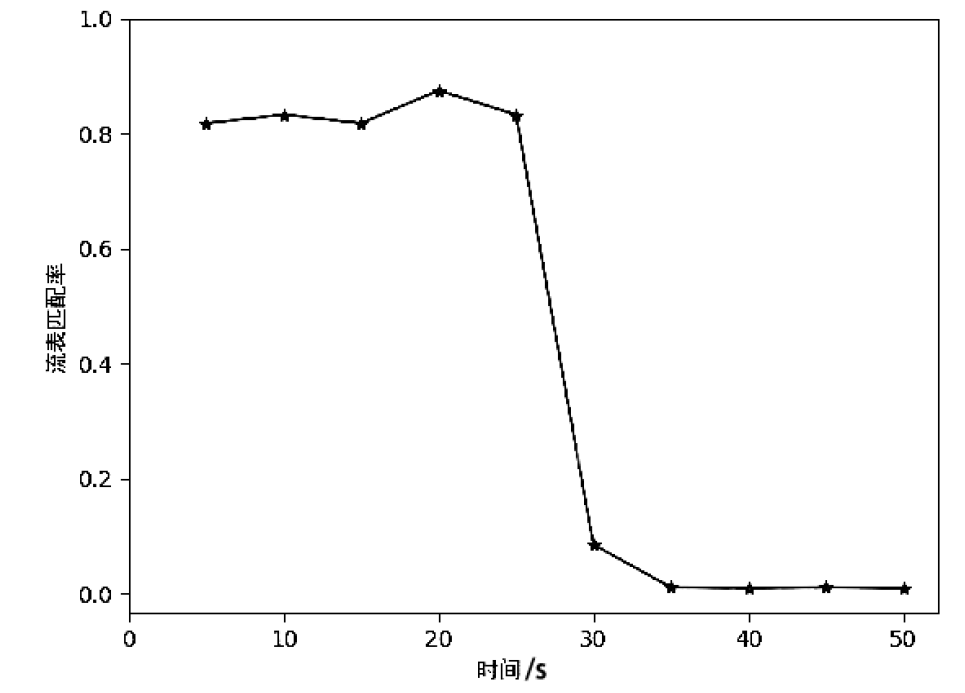
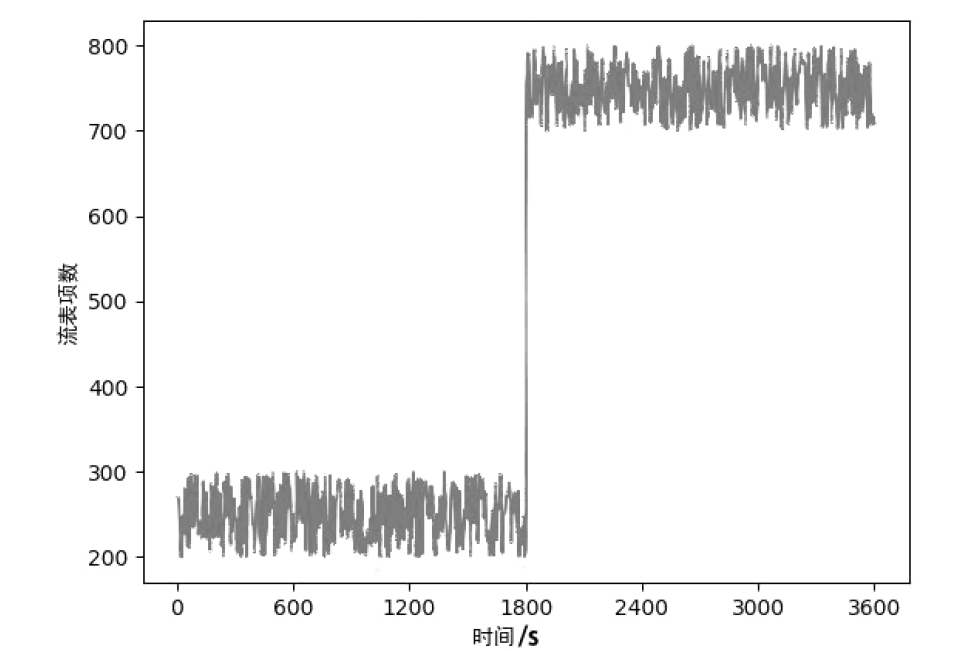
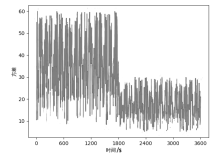
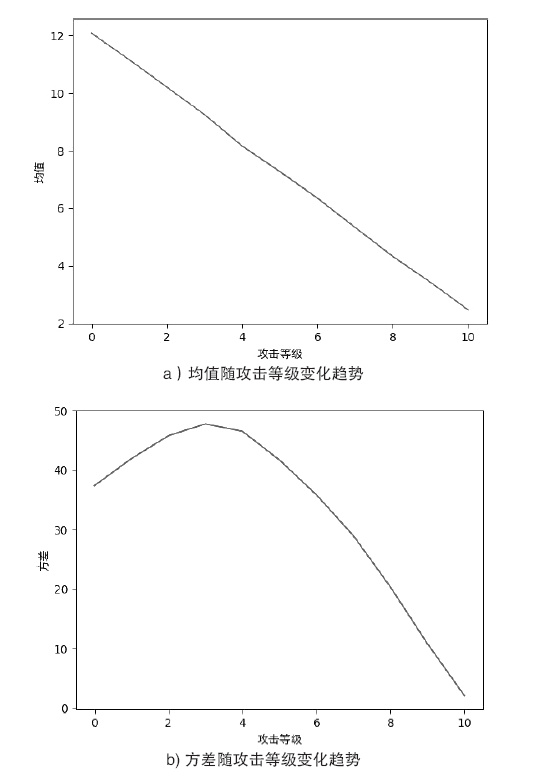
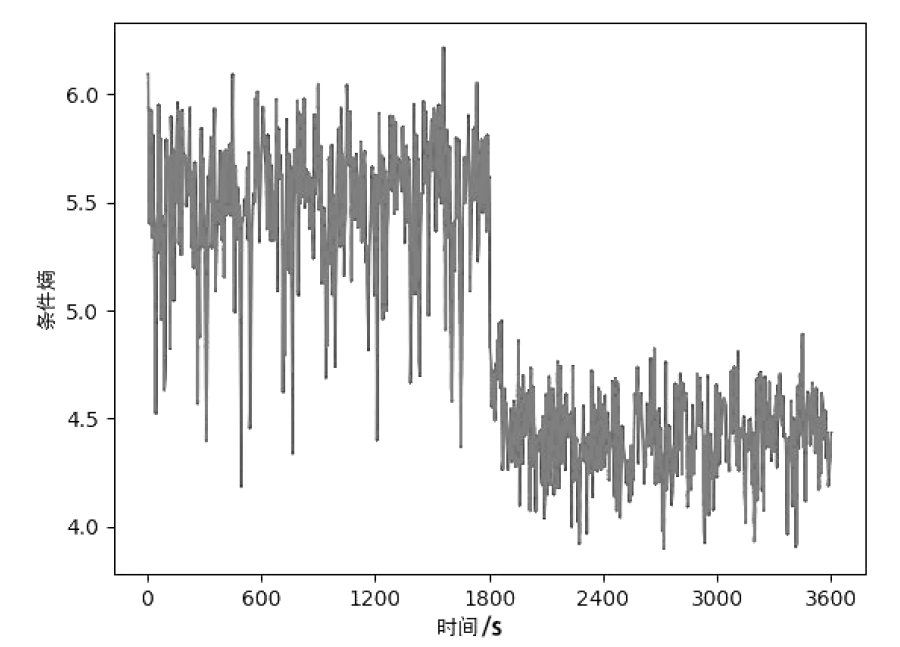
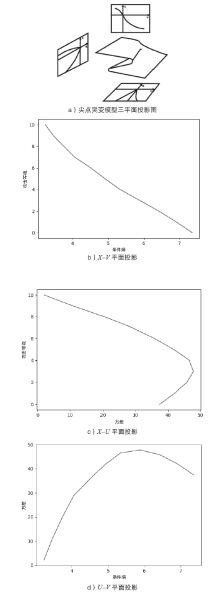
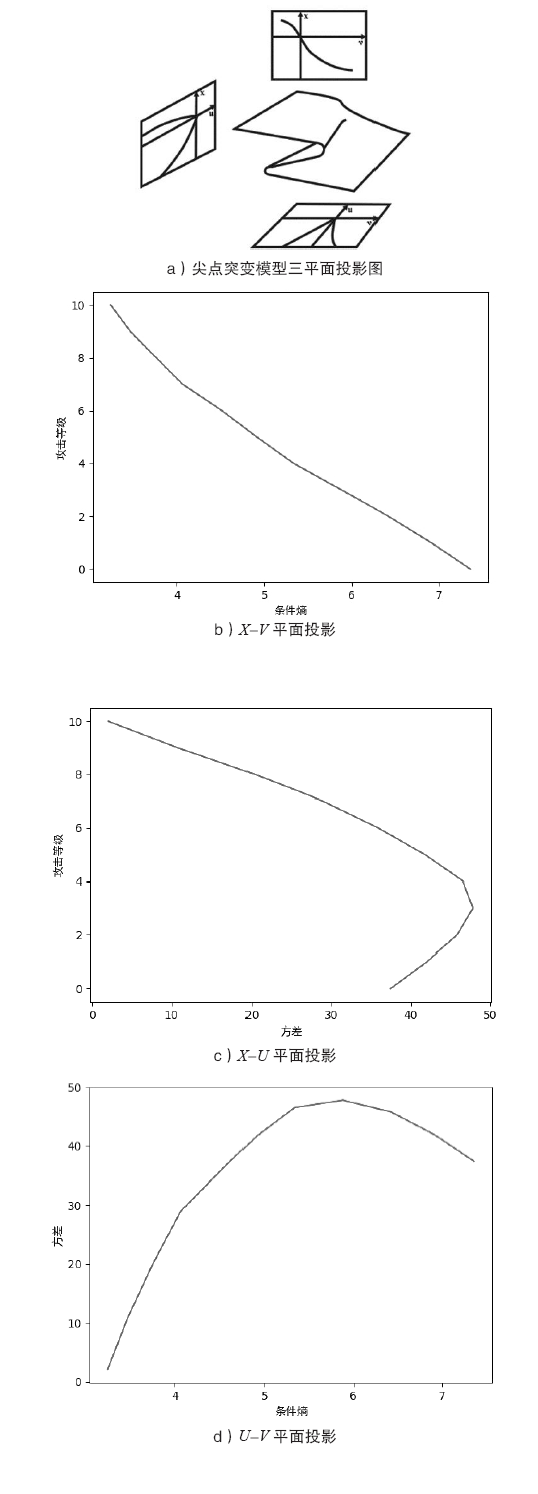
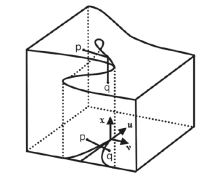
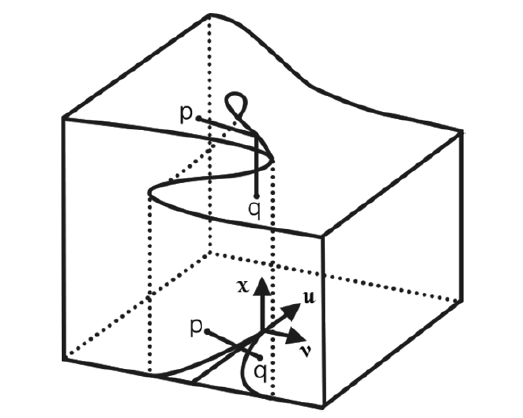
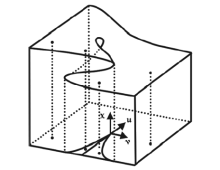
| [1] |
DONG Shi, ABBAS K, JAIN R . A Survey on Distributed Denial of Service(DDoS) Attacks in SDN and Cloud Computing Environments[J]. IEEE Access, 2019(7):80813-80828.
|
| [2] |
CHEN K Y, JUNUTHULA A R, SIDDHRAU I K , et al. SDNShield: Towards More Comprehensive Defense Against DDoS Attacks on SDN Control Plane [C]//IEEE. IEEE Conference on Communications and Network Security, October 17-19, 2016, Philadelphia, PA, USA. New Jersey: IEEE, 2016: 28-36.
|
| [3] |
SAKIR S, SANDRA S H, PUSHPINDER K C , et al. Are We Ready for SDN? Implementation Challenges for Software-Defined Networks[J]. IEEE Communications Magazine, 2013,51(7):36-43.
|
| [4] |
DHARMA N I G, MUTHOHAR M F, PRAYUDA J D A , et al. Time-based DDoS Detection and Mitigation for SDN Controller [C]//IEEE. 17th Asia-Pacific Network Operations and Management Symposium, August 19-21, 2015, Busan, South Korea. New Jersey: IEEE, 2015: 550-553.
|
| [5] |
BENTON K, CAMP L J, SMALL C . Open Flow Vulnerability Assessment [C]//ACM. ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, August 16, 2013, Hong Kong, China. New York: ACM, 2013: 151-152.
|
| [6] |
WANG Haopei, XU Lei, GU Guofei . FloodGuard: A DoS Attack Prevention Extension in Software-defined Networks [C]//IEEE/IFIP. 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, June 22-25, 2015, Rio de Janeiro, Brazil. New Jersey: IEEE, 2015: 239-250.
|
| [7] |
GIOTIS K, ARGYROPOULOS C, ANDROULIDAKIS G , et al. Combining OpenFlow and sFlow for an Effective and Scalable Anomaly Detection and Mitigation Mechanism on SDN Environments[J]. Computer Networks, 2014(62):122-136.
|
| [8] |
ZHENG Shiji . Research on SDN-based IoT Security Architecture Model [C]//IEEE. IEEE 8th Joint International Information Technology and Artificial Intelligence Conference, May 24-26, 2019, Chongqing, China. New Jersey: IEEE, 2019: 575-579.
|
| [9] |
BRAGA R, MOTA E, PASSITO A . Lightweight DDoS Flooding Attack Detection Using NOX/OpenFlow [C]//IEEE. The 35th Annual IEEE Conference on Local Computer Networks, October 10-14, 2010, Denver, CO, USA. New Jersey: IEEE, 2010: 408-415.
|
| [10] |
JIANG Wenti, GU Yu, REN Danni , et al. DDoS Attacks and Flash Crowds Detection Based on Flow Characteristics in SDN[J]. Journal of Chongqing University of Posts and Telecommunications(Natural Science Edition), 2019,31(3):420-426.
|
|
姜文醍, 谷宇, 任丹妮 , 等. SDN中基于流特征的DDoS攻击与闪拥事件检测[J]. 重庆邮电大学学报(自然科学版), 2019,31(3):420-426.
|
| [11] |
LI Chuanhuang, WU Yan, YUAN Xiaoyong , et al. Detection and Defense of DDoS Attack-based on Deep Learning in OpenFlow-based SDN[EB/OL]. http://smartsearch.nstl.gov.cn/paper_detail.html?id=f9f7fd77d39aaea3e4dcb5c026a490c6, 2019-9-11.
|
| [12] |
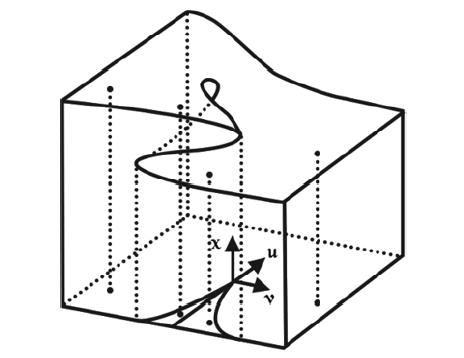
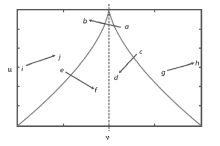
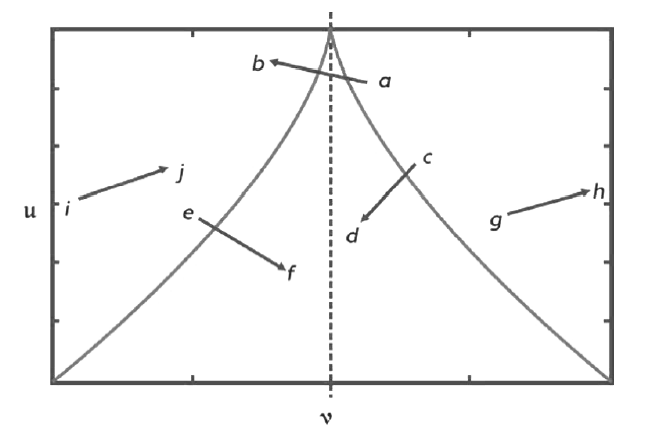
AERTS D, CZACHOR M, GABORA M , et al. Quantum Morphogenesis: A Variation on Thom’s Catastrophe Theory[EB/OL]. https://arxiv.org/pdf/quant-ph/0211105v2.pdf, 2019-9-12
|
| [13] |
GUO Yi, MIAO FU, ZHANG Liancheng , et al. CATH: An Effective Method for Detecting Denial-of-Service Attacks in Software Defined Networks[J]. Science China Information Sciences, 2019,62(3):75-89.
|
| [14] |
QI Liuling . Research of DDoS Attack Detection Method Based on Entropy and Neural Networks in SDN[D]. Baoding: Hebei University, 2018.
|
|
齐鎏岭 . SDN中基于熵和神经网络的DDoS攻击检测方法研究[D]. 保定:河北大学, 2018.
|
| [15] |
HU Wusheng . IP Network Anomalous Behavior Detection and Mechanism Based on Catastrophe Theory[D]. Chengdu: University of Electronic Science and Technology of China, 2010.
|
|
胡武生 . 基于突变理论的IP网络异常行为检测和控制机制[D]. 成都:电子科技大学, 2010.
|
| [16] |
IMAN S, ARASH H L, SAQIB H , et al. Developing Realistic Distributed Denial of Service(DDoS) Attack Dataset and Taxonomy [C]//IEEE. IEEE 53rd International Carnahan Conference on Security Technology, October 1-3, 2019, Chennai, India. New Jersey: IEEE, 2019: 1-8.
|
 ), WANG Yujie1,2, HAN Lei3
), WANG Yujie1,2, HAN Lei3