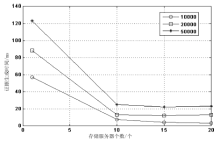
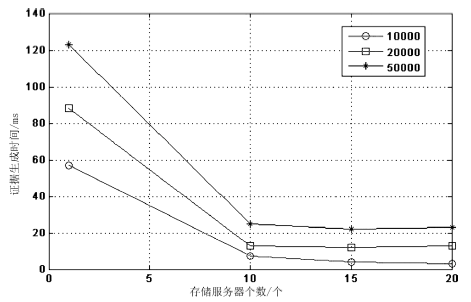
| [1] |
TAN Shuang, JIA Yan, HAN Weihong.Research and Development of Provable Data Integrity in Cloud Storage[J]. Chinese Journal of Computers, 2015, 38(1): 164-177.
|
|
谭霜,贾焰,韩伟红.云存储中的数据完整性证明研究及进展[J].计算机学报,2015,38(1):164-177.
|
| [2] |
LI Bo, HUANG Yanyu, LIU Zheli, et al.HybridORAM: Practical Oblivious Cloud Storage with Constant Bandwidth[J].Information Sciences, 2019, 479: 651-663.
|
| [3] |
LV Congdong, HAN Zhen, MA Wei.Design and Implementation of Data Storage Encryption Mechanism in Cloud Storage[J]. Netinfo Security, 2014, 14(6): 1-5.
|
|
吕从东,韩臻,马威.云存储服务端数据存储加密机制的设计和实现[J].信息网络安全,2014,14(6):1-5.
|
| [4] |
STANEK J, KENCL L.Enhanced Secure Thresholded Data Deduplication Scheme for Cloud Storage[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(4): 694-707.
|
| [5] |
LEI Lei,CAI Quanwei, JING Jiwu,et al. Enforcing Access Controls on Encrypted Cloud Storage with Policy Hiding[J]. Journal of Software, 2016, 27(6): 1432-1450.
|
|
雷蕾,蔡权伟,荆继武,等.支持策略隐藏的加密云存储访问控制机制[J].软件学报,2016,27(6):1432-1450.
|
| [6] |
PENG Su, ZHOU Fucai, XU Jian, et al.Comments on Identity-Based Distributed Provable Data Possession in Multicloud Storage[J]. IEEE Transactions on Services Computing, 2016, 9(6): 996-998.
|
| [7] |
ZHAO Yang, CHEN Yang, XIONG Hu, et al.A Revocable Authorization Provable Data Possession Scheme in Clouds[J]. Netinfo Security, 2015, 15(8): 1-7.
|
|
赵洋,陈阳,熊虎,等.云环境下一种可撤销授权的数据拥有性证明方案[J].信息网络安全,2015,15(8):1-7.
|
| [8] |
JUELS A, KALISKI Jr B S. PORs: Proofs of Retrievability for Large Files[C]//ACM. The 14th ACM Conference on Computer and Communications Security, October 29-November 2, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 584-597.
|
| [9] |
ATENIESE G, BURNS R, CURTMOLA R, et al.Provable Data Possession at Untrusted Stores[C]// ACM. The 14th ACM Conference on Computer and Communications Security, October 29-November 2, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 598-609.
|
| [10] |
SHACHAM H, WATERS B.Compact Proofs of Retrievability[J]. Journal of Cryptology, 2012, 26(3): 442-483.
|
| [11] |
ATENIESE G, PIETRO R D, MANCINI L V, et al.Scalable and Efficient Provable Data Possession[C]//ACM. The 4th International Conference on Security and Privacy in Communication Netowrks, September 22-25, 2008, Istanbul, Turkey. New York: ACM, 2008.
|
| [12] |
ERWAY C,>KÜP04Ü A,PAPAMANTHOU C, et al. Dynamic Provable Data Possession[C]//ACM. The 16th ACM Conference on Computer and Communications Security, November 9-13, 2009, Illinois, USA. New York: ACM, 2009: 213-222.
|
| [13] |
ESINER E, KACHKEEV A, BRAUNFELD S, et al.FlexDPDP: FlexList-based Optimized Dynamic Provable Data Possession[J]. ACM Transactions on Storage, 2016, 12(4): 1-44.
|
| [14] |
CURTMOLA R, KHAN O, BURNS R, et al.MR-PDP: Multiple-replica Provable Data Possession[C]//IEEE. The 28th International Conference on Distributed Computing Systems, July 17-20, 2008, Beijing, China. NJ: IEEE, 2008: 411-420.
|
| [15] |
BARSOUM A F, HASAN M A. On Verifying Dynamic Multiple Data Copies over Cloud Servers[EB/OL]. , 2011-8-15.
|
| [16] |
ZHU Yan, HU Hongxin, AHN G J, et al.Cooperative Provable Data Possession for Integrity Verification in Multicloud Storage[J]. IEEE Transactions on Parallel & Distributed Systems, 2012, 23(12): 2231-2244.
|
| [17] |
XU Jian, LI Mingjie, LI Fuxiang, et al.Optimized Algorithms for Flexible Length-Based Authenticated Skip List[J]. China Communications, 2016, 13(1): 124-138.
|
 ), Mingjie LI, Jian XU, Fucai ZHOU
), Mingjie LI, Jian XU, Fucai ZHOU