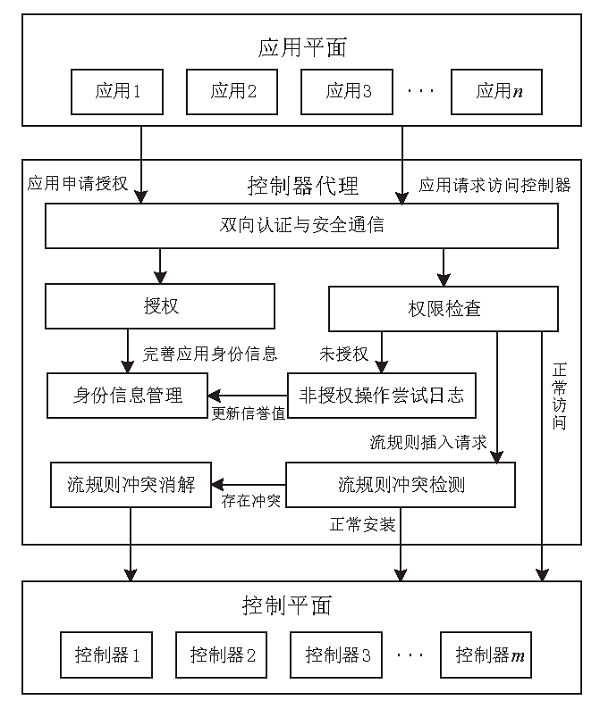
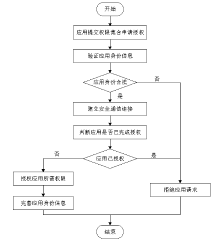
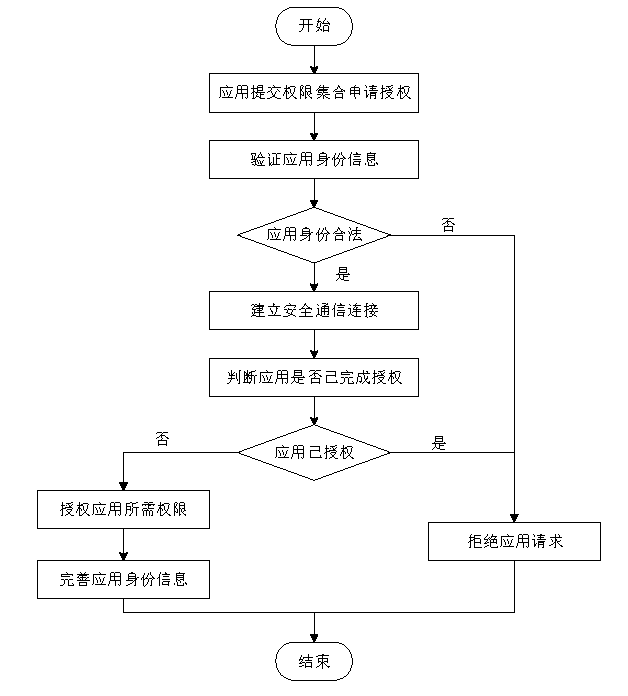
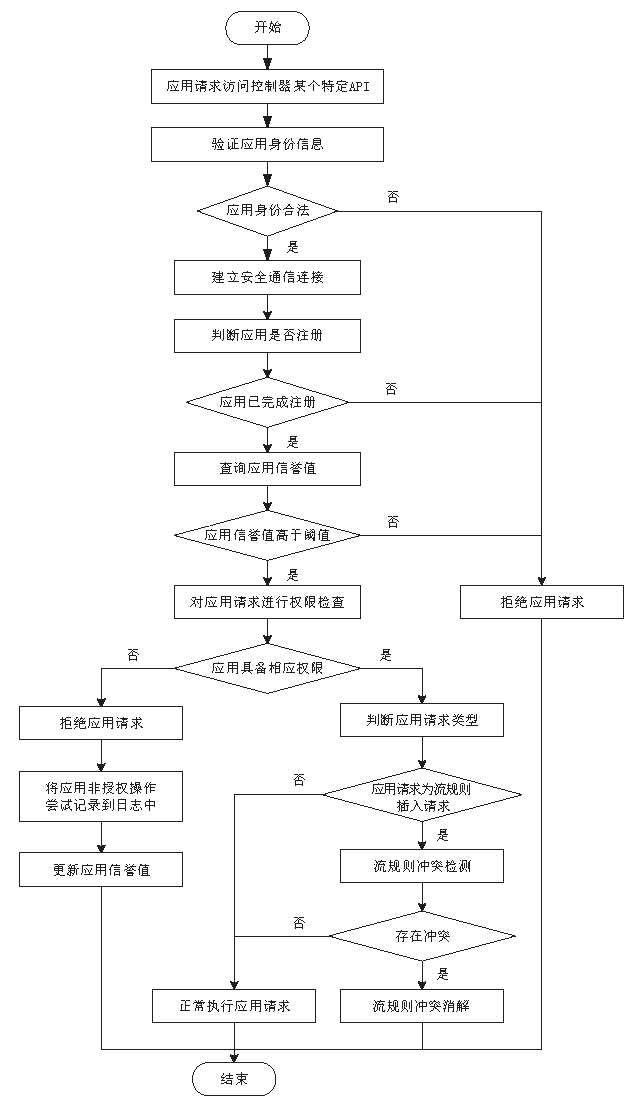
| [1] |
ONF. Software-defined Networking(SDN) Definition[EB/OL]. , 2020-12-20.
|
| [2] |
DABBAGH M, HAMDAOUI B, GUIZANI M, et al. Software-defined Networking Security: Pros and Cons[J]. Communications Magazine IEEE, 2015,53(6):73-79.
doi: 10.1109/MCOM.2015.7120048
URL
|
| [3] |
RAWAT D B, REDDY S R. Software Defined Networking Architecture, Security and Energy Efficiency: A Survey[J]. IEEE Communications Surveys & Tutorials, 2016,19(1):325-346.
|
| [4] |
Project Floodlight. Floodlight Controller[EB/OL]. https://floodlight.atlassian.net/wiki/spaces/floodlightcontroller/overview, 2020-12-20.
|
| [5] |
OpenDaylight. Platform Overview[EB/OL]. , 2020-12-22.
|
| [6] |
ONF. ONOS[EB/OL]. https://onosproject.org/, 2020 -12-22.
|
| [7] |
IETF. Software-defined Networking: A Perspective from within a Service Provider Environment[EB/OL].https://www.rfc-editor.org/info/rfc7149 , 2020 -12-22.
|
| [8] |
KREUTZ D, RAMOS F M V, VERISSIMO P. Towards Secure and Dependable Software-defined Networks[C]// ACM. ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, August 22, 2014, Chicago, IL, USA. New York: ACM, 2014: 55-60.
|
| [9] |
AHMAD I, NAMAL S, YLIANTTILA M, et al. Security in Software Defined Networks: A Survey[J]. IEEE Communications Surveys & Tutorials, 2015,17(4):2317-2346.
|
| [10] |
SHU Zhaogang, WAN Jiafu, LI Di, et al. Security in Software-defined Networking: Threats and Countermeasures[J]. Mobile Networks and Applications, 2016,21(5):764-776.
doi: 10.1007/s11036-016-0676-x
URL
|
| [11] |
SCOTT-HAYWARD S, NATARAJAN S, SEZER S. A Survey of Security in Software Defined Networks[J]. IEEE Communications Surveys & Tutorials, 2016,18(1):623-654.
|
| [12] |
ONF. Principles and Practices for Securing Software-defined Networks[EB/OL]. https://opennetworking.org/wp-content/uploads/2014/10/Principles_and_Practices_for_Securing_Software-Defined_Networks_applied_to_OFv1.3.4_V1.0.pdf, 2020-12-25.
|
| [13] |
SMELIANSKY R L. SDN for Network Security [C]//IEEE. 2014 International Science and Technology Conference (Modern Networking Technologies), October 28-29, 2014, Moscow, Russia. NJ: IEEE, 2014: 1-5.
|
| [14] |
CHAUDHARY R, AUJLA G S, GARG S, et al. SDN-enabled Multi-attribute-based Secure Communication for Smart Grid in IIoT Environment[J]. IEEE Transactions on Industrial Informatics, 2018,14(6):2629-2640.
doi: 10.1109/TII.9424
URL
|
| [15] |
LEE S, YOON C, SHIN S. The Smaller, the Shrewder: A Simple Malicious Application Can Kill an Entire SDN Environment[C]// ACM. 2016 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, March 11, 2016, New Orleans, LA, USA. New York: ACM, 2016: 23-28.
|
| [16] |
LEE C, SHIN S. SHIELD: An Automated Framework for Static Analysis of SDN Applications[C]// ACM. 2016 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, March 11, 2016, New Orleans, LA, USA. New York: ACM, 2016: 29-34.
|
| [17] |
WANG Pengzhan, HUANG Liusheng, XU Hongli, et al. Rule Anomalies Detecting and Resolving for Software Defined Networks[C]// IEEE. GLOBECOM 2015-2015 IEEE Global Communications Conference, December 6-10, 2015, San Diego, CA, USA. NJ: IEEE, 2016: 1-6.
|
| [18] |
PISHARODY S, CHOWDHARY A, HUANG Dijiang. Security Policy Checking in Distributed SDN-based Clouds[C]// IEEE. 2016 IEEE Conference on Communications and Network Security (CNS), October 17-19, 2016, Philadelphia, PA, USA. NJ: IEEE, 2017: 19-27.
|
| [19] |
PISHARODY S, NATARAJAN J, CHOWDHARY A, et al. Brew: A Security Policy Analysis Framework for Distributed SDN-based Cloud Environments[J]. IEEE Transactions on Dependable & Secure Computing, 2017,16(6):1011-1025.
|
| [20] |
WANG Mengmeng, LIU Jianwei, CHEN Jie, et al. PERM-GUARD: Authenticating the Validity of Flow Rules in Software Defined Networking[C]// IEEE. 2015 IEEE 2nd International Conference on Cyber Security and Cloud Computing, November 3-5, 2015, New York, NY, USA. NJ: IEEE, 2015: 127-132.
|
| [21] |
PORRAS P, SHIN S, YEGNESWARAN V, et al. A Security Enforcement Kernel for OpenFlow Networks[EB/OL]. , 2020-12-25.
|
| [22] |
PORRAS P A, CHEUNG S, FONG M W, et al. Securing the Software Defined Network Control Layer[EB/OL]. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.703.7607&rep=rep1&type=pdf, 2020-12-25.
|
 ), JIA Jie1, HUANG Min2
), JIA Jie1, HUANG Min2