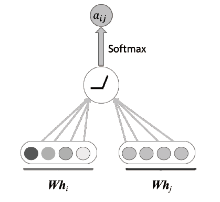
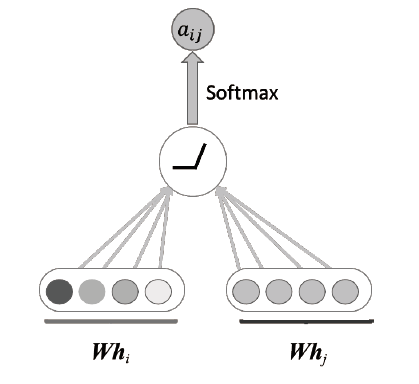
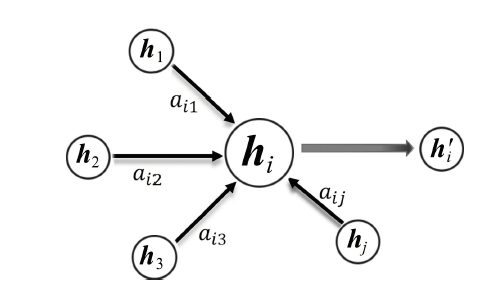
| [1] |
MA Chunguang, AN Jing, BI Wei, et al. Smart Contract in Blockchain[J]. Netinfo Security, 2018, 18(11): 8-17.
|
|
马春光, 安婧, 毕伟, 等. 区块链中的智能合约[J]. 信息网络安全, 2018, 18(11): 8-17.
|
| [2] |
BIAN Lingyu, ZHANG Linlin, ZHAO Kai, et al. Ethereum Malicious Account Detection Method Based on LightGBM[J]. Netinfo Security, 2020, 20(4): 73-84.
|
|
边玲玉, 张琳琳, 赵楷, 等. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4):73-84.
|
| [3] |
CHEN Weili, ZHENG Zibin, CUI Jiahui, et al. Detecting Ponzi Schemes on Ethereum: Towards Healthier Blockchain Technology[C]// Springer. Proceedings of the 2018 World Wide Web Conference. Heidelberg: Springer, 2018: 1409-1418.
|
| [4] |
TAO Feng, WANG Jinsong, LIU Duobin, et al. Bitcoin User Address Classification Method Based on Improved Random Forest[J]. Journal of Tianjin University of Technology, 2022, 38(1): 53-58.
|
|
陶峰, 王劲松, 吕垛斌, 等. 基于改进随机森林的比特币用户地址分类方法[J]. 天津理工大学学报, 2022, 38(1): 53-58.
|
| [5] |
LIU Xiao, TANG Zaiyang, LI Peng, et al. A Graph Learning Based Approach for Identity Inference in DApp Platform Blockchain[J]. IEEE Transactions on Emerging Topics in Computing, 2022, 10(1): 438-449.
|
| [6] |
KANEZASHI H, SUZUMURAT, LIU Xin, et al. Ethereum Fraud Detection with Heterogeneous Graph Neural Networks[EB/OL]. (2022-07-04)[2022-07-08]. https://arxiv.org/abs/2203.12363.
|
| [7] |
VELICKOVIC P, CUCURULL G, CASANOVA A, et al. Graph Attention Networks[C]// Springer. International Conference on Learning Representations. Heidelberg: Springer, 2018: 1050-1062.
|
| [8] |
XU D, RUAN C, KORPROGLU E, et al. Inductive Representation Learning on Temporal Graphs[EB/OL]. (2020-10-19)[2022-07-08]. https://arxiv.org/abs/2002.07962.
|
| [9] |
ZHOU Jun, ZHANG Zhiqiang, CAO Yuetian, et al. A Geography and Time Aware Representation Learning Framework[J]. CAAI Transactions on Intelligent Systems, 2021, 16(5): 909-917.
|
|
周俊, 张志强, 曹月恬, 等. 地理位置和时间感知的表示学习框架[J]. 智能系统学报, 2021, 16(5): 909-917
|
| [10] |
CHEN Liang, PENG Jiaying, LIU Yang, et al. Phishing Scams Detection in Ethereum Transaction Network[J]. ACM Transactions on Internet Technology, 2021, 21(1): 1-16.
|
| [11] |
ZHOU Jiajun, HU Chenkai, CHI Jianlei, et al. Behavior-Aware Account De-Anonymization on Ethereum Interaction Graph[EB/OL]. [2022-07-08]. https://arxiv.org/abs/2203.09360.
|
| [12] |
LI Panpan, XIE Yunyi, XU Xinyao, et al. Phishing Fraud Detection on Ethereum Using Graph Neural Network[EB/OL]. (2022-04-18)[2022-07-08]. https://arxiv.org/abs/2204.08194
|
| [13] |
KINGMA P, BA J. Adam: A Method for Stochastic Optimization[EB/OL]. (2017-01-30)[2022-07-08]. https://arxiv.org/abs/1412.6980.
|
| [14] |
LIANG Fei. Intelligent Detection Method of Malicious URL Based on Multi Group Attention Mechanism[J]. Netinfo Security, 2020, 20(1): 18-22.
|
|
梁飞. 基于多分组注意力机制的恶意URL智能检测方法[J]. 信息网络安全, 2020, 20(1):18-22.
|
| [15] |
WU Jiajing, LIU Jieli, LIN Dan, et al. Blockchain Transaction Networks:A Survey[J]. Acta Scientiarum Naturalium Universitatis Sunyatseni, 2021, 60(5): 1-12.
|
|
吴嘉婧, 刘洁利, 林丹, 等. 区块链交易网络研究综述[J]. 中山大学学报(自然科学版), 2021, 60(5):1-12.
|
 ), SHANG Gangchuan2, TIAN Yangjun3
), SHANG Gangchuan2, TIAN Yangjun3