| [1] |
CAI Fangbo, HE Jingsha, ZHANG Yuqiang, et al.Research on Real-time Synchronization Security Scheme for Wireless Sensor Nodes[J]. Netinfo Security, 2016, 16(8): 12-17.
|
|
蔡方博,何泾沙,张玉强,等.无线传感器节点实时同步安全方法研究[J].信息网络安全,2016,16(8):12-17.
|
| [2] |
LI Jianhui, LIU Chang, WANG Caishen, et al.Research and Design of Multi-parameter Health Monitoring System Based on WBAN[J]. Modern Electronics Technique, 2017, 40(22): 149-151.
|
|
李建辉,刘畅,王彩申,等.基于WBAN的多参数健康监护系统研究与设计[J].现代电子技术,2017,40(22):149-151.
|
| [3] |
KARLOF C, SASTRY N, WAGNER D.TinySec: A Link Layer Security Architecture for Wireless Sensor Networks[C]//ACM. International Conference on Embedded Networked Sensor Systems, November 3-5, 2004, Baltimore, MD, USA. New York: ACM, 2004 : 162-175.
|
| [4] |
LUK M, MEZZOUR G, PERRIG A, et al.MiniSec: A Secure Sensor Network Communication Architecture[C]//IEEE. International Conference on Information Processing in Sensor Networks, April 25-27, 2007, Cambridge, MA, USA. New York: IEEE, 2007: 479-488.
|
| [5] |
WU Chuankun, ZHANG Lei, LI Jiangli.Design of Trust Architecture and Lightweight Authentication Scheme for IoT Devices[J]. Netinfo Security, 2017, 17(9): 16-20.
|
|
武传坤,张磊,李江力.物联网设备信任体系架构与轻量级身份认证方案设计[J].信息网络安全,2017,17(9):16-20.
|
| [6] |
ZHAO Na, LONG Hui, SU Jinshu.A Scheme for Anonymous Authentication and Privacy Protection in the Internet of Things Environment[J]. Netinfo Security, 2018, 18(11): 1-7.
|
|
赵娜,龙慧,苏金树.一种适用于物联网环境的匿名认证与隐私保护方案[J].信息网络安全,2018,18(11):1-7.
|
| [7] |
ULUTAS M, ULUTAS G, NABIYEV V V.Medical Image Security and EPR Hiding Using Shamir’s Secret Sharing Scheme[J]. Journal of Systems and Software, 2011, 84(3): 341-353.
|
| [8] |
MEMON N A, GILANI S A M. Watermarking of Chest CT Scan Medical Images for Content Authentication[J]. International Journal of Computer Mathematics, 2011, 88(2): 265-280.
|
| [9] |
LI M, YU S, GUTTMAN J D, et al.Secure Ad Hoc Trust Initialization and Key Management in Wireless Body Area Networks[J]. ACM Transactions on Sensor Networks, 2013, 9(2): 1-35.
|
| [10] |
FIAT A, SHAMIR A.How To Prove Yourself: Practical Solutions to Identification and Signature Problems[J]. Advances in Cryptology-Eurocrypt '86, 1986, 263(25): 186-194.
|
| [11] |
SINGH T R, SINGH K M, ROY S.Video Watermarking Scheme Based on Visual Cryptographyand Scene Change Detection[J]. AEU-International Journal of Electronics and Communications, 2013, 67(8): 645-651.
|
| [12] |
NAOR M, SHAMIR A.Visual Cryptography[J]. Lecture Notes in Computer Science, 1994, 950(9): 1-12.
|
| [13] |
SUREKH B, SWAMY G N, REDDY K R L. A Novel Copyright Protection Scheme Based on Visual Secret Sharing[C]//IEEE. Third International Conference on Computing, Communication and Networking Technologies, July 26-28, 2012, Coimbatore, India. New York: IEEE, 2012: 1-5.
|
| [14] |
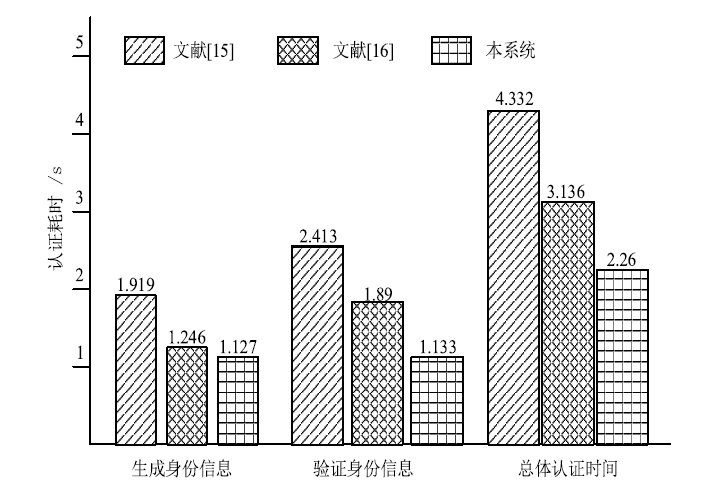
QIAN Suo.Introduction on Intelligent Transportation System Based on WSN[J]. Electronic Measurement Technology, 2018, 41(5): 102-105.
|
| [15] |
WANG Weihong, CUI Yiling, CHEN Tieming.Design and Implementation of an ECDSA-based Identity Authentication Protocol on WSN[C]//IEEE. IEEE International Symposium on Microwave, Antenna, Propagation and EMC Technologies for Wireless Communications, October 27-29, 2009, Beijing, China. New York: IEEE, 2009: 1202-1205.
|
| [16] |
WANG Haodong, SHENG Bo, TAN Chiu C, et al.Public-key Based Access Control in Sensornet[J]. Wireless Networks, 2011, 17(5): 1217-1234.
|
 )
)