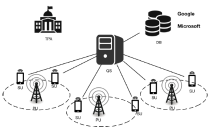
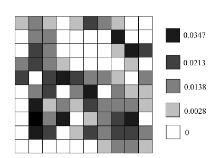
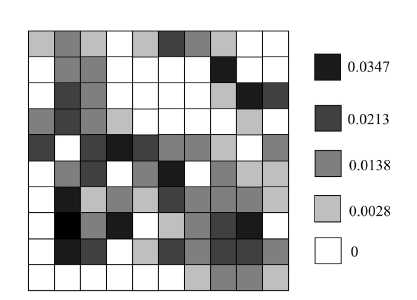
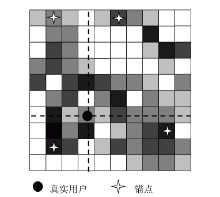
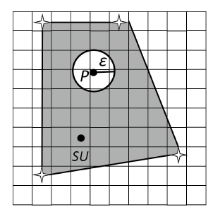
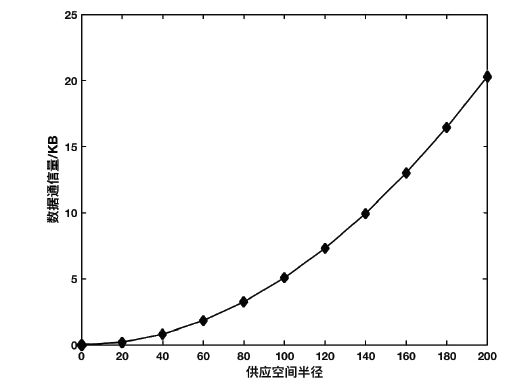
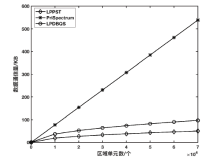
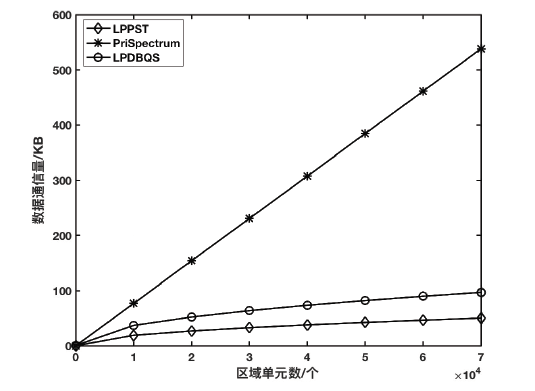
| [1] |
MITOLA J, MAGUIRE G Q.Cognitive Radio: Making Software Radios More Personal[J]. IEEE Personal Communiactions, 1999,6(4):13-18.
|
| [2] |
AKYILDIZ I F, LO B F, BALAKRISHNAN R.Cooperative Spectrum Sensing in Cognitive Radio Networks: A Survey[J]. Physical Communication,2011, 4(1): 40-62.
|
| [3] |
RAO Xuli, LIN Hui, TIAN Youliang, et al.Research on a Trusted Collaborative Second Users Selection Strategy in Distributed Cognitive Radio Networks[J].Netinfo Security, 2018,18(10):37-44.
|
|
饶绪黎,林晖,田有亮,等.分布式认知无线电网络中的一种可信协作次用户选取策略研究[J].信息网络安全,2018,18(10):37-44.
|
| [4] |
Federal Communications Commission.Third Memorandum Opinion and Order[R].Washington: Federal Communications Commission, FCC-12-36,2012.
|
| [5] |
CHEN V, DAS S, ZHU Lei, et al.Protocol to Access White-space (PAWS) Databases[R].USA: Internet Engineering Task Force, Fremont, RFC 7545, 2015.
|
| [6] |
MURTY R, CHANDRA R.Senseless: A Database-driven White Spacesnetwork[J]. IEEE Transactions on Mobile Computing, 2011, 11(2):189-203.
|
| [7] |
GRISSA M, YAVUZ A A, HAMDAOUI B.Cuckoo Filter-based Location-privacy Preservation in Database-driven Cognitive Radio Networks[C]//IEEE. 2015 World Symposium on Computer Networks and Information Security (WSCNIS), September 19-21, 2015, Hammamet, Tunisia. NJ: IEEE, 2015,1-7.
|
| [8] |
WU Shasha, XIONG Jinbo, YE Guohua,et al.Research on Location Privacy Protection Based on Dummy Locations in Mobile Internet Environment[J].Netinfo Security, 2016,16(10):54-59.
|
|
吴莎莎,熊金波,叶帼华,等.移动互联网环境下基于假位置的位置隐私保护研究[J].信息网络安全,2016,16(10):54-59.
|
| [9] |
AGUILARMELCHOR C, BARRIER J, FOUSSE L, et al.Xpir: Private Information Retrieval for Everyone[J]. Proceedings on Privacy Enhancing Technologies,2016(2):155-174.
|
| [10] |
ZANG Hui, BOLOT J.Anonymization of Location Data Does Not Work: a Large-scale Measurement Study[C]//ACM. The 17th Annual International Conference on Mobile Computing and Networking, September 19-23, 2011, Las Vegas, Nevada, USA. New York: ACM, 2011:145-156.
|
| [11] |
PONTARELLI S, REVIRIEGO P, JUANANTONIO M.Parallel d-Pipeline: a Cuckoo Hashing Implementation for Increased Throughput[J]. IEEE Transactions on Computers, 2016, 65(1):326-331.
|
| [12] |
GAO Zhaoyu, ZHU Haojin, LIU Yao, et al.Location Privacy in Database-driven Cognitive Radio Networks: Attacks and Countermeasures[C]// IEEE. 2013 Proceedings IEEE INFOCOM, April 14-19, 2013, Turin, Italy. NJ:IEEE, 2013:2751-2759.
|
| [13] |
TROJA E, SPIRIDON B.Leveraging P2P Interactions for Efficient Location Privacy in Database-driven Dynamic Spectrum Access[J]. International Journal of Network Security, 2014, 17(5):569-579.
|
| [14] |
GRISSA M, YAVUZ A A, HAMDAOUI B.Location Privacy Preservation in Database-driven Wireless Cognitive Networks through Encrypted Probabilistic Data Structures[J]. IEEE Transactions on Cognitive Communications & Networking, 2017, 3(2): 255-266
|
| [15] |
PETROV D, ZNATI T.Location Privacy Preserving Protocols in Database-enabled Cognitive Radio Networks[C]//IEEE. The 13th International Wireless Communications and Mobile Computing Conference, June 26-30, 2017, Valencia, Spain.NJ:IEEE,2017:147-152.
|
| [16] |
YIU M L, JENSEN C S, HUANG Xuegang, et al.Spacetwist: Managing the Trade-offs among Location Privacy, Query Performance, and Query Accuracy in Mobile Services[C]// IEEE. 2008 IEEE 24th International Conference on Data Engineering, April 7-12,2008, Cancun, Mexico. NJ:IEEE, 2008:366-375.
|
| [17] |
EMMA F. Route Choice Analysis: Data, Models,Algorithmsand Applications[EB/OL].,2018-9-20.
|
| [18] |
NIU Ben, LI Qinghua, ZHU Xiaoyan, et al.Achieving k-anonymity in Privacy-aware Location-based Services[C]//IEEE. IEEE INFOCOM 2014-IEEE Conference on Computer Communications, April 27-May 2, 2014, Toronto, ON, Canada.NJ:IEEE,2014: 754-762.
|
| [19] |
BAHRAK B, BHATTARAI S, ULLAH A.Protecting the Primary Users’ Operational Privacy in Spectrum Sharing[C]//IEEE. 2014 IEEE International Symposium on Dynamic Spectrum Access Networks (DYSPAN), April 1-4, 2014 , McLean, VA, USA.NJ:IEEE,2014:236-247.
|
| [20] |
Federal Communications Commission.Enabling Innovative Small Cell Use in 3.5 GHZ Band NPRM & Order[R]. Washington: Federal Communications Commission, FCC 12-148,2012.
|
| [21] |
Electronic Code of Federal Regulations. Subchapter A: Part 15-Television Band Devices[R].Washington: Federal Communications Commission, FCC 752-871,2015.
|
| [22] |
ZHOU Changli, MA Chunguang, YANG Songtao.Research on LBS Location Privacy Protection Method Based on Sensitive Location Diversity[J]. Journal on Communications, 2015, 36(4):125-136.
|
|
周长利,马春光,杨松涛.基于敏感位置多样性的LBS位置隐私保护方法研究[J].通信学报, 2015, 36(4):125-136.
|
 ), Rui ZHU1,2, Yali ZENG1,2
), Rui ZHU1,2, Yali ZENG1,2