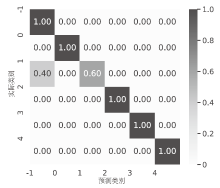
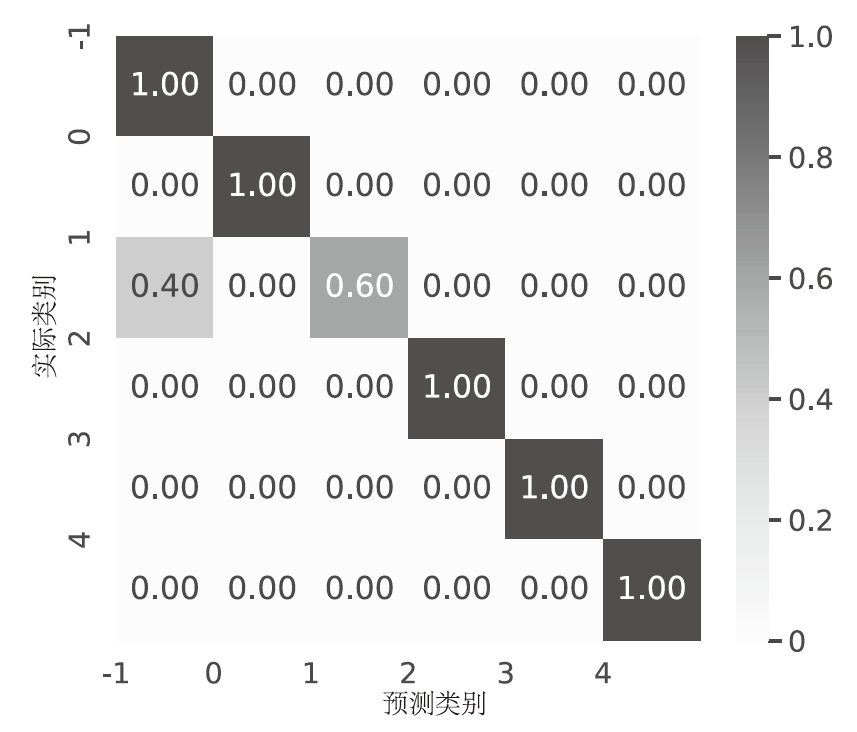
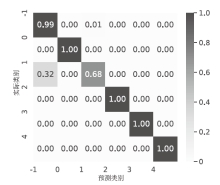
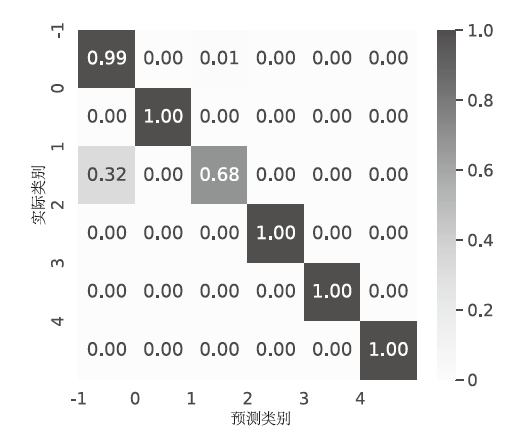
Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1615-1623.doi: 10.3969/j.issn.1671-1122.2024.11.001
Previous Articles Next Articles
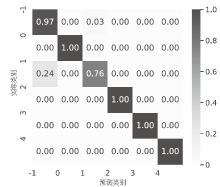
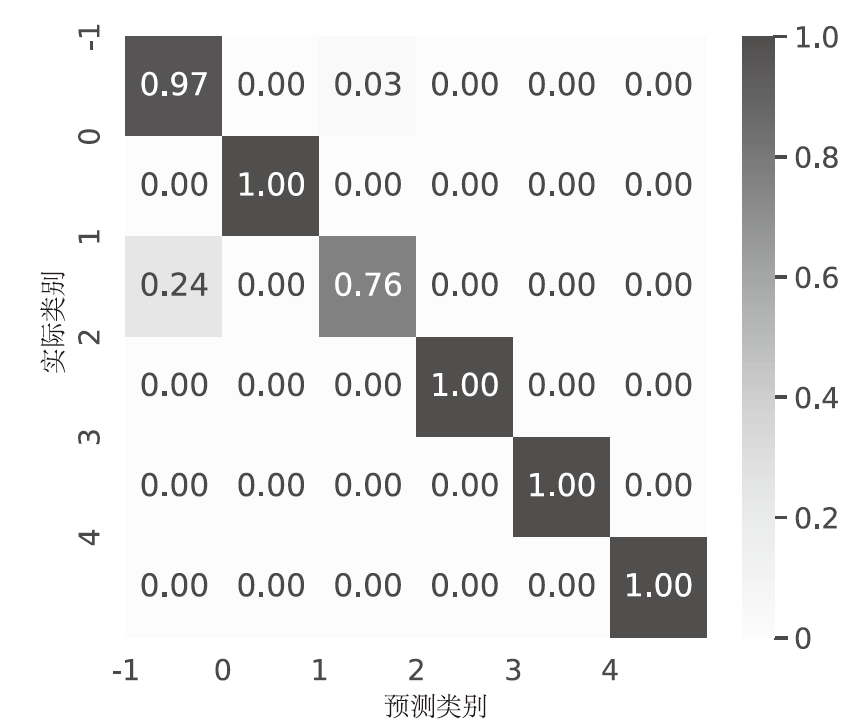
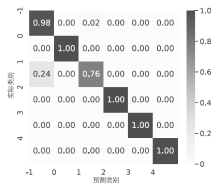
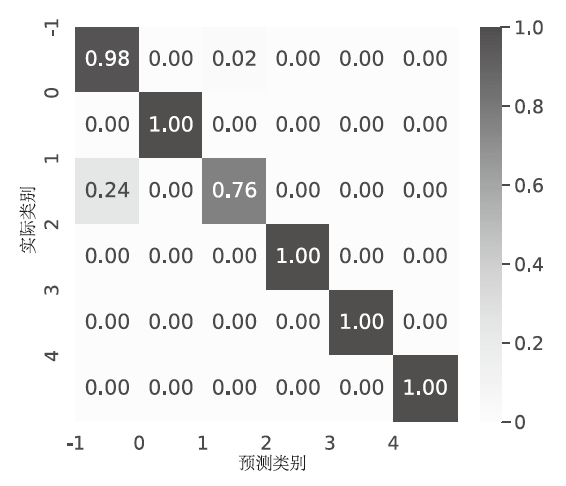
Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence
YIN Jie1( ), CHEN Pu1, YANG Guinian2, XIE Wenwei3, LIANG Guangjun1
), CHEN Pu1, YANG Guinian2, XIE Wenwei3, LIANG Guangjun1
- 1. Department of Computer Information and Cybersecurity, Jiangsu Police Institute, Nanjing 210031, China
2. Network Security Support Team of Nanjing Public Security Bureau, Nanjing 210005, China
3. Trend Micro(China) Nanjing Branch, Nanjing 210012, China
-
Received:2024-08-10Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence[J]. Netinfo Security, 2024, 24(11): 1615-1623.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.11.001
| [1] | KONG Dezhang, CHEN Xiang, WU Chunming, et al. RDefender: A Lightweight and Robust Defense against Flow Table Overflow Attacks in SDN[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 9436-9451. |
| [2] | LI Ziqiang, SUN Hong, XIA Pengfei, et al. A Proxy Attack-Free Strategy for Practically Improving the Poisoning Efficiency in Backdoor Attacks[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 9730-9743. |
| [3] | ANTONAKAKIS M, APRIL T, BAILEY M, et al. Understanding the Mirai Botnet[C]//ACM. 26th USENIX Conference on Security Symposium. New York: ACM, 2017: 1093-1110. |
| [4] | China Mobile Communications Research Institute. White Paper on Future Application Scenarios and Capabilities of 6G Internet of Things(2023)[EB/OL]. [2024-06-10]. http://cmri.chinamobile.com/wp-content/uploads/2023/08/6G物联网未来应用场景及能力白皮书.pdf. |
| 中国移动通信研究院. 6G物联网未来应用场景及能力白皮书(2023年)[EB/OL]. [2024-06-10]. http://cmri.chinamobile.com/wp-content/uploads/2023/08/6G物联网未来应用场景及能力白皮书.pdf. | |
| [5] | ELIYAN L F, DI PIETRO R. DoS and DDoS Attacks in Software Defined Networks: A Survey of Existing Solutions and Research Challenges[J]. Future Generation Computer Systems, 2021, 122: 149-171. |
| [6] | FANG Xin, WAN Yang, WEN Xia, et al. DDoS Attacks Based on Protocol Analysis of Network Intrusion Detection System Research[J]. Netinfo Security, 2012, 12(4): 36-38. |
| 方欣, 万扬, 文霞, 等. 基于协议分析技术的网络入侵检测系统中DDoS攻击的方法研究[J]. 信息网络安全, 2012, 12(4):36-38. | |
| [7] | MOHAMMAD R M A, ALSMADI M K, ALMARASHDEH I, et al. An Improved Rule Induction Based Denial of Service Attacks Classification Model[EB/OL]. [2024-08-01]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820302819?via%3Dihub. |
| [8] | HAJIMAGHSOODI M, JALILI R. RAD: A Statistical Mechanism Based on Behavioral Analysis for DDoS Attack Countermeasure[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2732-2745. |
| [9] | LIU Xinqian, REN Jiadong, HE Haitao, et al. Low-Rate DDoS Attacks Detection Method Using Data Compression and Behavior Divergence Measurement[EB/OL]. [2024-07-20]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820303801?via%3Dihub. |
| [10] | SEIFOUSADATI A, GHASEMSHIRAZI S, FATHIAN M. A Machine Learning Approach for DDoS Detection on IoT Devices[EB/OL]. [2024-08-01]. https://arxiv.org/abs/2110.14911v1. |
| [11] | MUGHAID A, ALQAHTANI A, ALZU’BI S, et al. Utilizing Machine Learning Algorithms for Effectively Detection IoT DDoS Attacks[C]// Springer. International Conference on Advances in Computing Research. Heidelberg: Springer, 2023: 617-629. |
| [12] | GAO Neng, FENG Dengguo, XIANG Ji. A Data-Mining Based DoS Detection Technique[J]. Chinese Journal of Computers, 2006, 29(6): 944-951. |
| 高能, 冯登国, 向继. 一种基于数据挖掘的拒绝服务攻击检测技术[J]. 计算机学报, 2006, 29(6):944-951. | |
| [13] | LI Junfeng, TANG Wei. Application of Feedforward Neural Network Algorithm in DDoS Detection[J]. China Science and Technology Information, 2009(17): 115-116. |
| 李俊峰, 汤伟. 前馈神经网络算法在DDoS检测中的应用[J]. 中国科技信息, 2009(17):115-116. | |
| [14] | DUAN Weiheng. Research and Analysis of Anti-DDOS Market Based on Cloud Computing Technology[D]. Beijing: Beijing University of Posts and Telecommunications, 2012. |
| 段伟恒. 基于云计算技术的抗DDOS市场研究分析[D]. 北京: 北京邮电大学, 2012. | |
| [15] | WANG Chunhui. Analysis of Six Legal Systems on Cyber Security Law[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2017, 37(1): 1-13. |
| 王春晖. 《网络安全法》六大法律制度解析[J]. 南京邮电大学学报(自然科学版), 2017, 37(1):1-13. | |
| [16] | HOSSAIN M S, RAGHUNATHAN V. AEGIS: A Lightweight Firewall for Wireless Sensor Networks[C]//Springer. Distributed Computing in Sensor Systems:6th IEEE International Conference. Heidelberg: Springer, 2010: 258-272. |
| [17] | ZHANG Yu, WEN Jiangtao. An IoT Electric Business Model Based on the Protocol of Bitcoin[C]//IEEE. 2015 18th International Conference on Intelligence in Next Generation Networks. New York: IEEE, 2015: 184-191. |
| [18] | XIE Yunzhou. The Evolution of NB-IoT Standard System and Development of Internet of Things Industry[J]. Chinese Journal on Internet of Things, 2018, 2(1): 76-87. |
|
解运洲. NB-IoT标准体系演进与物联网行业发展[J]. 物联网学报, 2018, 2(1):76-87.
doi: 10.11959/j.issn.2096-3750.2018.00044 |
|
| [19] | CAO Jichang, WANG Jiayi, CHEN Mingqi. Research and Application of Key Technologies of Intelligent Site System Based on BIM+GIS+IoT Technology[J]. Construction Science and Technology, 2020(S1): 74-77. |
| 曹吉昌, 王佳仪, 陈明琪. 基于BIM+GIS+IoT技术的智慧工地系统关键技术研究及应用[J]. 建设科技, 2020(S1):74-77. | |
| [20] | KANG Shilong, DU Zhongyi, LEI Yongmei, et al. Overview of Industrial Internet of Things[J]. Internet of Things Technologies, 2013, 3(6): 80-82. |
| 康世龙, 杜中一, 雷咏梅, 等. 工业物联网研究概述[J]. 物联网技术, 2013, 3(6):80-82. | |
| [21] | YIN Zhouping, TAO Bo. Technologies of the Industrial Internet of Things and Its Applications[M]. Beijing: Tsinghua University Press, 2022. |
| 尹周平, 陶波. 工业物联网技术及应用[M]. 北京: 清华大学出版社, 2022. |
| [1] | ZHANG Xuewang, CHEN Siyu, LUO Xinyue, LEI Zhitao, XIE Haofei. Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT [J]. Netinfo Security, 2024, 24(9): 1352-1363. |
| [2] | LI Zhihua, CHEN Liang, LU Xulin, FANG Zhaohui, QIAN Junhao. Lightweight Detection Method for IoT Mirai Botnet [J]. Netinfo Security, 2024, 24(5): 667-681. |
| [3] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| [4] | QI Han, WANG Jingtong, ABDULLAH Gani, GONG Changqing. Robustness of Variational Quantum Convolutional Neural Networks Based on Random Quantum Layers [J]. Netinfo Security, 2024, 24(3): 363-373. |
| [5] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [6] | CHEN Baogang, ZHANG Yi, YAN Song. Research on Multi-Factor Continuous Trustworthy Identity Authentication for Users in Civil Aviation Air Traffic Control Operational Information Systems [J]. Netinfo Security, 2024, 24(11): 1632-1642. |
| [7] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [8] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [9] | ZHANG Zihan, LAI Qingnan, ZHOU Changling. Survey on Fuzzing Test in Deep Learning Frameworks [J]. Netinfo Security, 2024, 24(10): 1528-1536. |
| [10] | SA Qirui, YOU Weijing, ZHANG Yifei, QIU Weiyang, MA Cunqing. A Survey of Ownership Protection Schemes for Federated Learning Models [J]. Netinfo Security, 2024, 24(10): 1553-1561. |
| [11] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [12] | YIN Chunyong, JIANG Yiyang. Differential Privacy Trajectory Protection Model Based on Personalized Spatiotemporal Clustering [J]. Netinfo Security, 2024, 24(1): 80-92. |
| [13] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [14] | WANG Juan, ZHANG Chong, GONG Jiaxin, LI Jun’e. Review of Fuzzing Based on Machine Learning [J]. Netinfo Security, 2023, 23(8): 1-16. |
| [15] | XU Chungen, XUE Shaokang, XU Lei, ZHANG Pan. Efficient Neural Network Inference Protocol Based on Secure Two-Party Computation [J]. Netinfo Security, 2023, 23(7): 22-30. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||