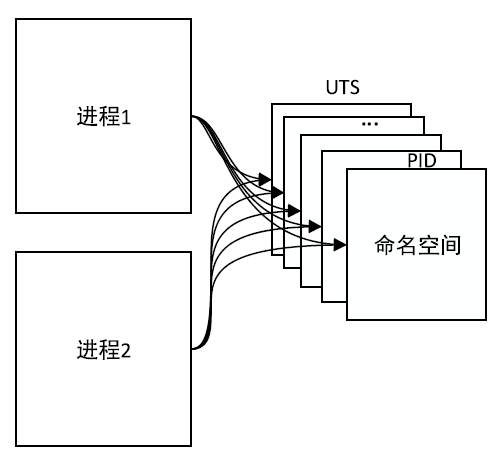
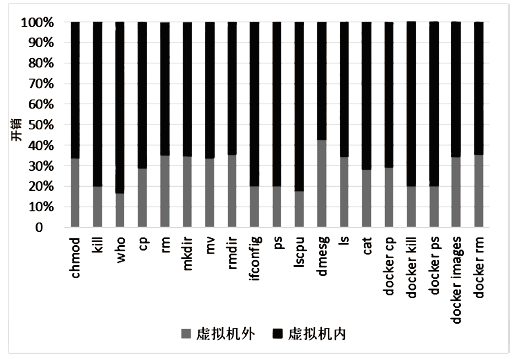
| [1] |
LIN Xin, LEI Lingguang, WANG Yuewu, et al. A Measurement Study on Linux Container Security: Attacks and Countermeasures[C]// ACSAC.Proceedings of the 34th Annual Computer Security Applications Conference. New York: ACSAC, 2018: 418-429.
|
| [2] |
WANG Xu, ZHAO Peng. Kata Containers: The Speed of Containers, the Security of VMs[EB/OL]. [2022-05-29].
|
| [3] |
GOOGLE. gViosr: A Container Sandbox Runtime Focused on Security, Efficiency, and Ease of Use[EB/OL]. [2022-05-29].
|
| [4] |
GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. [2022-05-29]. .
|
| [5] |
ZHAN Dongyang, YE Lin, FANG Binxing, et al. Cfwatcher: A Novel Target-Based Real-Time Approach to Monitor Critical Files Using Vmi[C]// IEEE. 2016 IEEE International Conference on Communications (ICC). New York:IEEE, 2016: 1-6.
|
| [6] |
ZHAN Dongyang, YE Lin, FANG Binxing, et al. Protecting Critical Files Using Target-Based Virtual Machine Introspection Approach[J]. IEICE Transactions on Information and Systems, 2017, 100(10): 2307-2318.
|
| [7] |
HIZVER J, CHIUEH T. Real-Time Deep Virtual Machine Introspection and Its Applications[N]// Proceedings of the 10th ACM SIGPLAN/SIGOPS International Conference on Virtual Execution Environments, 2014-03-14.
|
| [8] |
FU Yangchun, ZENG Junyuan, LIN Zhiqiang. HYPERSHELL: A Practical Hypervisor Layer Guest {OS} Shell for Automated {In-VM} Management[C]// USENIX. 2014 USENIX Annual Technical Conference (USENIX ATC 14). California:USENIX, 2014: 85-96.
|
| [9] |
GU Zhongshu, DENG Zhui, XU Dongyan, et al. Process Implanting: A New Active Introspection Framework for Virtualization[C]// IEEE. 2011 IEEE 30th International Symposium on Reliable Distributed Systems. New York: IEEE, 2011: 147-156.
|
| [10] |
FU Yangchun, LIN Zhiqiang. Exterior: Using a Dual-Vm Based External Shell for Guest-Os Introspection, Configuration, and Recovery[J]. Acm Sigplan Notices, 2013, 48(7): 97-110.
|
| [11] |
ZHAN Dongyang, YE Lin, FANG Binxing, et al. SAVM: A Practical Secure External Approach for Automated In-VM Management[EB/OL]. [2022-05-29]. https://onlinelibrary.wiley.com/doi/full/10.1002/cpe.4482.
|
| [12] |
SULTAN S, AHMAD I, DIMITRIOU T. Container Security: Issues, Challenges, and the Road Ahead[J]. IEEE Access, 2019, 7: 52976-52996.
doi: 10.1109/ACCESS.2019.2911732
URL
|
| [13] |
TOMAR A, JEENA D, MISHRA P, et al. Docker Security: A Threat Model, Attack Taxonomy and Real-Time Attack Scenario of Dos[C]// IEEE. 2020 10th International Conference on Cloud Computing, Data Science & Engineering (Confluence). New York:IEEE, 2020: 150-155.
|
| [14] |
YU Dongjin, JIN Yike, ZHANG Yuqun, et al. A Survey on Security Issues in Services Communication of Microservices-Enabled Fog Applications[EB/OL]. [2022-05-29]. https://onlinelibrary.wiley.com/doi/abs/10.1002/cpe.4436.
|
| [15] |
WATADA J, ROY A, KADIKAR R, et al. Emerging Trends, Techniques and Open Issues of Containerization: A Review[J]. IEEE Access, 2019, 7: 152443-152472.
doi: 10.1109/ACCESS.2019.2945930
URL
|
| [16] |
COMBE T, MARTIN A, DI PIETOR R. To Docker or Not to Docker: A Security Perspective[J]. IEEE Cloud Computing, 2016, 3(5): 54-62.
|
| [17] |
GAO Xing, GU Zhongshu, KAYAALP M, et al. Container-Leaks: Emerging Security Threats of Information Leakages in Container Clouds[C]// IEEE. 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York:IEEE, 2017: 237-248.
|
| [18] |
GAO Xing, STEENKAMER B, GU Zhongshu, et al. A Study on the Security Implications of Information Leakages in Container Clouds[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 18(1): 174-191.
doi: 10.1109/TDSC.2018.2879605
URL
|
| [19] |
GAO Xing, GU Zhongshu, LI Zhengfa, et al. Houdini’s Escape: Breaking the Resource Rein of Linux Control Groups[C]// ACM. Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 1073-1086.
|
| [20] |
NAM J, LEE S, SEO H, et al. BASTION: A Security Enforcement Network Stack for Container Networks[C]// USENIX. 2020 USENIX Annual Technical Conference (USENIX ATC 20). California:USENIX, 2020: 81-95.
|
| [21] |
LEI Lingguang, SUN Jianhua, SUN Kun, et al. SPEAKER: Split-Phase Execution of Application Containers[C]// Springer. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment. Heidelberg: Springer, 2017: 230-251.
|
| [22] |
WAN Zhiyuan, LO D, XIA Xin, et al. Mining Sandboxes for Linux Containers[C]//IEEE. 2017 IEEE International Conference on Software Testing, Verification and Validation (ICST). New York:IEEE, 2017: 92-102.
|
| [23] |
BARLEY S, BASIL Z, KOHANIM S, et al. Secure Yet Usable: Protecting Servers and Linux Containers[J]. IBM Journal of Research and Development, 2016, 60(4): 1-10.
|
| [24] |
GHAYAMNIA S, PALIT T, BENAMEUR A, et al. Confine: Automated System Call Policy Generation for Container Attack Surface Reduction[C]//Springer. 23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2020). Heidelberg:Springer, 2020: 443-458.
|
| [25] |
AMAZON. Secure and Fast Microvms for Serverless Computing[EB/OL]. [2022-05-29].
|
| [26] |
DOLAN-GAVITT B, LEEK T, ZHIVICH M, et al. Virtuoso: Narrowing the Semantic Gap in Virtual Machine Introspection[C]// IEEE. 2011 IEEE Symposium on Security and Privacy. New York: IEEE, 2011: 297-312.
|
| [27] |
CARBONE M, CONOVER M, MONTAGUE B, et al. Secure and Robust Monitoring of Virtual Machines through Guest-Assisted Introspection[J]. International Workshop on Recent Advances in Intrusion Detection, 2012, 7462: 22-41.
|
| [28] |
WU Rui, CHEN Ping, LIU Peng, et al. System Call Redirection: A Practical Approach to Meeting Real-World Virtual Machine Introspection Needs[C]// IEEE. 2014 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2014: 574-585.
|
 ), ZHAN Dongyang, YE Lin, ZHANG Hongli
), ZHAN Dongyang, YE Lin, ZHANG Hongli