| [1] |
HE Dan. Common Methods and Prevention Strategies of Network Attack[J]. Information and Computer (Theoretical Edition), 2015, 16(8):127-128.
|
|
贺丹. 网络攻击的常用手法及防范策略[J]. 信息与电脑(理论版), 2015, 16(8):127-128.
|
| [2] |
WANG Feng, ZHANG Xiao, XU Yuan. Domestic Status and Development Suggestions of Web Application Firewall[J]. China Information Security, 2016, 7(12):80-83.
|
|
王峰, 张骁, 许源. Web应用防火墙的国内现状与发展建议[J]. 中国信息安全, 2016, 7(12):80-83.
|
| [3] |
WANG Juan. "Internet Plus" Multidimensional Mode Research and Analysis[J]. Wireless Interconnect Technology, 2015, 15(8):46-47.
|
|
王娟. “互联网+”的多维模式研究与分析[J]. 无线互联科技, 2015, 15(8):46-47.
|
| [4] |
JING Shan. Research on Web Application Vulnerability Detection Technology Based on Penetration Test[D]. Beijing: Beijing University of Posts and Telecommunications, 2015.
|
|
净山. 基于渗透测试的Web应用漏洞检测技术研究[D]. 北京:北京邮电大学, 2015.
|
| [5] |
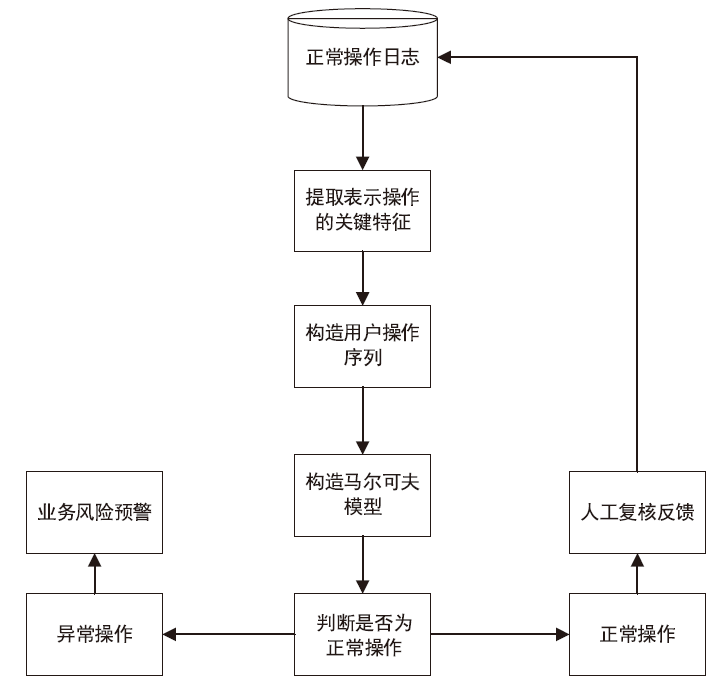
LIU Hui, CAI Lidong. Anomaly Detection of Linux Process Behavior by Markov Chain[J]. Computer Engineering, 2005, 31(12):161-162, 180.
doi: 10.1007/s00366-013-0338-6
URL
|
|
刘辉, 蔡利栋. 用马尔可夫链对Linux进程行为的异常检测[J]. 计算机工程, 2005, 31(12):161-162,180.
|
| [6] |
TANG Xiaoyong. Algorithm Research on Markov Chain Problem[D]. Chengdu:University of Electronic Science and technology of China, 2015.
|
|
唐小勇. 马尔可夫链问题算法研究[D]. 成都:电子科技大学, 2015.
|
| [7] |
NIE Duzhong, CHEN Hua, MI Chengji, et al. Modified Algorithm of Markov Chain State Probability Transfer Matrix[J]. Statistics and Decision, 2013, 29(3):14-17.
|
|
聂笃忠, 陈桦, 米承继, 等. 马尔可夫链状态概率转移矩阵修正算法[J]. 统计与决策, 2013, 29(3):14-17.
|
| [8] |
HAN Guanghui, ZENG Cheng. A Note on the Definition of Finite Automata[J]. Computer and Information Technology, 2015, 23(4):1-4.
|
|
韩光辉, 曾诚. 关于有限自动机定义的一个注记[J]. 电脑与信息技术, 2015, 23(4):1-4.
|
| [9] |
HU Zheqian, YANG Lu. United Endpoint Management Research and Application[J]. Information Security Technology and Application, 2011, 2(1):60-61.
|
|
胡喆骞, 杨璐. 终端安全管理系统的研究与应用[J]. 信息安全与技术, 2011, 2(1):60-61.
|
| [10] |
LIN Xiaodong, YANG Yixian. Web Firewall Technology[J]. Telecommunication Science, 1997, 42(3):43-45.
|
|
林晓东, 杨义先. 网络防火墙技术[J]. 电信科学, 1997, 42(3):43-45.
|
| [11] |
YIN Shuling, HU Lan, WEN Jing. Web Application Firewall and its Detection Technology[J]. Network Security Technology and Application, 2016, 16(7):34-35.
|
|
尹淑玲, 胡岚, 温静. Web应用防火墙及其检测技术[J]. 网络安全技术与应用, 2016, 16(7):34-35.
|
| [12] |
TANG Weijie, HUANG Wenming. Discussion on Data Security Management System in the Era of Big Data[J]. Cyberspace Security, 2016, 7(7):58-61.
|
|
唐玮杰, 黄文明. 大数据时代下的数据安全管理体系讨论[J]. 网络空间安全, 2016, 7(7):58-61.
|
| [13] |
ZHANG Yi. Design and Implementation of Website Integrated Monitoring System[D]. Xi’an: Xidian University, 2013.
|
|
张一. 网站综合监控系统的设计与实现[D]. 西安:西安电子科技大学, 2013.
|
| [14] |
WU Jinghua, ZHOU Qihai, LIU Jiafen. Research on Anti Fraud Monitoring Model of Information Security in Modern Payment System[J]. Computer Science, 2010, 37(12):76-80.
|
|
吴敬花, 周启海, 刘家芬. 现代支付系统信息安全的反欺诈监测模型研究[J]. 计算机科学, 2010, 37(12):76-80.
|
| [15] |
FENG Dan. Research on Web Application Business Logic Vulnerability Detection Technology[D]. Hangzhou: Zhejiang Gongshang University, 2017.
|
|
冯丹. Web应用业务逻辑漏洞检测技术研究[D]. 杭州:浙江工商大学, 2017.
|
 )
)