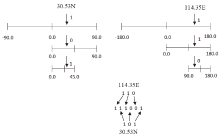
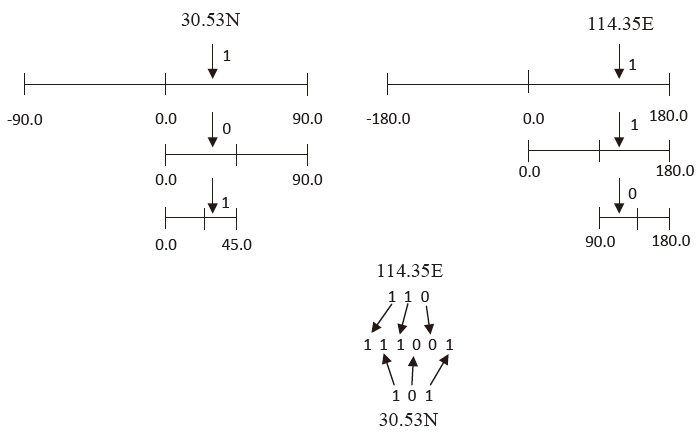
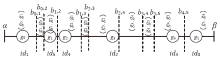
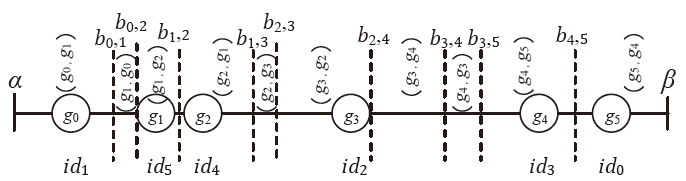
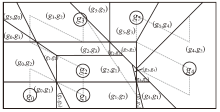
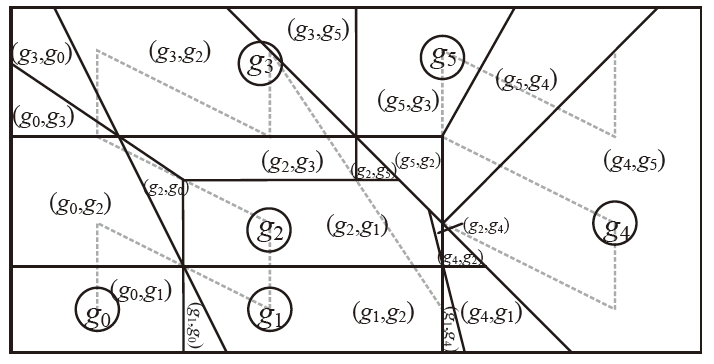
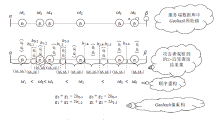
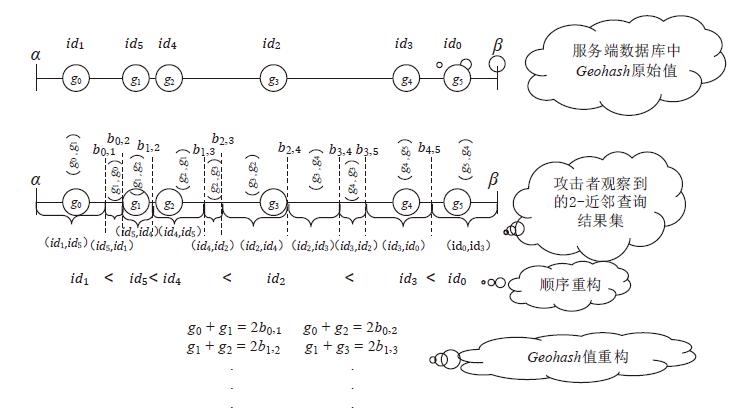
| [1] |
JIN An, CHENG Chengqi, SONG Shuhua, et al. Regional Query of Area Data Based on Geohash[J]. Geography and Geo-information Science, 2013,29(5): 31-35.
|
|
金安, 程承旗, 宋树华, 等. 基于 Geohash 的面数据区域查询[J]. 地理与地理信息科学, 2013,29(5): 31-35.
|
| [2] |
HUANG Keying, LI Guoqing, WANG Jian. Rapid Retrieval Strategy for Massive Remote Sensing Metadata Based on GeoHash Coding[J]. Remote Sensing Letters, 2018,9(11): 1070-1078.
|
| [3] |
ZHOU Chang, LU Huimei, XIANG Yong, et al. GeohashTile: Vector Geographic Data Display Method Based on Geohash[J]. ISPRS International Journal of Geo-Information, 2020,9(7): 418-443.
|
| [4] |
XIANG Longgang, WANG Dehao, GONG Jianya. Organization and Efficient Range Query of Large Trajectory Data Based on Geohash[J]. Geomatics and Information Science of Wuhan University, 2017,42(1): 21-27.
|
|
向隆刚, 王德浩, 龚健雅. 大规模轨迹数据的 Geohash 编码组织及高效范围查询[J]. 武汉大学学报(信息科学版), 2017,42(1): 21-27.
|
| [5] |
HE Shouwu, CHU Longxian, LI Xiaoying. Spatial Query Processing for Location Based Application on Hbase[C]//IEEE. 2nd International Conference on Big Data Analysis (ICBDA), March 10-12, 2017, Bejing, China. New York: IEEE, 2017: 110-114.
|
| [6] |
TAKASU A. An Efficient Distributed Index for Geospatial Databases[C]//Springer. Database and Expert Systems Applications, September 1-4, 2015, Valencia, Spain. Nature Switzerland AG: Springer, 2015: 28-42.
|
| [7] |
BAN Ya, WANG Rui, LIU Hongjing, et al. An Efficient Distributed Index for Geospatial Databases[C]//Atlantis Press. International Conference on Computer Modeling, Simulation and Algorithm (CMSA), April, 22-23, 2018, Beijing,China. Paris: Atlantis Press, 2018: 385-388.
|
| [8] |
WU Ke. Research on GPU-based Spatial Data Index and Query Technology[D]. Xi’an: Xidian University, 2018.
|
|
吴珂. 基于GPU的空间数据索引与查询技术研究[D]. 西安:西安电子科技大学, 2018.
|
| [9] |
BOST R. Forward Secure Searchable Encryption[C]//ACM. Proceedings of the 23th ACM Conference on Computer and Communications Security (ACM CCS), October 24-28, 2016, Vienna Austria. New York: ACM, 2016: 1143-1154.
|
| [10] |
CASH D, JAEGER J, JARECKI S, et al. Dynamic Searchable Encryption in Very-large Databases: Data Structures and Implementation[C]//ISOC. Network & Distributed System Security Symposium (NDSS), February 23-26, 2014, San Diego, CA, USA. Reston VA: ISOC, 2014: 23-26.
|
| [11] |
CURTMOLA R, GARAY J, KAMARA S, et al. Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[J]. Journal of Computer Security, 2011,19(5): 895-934.
|
| [12] |
KELLARIS G, KOLLIOS G, NISSIM K, et al. Generic Attacks on Secure Outsourced Databases[C]//ACM. Proceedings of the 23th ACM Conference on Computer and Communications Security (ACM CCS), October 24-28, 2016, Vienna Austria. New York: ACM, 2016: 1329-1340.
|
| [13] |
LACHARITÉ M S, MINAUD B, PATERSON K G. Improved Reconstruction Attacks on Encrypted Data Using Range Query Leakage[C]//IEEE. 2018 IEEE Symposium on Security and Privacy (SP), May 20-24, 2018, San Francisco, CA, USA. New York: IEEE, 2018: 297-314.
|
| [14] |
KORNAROPOULOS E M, PAPAMANTHOU C, TAMASSIA R. Data Recovery on Encrypted Databases with k-nearest Neighbor Query Leakage[C]//IEEE. 2019 IEEE Symposium on Security and Privacy (SP), May 19-23, 2019, San Francisco, CA, USA. New York: IEEE, 2019: 1033-1050.
|
| [15] |
GRUBBS P, LACHARITÉ M S, MINAUD B, et al. Learning to Reconstruct: Statistical Learning Theory and Encrypted Database Attacks[C]//IEEE. 2019 IEEE Symposium on Security and Privacy (SP), May 19-23, 2019, San Francisco, CA, USA. New York: IEEE, 2019: 1067-1083.
|
 ), LIU Shubo3
), LIU Shubo3