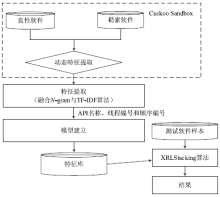
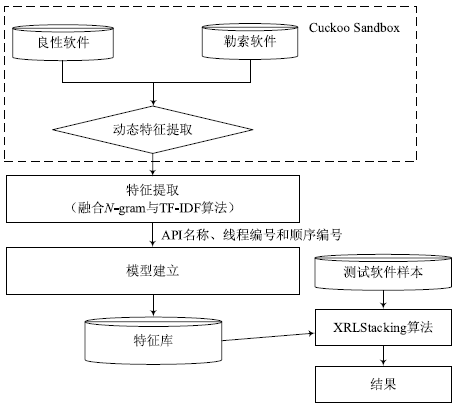
| [1] |
FreeBuf. Blackmail: Backup Files Can Prevent Blackmail Software? It’s not Simple![EB/OL]. , 2019-5-11.
|
|
FreeBuf.黑客勒索:备份文件就能防勒索软件?没那么简单[EB/OL]. , 2019-5-11.
|
| [2] |
LIN Jianbao, CUI Xiang, ZHANG Fangjiao.Blackmail Attacks are Becoming More and More Intense, and Security Awareness Needs to be Strengthened[J]. China Information Security, 2016(8): 79-83.
|
|
林建宝,崔翔,张方娇.勒索攻击愈演愈烈,安全意识亟待加强[J]. 中国信息安全, 2016(8):79-83.
|
| [3] |
WANG Zihan.Research on the Tracing and Tracing Technology of Extortion Software[D]. Beijing: Beijing University of Posts and Telecommunication, 2019.
|
|
王梓晗. 勒索软件追踪溯源技术研究[D].北京:北京邮电大学,2019.
|
| [4] |
Tencent Yujian Threat Intelligence Center. Special Report on Blackmail Virus in the First Half of 2019[EB/OL]. , 2019-5-11.
|
|
腾讯御见威胁情报中心. 2019上半年勒索病毒专题报告[EB/OL]. , 2019-5-11.
|
| [5] |
ANDRONIO N, ZANERO S, MAGGI F.HelDroid: Dissecting and Detecting Mobile Ransomware[C]//Springer. International Symposium on Recent Advances in Intrusion Detection, November 2-4, 2015, Kyoto, Japan. Heidelberg: Springer, 2015: 382-404.
|
| [6] |
SGANDURRA D, MUÑOZ-GONZÁLEZ L, MOHSEN R, et al. Lupu: Automated Dynamic Analysis of Ransomware: Benefits, Limitations and Use for Detection[EB/OL]. , 2019-5-12.
|
| [7] |
CHANDRASEKAR R, MANOHARAN R. Malware Detection Using Windows API Sequence and Machine Learning[EB/OL]. , 2019-5-18.
|
| [8] |
HAN Lansheng, GAO Kunlun, ZHAO Baohua, et al.Behavior Detection of Malware Based on Combination of API Function and Its Parameters[J]. Application Research of Computers, 2013, 30(11): 3407-3410, 3425.
|
|
韩兰胜,高昆仑,赵保华,等.基于API函数及其参数相结合的恶意软件行为检测[J]. 计算机应用研究,2013,30(11):3407-3410,3425.
|
| [9] |
ALAZAB M, LAYTON R, VENKATARAMAN S, et al. Malware Detection Based on Structural and Behavioural Features of API Calls[EB/OL]. , 2019-5-24.
|
| [10] |
KHARRAZ A, ROBERTSON W, BALZAROTTI D, et al. Cutting the Gordian Knot: A Look under the Hood of Ransomware Attacks[EB/OL]. , 2019-5-12.
|
| [11] |
CHEN Qian, ROBERT A. Bridges: Automated Behavioral Analysis of Malware: A Case Study of WannaCry Ransomware[EB/OL]. , 2019-5-13.
|
| [12] |
HAMPTON N, BAIG Z A, ZEADALLY S. Ransomware Behavioural Analysis on Windows Platforms[EB/OL]. , 2019-5-13.
|
| [13] |
GONG Qi, CAO Jinxuan, LU Tianliang, et al.Research on Detecting Ransomware Based on Characteristic Frequencies[J]. Application Research of Computers, 2018, 35(8): 2435-2438.
|
|
龚琪,曹金璇,芦天亮,等.基于特征频繁度的勒索软件检测方法研究[J]. 计算机应用研究,2018,35(8):2435-2438.
|
| [14] |
LI Meng, JIA Xiaoqi, WANG Rui, et al.A Feature Selection and Modelling Method for Malicious Code[J]. Computer Applications and Software, 2015, 32(8): 266-271.
|
|
李盟,贾晓启,王蕊,等.一种恶意代码特征选取和建模方法[J]. 计算机应用与软件,2015,32(8):266-271.
|
| [15] |
TIAN Dandan.Large Scale Web Page Classification Algorithm Based on Spectral Hashing[J]. Software Engineering and Applications, 2016, 5(1): 65-74.
|
|
田郸郸. 基于谱哈希的大规模网页分类算法[J]. 软件工程与应用,2016,5(1):65-74.
|
| [16] |
XU Bing, LIU Xiaojie, LI Shuai.Detection Method of Encrypted Extortion Software Based on File Characteristics[J]. Data Communications, 2019(2): 5-8, 34.
|
|
徐兵,刘晓洁,李帅.基于文件特征的加密型勒索软件检测方法[J]. 数据通信, 2019(2):5-8,34.
|
| [17] |
RIECK K, HOLZ T, WILLEMS C, et al.Learning and Classification of Malware Behavior[C]//Springer. 5th Conference on Detection of Intrusions and Malware and Vulnerability Assessment, July 10-11, Paris, France. Heidelberg: Springer, 2008: 108-125.
|
| [18] |
CHEN Tianqi, GUESTRIN C.XGBoost: A Scalable Tree Boosting System[C]//ACM. 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 13-17, 2016, San Francisco, CA, USA. New York: ACM, 2016: 785-794.
|
| [19] |
FRIEDMAN N, GEIGER D, GOLDSZMID M.Bayesian Network Classifier[J]. Machine Learning, 1997, 29(1): 131-163.
|
| [20] |
SHEEN S, YADAV A. Ransomware Detection by Mining API Call Usage[EB/OL]. , 2019-5-18.
|
| [21] |
CHAWLA N V, BOWYER K W, HALL L O, et al. Smote: Synthetic Minority Over-sampling Technique[EB/OL]. , 2019-5-19.
|
| [22] |
XIANG Zihao, QIU Weidong.Detection Method of Ransomware Based on Machine Learning[J]. Information Technology, 2018(5): 79-82, 89.
|
|
项子豪,邱卫东.基于机器学习的勒索软件检测方法[J]. 信息技术, 2018(5):79-82,89.
|
 ), GU Zhaojun1, ZHOU Jingxian1
), GU Zhaojun1, ZHOU Jingxian1