Netinfo Security ›› 2019, Vol. 19 ›› Issue (8): 51-60.doi: 10.3969/j.issn.1671-1122.2019.08.008
Previous Articles Next Articles
Research on Access Control for Privacy Protection of Mobile Terminals
A-yong YE( ), Junlin JIN, Lingyu MENG, Ziwen ZHAO
), Junlin JIN, Lingyu MENG, Ziwen ZHAO
- College of Mathematics and Informatics, Fujian Normal University, Fuzhou Fujian 350007, China
-
Received:2019-04-10Online:2019-08-10Published:2020-05-11
CLC Number:
Cite this article
A-yong YE, Junlin JIN, Lingyu MENG, Ziwen ZHAO. Research on Access Control for Privacy Protection of Mobile Terminals[J]. Netinfo Security, 2019, 19(8): 51-60.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.08.008
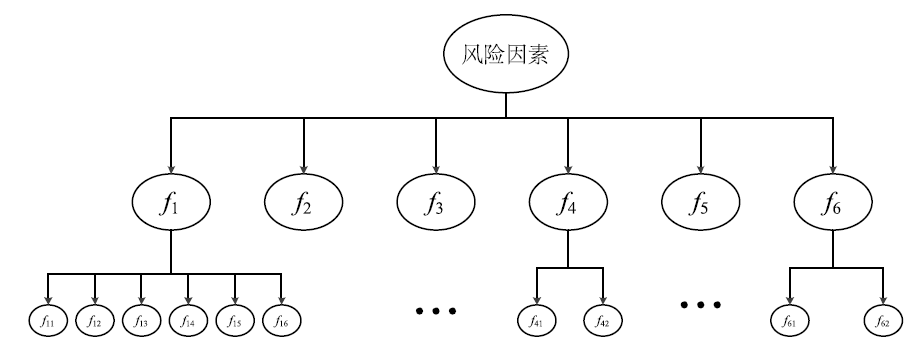
| f1 | f2 | f3 | f4 | f5 | f6 | |
|---|---|---|---|---|---|---|
| f1 | (1,1,1) | (1,1.31,2) | (1,0.667,0.5) | (1,1.817,2.5) | (0.667,0.55,0.5) | (1,1.778,3) |
| f2 | (0.5,0.763,1.5) | (1,1,1) | (0.667,0.55,0.5) | (1,1.5,2) | (0.5,0.464,0.4) | (0.5,1.44,2.5) |
| f3 | (1,1.5,2) | (1,1.817,2.5) | (1,1,1) | (1.5,2.32,3) | (0.5,0.763,1.5) | (1.5,2.289,3) |
| f4 | (0.667,0.55,0.5) | (1,0.667,0.5) | (0.5,0.464,0.4) | (1,1,1) | (0.4,0.354,0.26) | (1,1,2) |
| f5 | (1,1.817,2.5) | (1.5,2.154,3) | (0.5,1.31,2) | (2,2.657,3.5) | (1,1,1) | (2,2.657,3.5) |
| f6 | (0.5,0.562,0.5) | (0.67,0.69,0.67) | (0.4,0.437,0.4) | (0.5,1,2) | (0.4,0.333,0.26) | (1,1,1) |
| [1] | FELT A P, CHIN E, HANNA S, et al.Android Permissions Demystified[C]//ACM. ACM Conference on Computer & Communications Security, October 17-21, 2011, Chicago, USA. New York: ACM, 2011: 627-638. |
| [2] | ENCK W, ONGTANG M, MCDANIEL P.On Lightweight Mobile Phone Application Certification[C]//ACM. The 16th ACM Conference on Computer and Communications Security, November 9-13, 2009, Chicago, Illinois, USA. New York: ACM, 2009: 235. |
| [3] | CHUN B G.TaintDroid: An Information-Flow Tracking System for Realtime Privacy Monitoring on Smartphones.[J]. Acm Transactions on Computer Systems, 2014, 32(2): 1-29. |
| [4] | YOUNGROK C, WOOGUIL P, HUANG C H.Protecting Contacts against Privacy Leaks in Smartphones[J]. Plos One, 2018, 13(7): e0191502. |
| [5] | BHATT A J, GUPTA C, MITTAL S. iABC-AL: Active Learning-based Privacy Leaks Threat Detection for iOS Applications[EB/OL]. , 2018-5-23. |
| [6] | LI Tao, ZHANG Chi.Research on Network Security Risk Model Based on the Information Security Level Protection Standards[J]. Netinfo Security, 2016, 16(9): 177-183. |
| 李涛,张驰.基于信息安全等保标准的网络安全风险模型研究[J].信息网络安全,2016,16(9):177-183. | |
| [7] | Jason Program Office.Horizontal Integration: Broader Access Models for Realizing Information Dominance[R]. Mclean Virginia: The Mitrf Corporation, JSR-04-132, 2004. |
| [8] | SHAIKH R A, ADI K, LOGRIPPO L.Dynamic Risk-based Decision Methods for Access Control Systems[J]. Computers & Security, 2012, 31(4): 447-464. |
| [9] | TAN Zhiyong LIU Duo, SI Tiange, et al. A Multilevel Security Model with Credibility Characteristics[J]. Acta Electronica Sinica, 2008, 36(8): 1637-1641. |
| 谭智勇,刘铎,司天歌,等. 一种具有可信度特征的多级安全模型[J]. 电子学报,2008,36(8):1637-1641. | |
| [10] | CHENG P C, ROHATGIP P, KESER C, et al.Fuzzy Multi-level Security: An Experiment on Quantified Risk-adaptive Access Control[C]//IEEE. IEEE Symposium on Security and Privacy, May 20-23, 2007, Berkeley, CA, USA. NJ: IEEE, 2007: 222-230. |
| [11] | NI Qun, BERTINO E, LOBO J.Risk-based Access Control Systems Built on Fuzzy Inferences[C]//ACM. The 5th ACM Symposium on Information, Computer and Communications Security, April 13-16, 2010, Beijing, China. New York: ACM, 2010: 250-260. |
| [12] | DIMMOCK N, BELOKOSZTOLSZKI A, EYERS D, et al.Using Trust and Risk in Role-based Access Control Policies[C]//ACM. The Ninth ACM Symposium on Access Control Models and Technologies, June 2-4, 2004, Yorktown Heights, New York, USA. New York: ACM, 2004: 156-162. |
| [13] | CHEN Liang, CRAMPTON J.Risk-aware Role-based Access Control[C]//Springer. The 7th International Conference on Security and Trust Management, June 27-28, 2011, Copenhagen, Denmark. Heidelberg: Springer-Verlag, 2011: 140-156. |
| [14] | LI Ruixuan, HU Jinwei, TANG Zhuo, et al.R2BAC: A Risk-based Multi-domain Secure Interoperation Model[J]. Journal on Communications, 2008, 29(10): 58-69. |
| 李瑞轩,胡劲纬,唐卓,等. R2BAC:基于风险的多自治域安全互操作模型[J]. 通信学报,2008,29(10):58-69. | |
| [15] | BIJON K Z, KRISHNAN R, SANDHU R.A Framework for Risk-aware Role-based Access Control[C]//IEEE. 2013 IEEE Conference on Communications and Network Security, October 14-16, 2013, National Harbor, MD, USA. NJ: IEEE, 2013: 1-18. |
| [16] | WU Shasha, XIONG Jinbo, YE Guohua, et al.Research on Location Privacy Protection Based on Dummy Locations in Mobile Internet Environment[J]. Netinfo Security, 2016, 16(10): 54-59. |
| 吴莎莎,熊金波,叶帼华,姚志强.移动互联网环境下基于假位置的位置隐私保护研究[J].信息网络安全,2016,16(10):54-59. | |
| [17] | BRITTON D W, BROWN I A. A Security Risk Measurement for the Radac Model[EB/OL]. , 2019-3-15. |
| [18] | ZHOU Lintao, LI Hongxing, SUN Kaibiao.Teaching Performance Evaluation by Means of a Hierarchical Multifactorial Evaluation Model Based on Type-2 Fuzzy Sets[J]. Applied Intelligence, 2016, 46(1): 1-11. |
| [19] | SAATY T L.How to Make a Decision: The Analytic Hierarchy Process[J]. European Journal of Operational Research, 1994, 24(6): 19-43. |
| [20] | WEN Weiping, GUO Ronghua, MENG Zheng, et al.Research and Implementation on Information Security Risk Assessment Key Technology[J]. Netinfo Security, 2015, 15(2): 7-14. |
| 文伟平,郭荣华,孟正,柏皛.信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015,15(2):7-14. |
| [1] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [2] | Weimin LANG, Han ZHANG, Yifeng ZHAO, Jinfang YAO. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [3] | DUAN Qiongqiong, XIANG Dinghua, SHI Hongzhou. Design on the Blockchain-based Authentication for Smart Objects [J]. 信息网络安全, 2018, 18(9): 95-101. |
| [4] | ZHAO Na, LONG Hui, SU Jinshu. A Scheme for Anonymous Authentication and Privacy Protection in the Internet of Things Environment [J]. 信息网络安全, 2018, 18(11): 1-7. |
| [5] | CHEN Fulong, ZHANG Ziyang, WANG Taochun, XIE Dong. A Kind of Secure Identity Authentication Method Based on Contact Signals for Internet of Things [J]. 信息网络安全, 2018, 18(11): 40-48. |
| [6] | CHEN Yanan, MEI Qian, XIONG Hu, XU Weixiang. Certificateless Parallel Key-insulated Signature for Industrial Internet of Things [J]. 信息网络安全, 2018, 18(10): 1-9. |
| [7] | FAN Hong, SHAO Hua, LI Haitao. Implementation and Application of Internet of Things Security Technology [J]. 信息网络安全, 2017, 17(9): 38-41. |
| [8] | ZHAO Kuo, XING Yongheng. Security Survey of Internet of Things Driven by Block Chain Technology [J]. 信息网络安全, 2017, 17(5): 1-6. |
| [9] | PENG Kunlun, PENG Wei, WANG Dongxia, XING Qianqian. Research Survey on Security Issues in Cyber-Physical Systems [J]. 信息网络安全, 2016, 16(7): 20-28. |
| [10] | ZHANG Yuting, YAN Chenghua. Research on RFID Authentication Technology Based on Two-way Authentication Protocol [J]. 信息网络安全, 2016, 16(1): 64-69. |
| [11] | CHEN Zi-hong. Research on Security Model in Internet of Things for Tobacco Companies [J]. 信息网络安全, 2015, 15(9): 217-220. |
| [12] | CHEN Chen, WANG Yi-Jun, HU Guang-jun, GUO Yan-hui. Research for APT Attack Technology [J]. 信息网络安全, 2015, 15(3): 33-37. |
| [13] | ZHU Peng-fei, YU Hua-zhang, LU Zhou, ZHANG Yi-fei. A Smart Inspection Recording Scheme based on OTP Token [J]. 信息网络安全, 2014, 14(9): 165-166. |
| [14] | . Survey of Location-Data Security Strategy [J]. , 2014, 14(6): 6-. |
| [15] | . Identity-based Encryption Authenticated Key Agreement Protocol [J]. , 2014, 14(3): 1-. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||