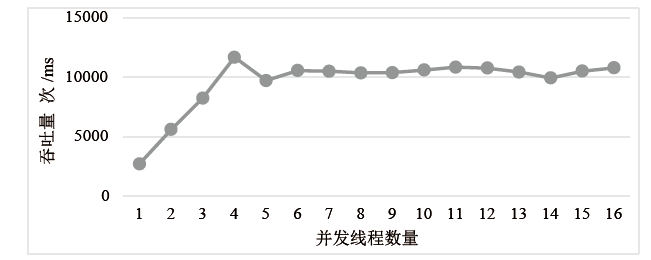
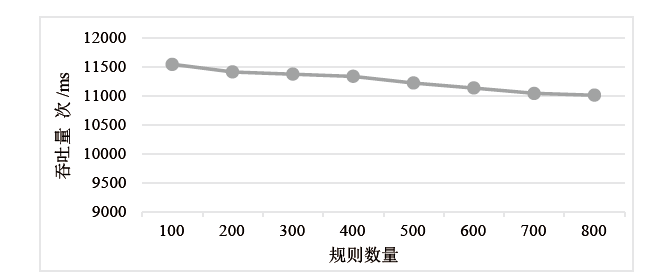
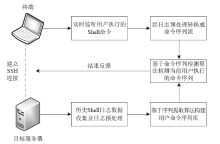
| [1] |
ARDAGNA CA, ASAL R, DAMIANI E, et al. From Security to Assurance in the Cloud: A Survey[J]. ACM Computing Surveys, 2015,48(1):1-50.
|
| [2] |
LI Jiliang, CHOO K K R, ZHANG Weiguo, et al. EPA-CPPA: An Efficient, Provably-secure And Anonymous Conditional Privacy-preserving Authentication Scheme for Vehicular Ad Hoc Networks[J]. Vehicular Communications, 2018,44(13):104-113
|
| [3] |
LI Jinxu. Security Threat Analysis and Countermeasures of Data Center in Universities[J]. Information & Communications, 2018,21(8):147-148.
|
|
李金旭. 高校数据中心安全威胁分析与对策[J]. 信息通信, 2018,21(8):147-148.
|
| [4] |
MCKAY K, BASSHAM L, SÖNMEZTURAN M, et al. Report on Lightweight Cryptography[EB/OL]. https://www.nist.gov/publications/report-lightweight-cryptography, 2020-10-15.
|
| [5] |
ZHANG Shuiping, LI Jizhen, ZHANG Fengqin, et al. Research and Implementation of Data Center Security System Based on Cloud Computing[J]. Computer Engineering and Design, 2011,32(12):3965-3968, 3979.
|
|
张水平, 李纪真, 张凤琴, 等. 基于云计算的数据中心安全体系研究与实现[J]. 计算机工程与设计, 2011,32(12):3965-3968,3979.
|
| [6] |
ZHANG Jianhan, NIE Yuanming. Data Center Security Protection Technical Analysis[J]. Netinfo Security, 2012,12(3):56-60.
|
|
张剑寒, 聂元铭. 数据中心安全防护技术分析[J]. 信息网络安全, 2012,12(3):56-60.
|
| [7] |
LI Chao, TIAN Xinguang, XIAO Xi, et al. Anomaly Detection of User Behavior Based on Shell Commands and Co-occurrence Matrix[J]. The Journal of Computer Research and Development. 2012,49(9):1982-1990.
|
|
李超, 田新广, 肖喜, 等. 基于Shell命令和共生矩阵的用户行为异常检测方法[J]. 计算机研究与发展, 2012,49(9):1982-1990.
|
| [8] |
GUO Weiming. Design and Research of Intrusion Detection System Based on Linux Host[D]. Xiamen: Xiamen University, 2018.
|
|
郭为鸣. 基于Linux主机的入侵检测系统的设计与研究[D]. 厦门:厦门大学, 2018.
|
| [9] |
SHONE N, NGOC T N, PHAI V D, et al. A Deep Learning Approach to Network Intrusion Detection[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018,2(1):41-50.
doi: 10.1109/TETCI.2017.2772792
URL
|
| [10] |
SERPEN G, AGHAEI E. Host-based Misuse Intrusion Detection Using PCA Feature Extraction and KNN Classification Algorithms[J]. Intelligent Data Analysis, 2018,22(5):1101-1114.
doi: 10.3233/IDA-173493
URL
|
| [11] |
ZHANG Jianwu, HUANG Jiasen, ZHOU Di. Intrusion Detection Model Based on Fuzzy Theory and Association Rules[J]. Telecommunications Science, 2019,35(5):59-69.
|
|
章坚武, 黄佳森, 周迪. 基于模糊理论与关联规则的入侵检测模型[J]. 电信科学, 2019,35(5):59-69.
|
| [12] |
ZHU Shaoping, XIAO Yonglian, DANG Yanjun. Intrusion Detection of Network Security Based on MSNN Model[J]. Computing Technology and Automation, 2019,38(4):182-185.
|
|
朱韶平, 肖永良, 党艳军. 基于MSNN模型的网络安全入侵检测[J]. 计算技术与自动化, 2019,38(4):182-185.
|
| [13] |
YANG Kui. A Novel Research on Real-time Intrusion Detection Technology Based on Data Mining[J]. Journal of Physics: Conference Series, 2019,1345(5):16-19.
|
| [14] |
CHELBA C, NOROUZI M, BENGIO S. N-gram Language Modeling Using Recurrent Neural Network Estimation[EB/OL]. https://arxiv.org/abs/1703.10724, 2017-03-09.
|
| [15] |
TIAN Xinguang, GAO Lizhi, ZHANG Eryang. Intrusion Detection Method Based on Machine Learning[J]. Journal on Communications, 2006,26(6):108-114.
|
|
田新广, 高立志, 张尔扬. 新的基于机器学习的入侵检测方法[J]. 通信学报, 2006,26(6):108-114.
|
 )
)