Information Systems Security & Privacy. New York: IEEE, 2018: 108-116. |
| [27] | ZHAO D, TRAORE I, SAYED B, et al. Botnet Detection Based on Traffic Behavior Analysis and Flow Intervals[J]. Computers & Security, 2013, 39: 2-16. |
| [28] | SHIRAVI A, SHIRAVI H, TAVALLAEE M, et al. Toward Developing a Systematic Approach to Generate Benchmark Datasets for Intrusion Detection[J]. Computers & Security, 2012, 31(3): 357-374. |
| [29] | HANG H, WEI Xuetao, FALOUTSOS M, et al. Entelecheia: Detecting P2P Botnets in Their Waiting Stage[C]// IEEE. 2013 IFIP Networking Conference. New York: IEEE, 2013: 1-9. |
| [1] | CHEN Xiaojing, TAO Yang, WU Baiqi, DIAO Yunfeng. Optimization Gradient Perception Adversarial Attack for Skeleton-Based Action Recognition [J]. Netinfo Security, 2024, 24(9): 1386-1395. |
| [2] | XU Ruzhi, ZHANG Ning, LI Min, LI Zixuan. Research on a High Robust Detection Model for Malicious Software [J]. Netinfo Security, 2024, 24(8): 1184-1195. |
| [3] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [4] | ZHANG Guanghua, LIU Yichun, WANG He, HU Boning. Defense Scheme for Removing Deep Neural Network Backdoors Based on JSMA Adversarial Attacks [J]. Netinfo Security, 2024, 24(4): 545-554. |
| [5] | XU Zirong, GUO Yanping, YAN Qiao. Malicious Software Adversarial Defense Model Based on Feature Severity Ranking [J]. Netinfo Security, 2024, 24(4): 640-649. |
| [6] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [7] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [8] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [9] | ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning [J]. Netinfo Security, 2024, 24(2): 272-281. |
| [10] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [11] | YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence [J]. Netinfo Security, 2024, 24(11): 1615-1623. |
| [12] | WEI Jinxia, HUANG Xizhang, FU Yuhao, LI Jing, LONG Chun. Mining Traffic Detection Method Based on Global Feature Learning [J]. Netinfo Security, 2024, 24(10): 1506-1514. |
| [13] | ZHANG Zihan, LAI Qingnan, ZHOU Changling. Survey on Fuzzing Test in Deep Learning Frameworks [J]. Netinfo Security, 2024, 24(10): 1528-1536. |
| [14] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [15] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||