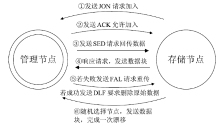
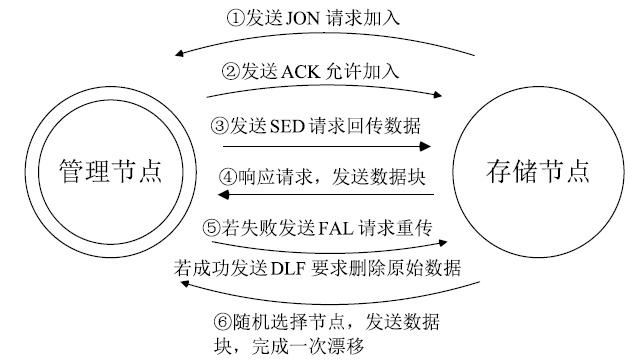
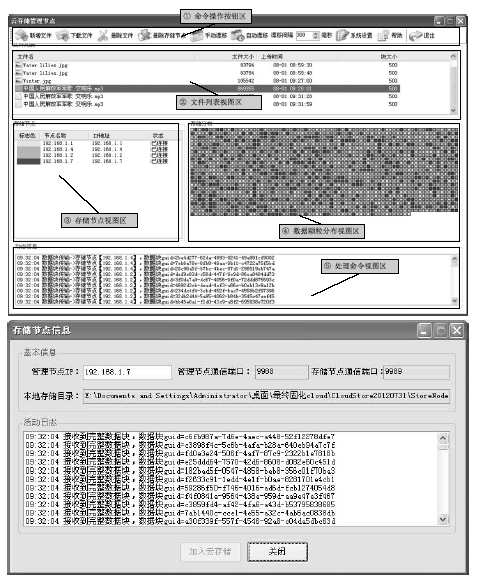
Netinfo Security ›› 2019, Vol. 19 ›› Issue (10): 65-73.doi: 10.3969/j.issn.1671-1122.2019.10.009
Previous Articles Next Articles
A Dynamic Cloud Security Storage System Based on Data Drifting
Xing ZHAO1, Xiaodong WANG2, Chuanrong ZHANG3
- 1. Xidian University, Xi’an Shannxi 710000, China;
2.Tan Kah Kee College, Xiamen University, Zhangzhou Fujian 363105, China
3. Air Force Engineering University, Xi’an Shannxi 710000, China;
-
Received:2019-03-15Online:2019-10-10Published:2020-05-11
CLC Number:
Cite this article
Xing ZHAO, Xiaodong WANG, Chuanrong ZHANG. A Dynamic Cloud Security Storage System Based on Data Drifting[J]. Netinfo Security, 2019, 19(10): 65-73.
share this article
| [1] | WIKIPEDIA. Cloud Storage[EB/OL]. , 2018-5-15. |
| [2] | FU Yingxun, LUO Shengmei, SHU Jiwu, et al.Survey of Secure Cloud Storage System and Key Technologies[J]. Journal of Computer Research and Development, 2013, 50(1): 136-145. |
| 傅颖勋,罗圣美,舒继武.安全云存储系统与关键技术综述[J].计算机研究与发展,2013,50(1):136-145. | |
| [3] | Executive Office Of President, National Science and Technology Council. Turstworthy Cyberspace: Strategic Plan for the Federal Cyber Security Research and Development Program[EB/OL].https://www.nitrd.gov/pubs/Fed_Cybersecurity_RD_Strategic_Plan_2011.pdf, 2011-12-10. |
| [4] | LIU Jie, ZENG Haoyang, TIAN Yongchun, et al.Technologies and Development Trend of Dynamic Resiliency for Security Defense[]]. Communication Technology, 2015, 48(2): 117-124. |
| 刘杰,曾浩洋,田永春,等.动态弹性安全防御技术及发展趋势[J].通信技术,2015,48(2):117-124. | |
| [5] | RAGHU Y.Building the Infrastructure for Cloud Security: A Solutions View[M]. 1st ed.NY: Apress, Berkeley, 2014. |
| [6] | ZHAO Luyi.A Detailed Implementation of Fully Homomorphic Encryption Using Ideal Lattice[C]//IEEE. Proceedings of the 2014 International Conference on Electrical, Control and Automation, February 22-25, 2014. Shanghai, China. New York: IEEE, 2014: 132-139. |
| [7] | JAKE Loftus, ALEXANDER May, et al.On CCA-Secure Somewhat Homomorphic Encryption[C]//IEEE. SAC 2011, March 21-25, 2011, TaiChung, Taiwan China. New York: IEEE, 2013: 55-72. |
| [8] | LI shuanbao, FU Jianming, ZHANG Huanguo, et al. Scheme on User Identity Attribute Preserving Based on Ring Signcryption for Cloud Computing[J]. Journal on Communication, 2014, 35(9): 99-111. |
| 李栓宝,傅建明,张焕国,等.云环境下的基于环签密的用户身份属性保护方案[J].通信学报,2014,35(9):99-111. | |
| [9] | LEE N Y, CHANG Y K.Hybrid Provable Data Possession at Untrusted Stores in Cloud Computing[C]// IEEE. 2011 IEEE 17th International Conference on Parallel and Distributed Systems, December 7-9, 2011, Washington, DC, USA. New York: IEEE, 2011: 638-645. |
| [10] | BOWERS D, JUELS A,OPREA A, et al.Proofs of Retrievability: Theory and Implementation[C]// ACM. Proc of the 2009 ACM Workshop on Cloud Computing Security, November 9-13, 2009, Chicago, IL, USA. New York: ACM, 2009: 43-54. |
| [11] | GE Yao, YONG Li, LINAN Lei, et al.An Efficient Dynamic Provable Data Possession Scheme in Cloud Storage[C]// Springer. 11th International Conference on Green, Pervasive and Cloud Computing(GPC 2016), May 5-8, 2016, Xi’an, China. New York: Springer-Verlag, 2016: 63-81. |
| [12] | NGUYEN T, CUTWAY A, SHI W S.Differentiated Replication Strategy in Data Centers[C]// Springer. Proceedings of the 7th IFIP International Conference on Network and Parallel Computing(NPC 2010), September 13-15, 2010, Zhenzhou, China. New York: Springer-Verlag, 2010: 277-288. |
| [13] | BESSANI A, CORREIA M, QUARESMA B, et al.DepSky: Dependable and Secure Storage in A Cloud-of-clouds[J]. ACM Trans on Storage, 2011, 9( 4): 31-46. |
| [14] | XIANG Fei, LIU Chuanyi, FANG Binxing, et al.Novel“Rich Cloud”Based Data Disaster Recovery Strategy[J]. Journal on Communications, 2013, 34(6): 92-100. |
| 项菲,刘川意,方滨兴,等.新的基于云计算环境的数据容灾策略[J].通信学报,2013,34(6):92-100. | |
| [15] | BIAN Genqing, GAO Song, SHAO Bilin, et al.Security Structure of Cloud Storage Based on Dispersal[J]. Journal of Xi’an Jiaotong University, 2010, 10(9): 41-45. |
| 边根庆,高松,邵必林.面向分散式存储的云存储安全架构[J].西安交通大学学报,2010,10(9):41-45. | |
| [16] | WANG jing, HUANG Chuanhe, WANG Jinhai, et al. An Access Control Mechanism with Dynamic Privilege for Cloud Storage[J]. Journal of Computer Research and Development, 2016, 53(4): 904-920. |
| 王晶,黄传河,王金海.一种面向云存储的动态授权访问控制机制[J].计算机研究与发展,2016,53(4): 904-920. | |
| [17] | WU xiuguo. Research on Minimum Cost Data Replica Distribution Based on Dynamic Planning in Cloud Storage System[J]. Computer Engineering, 2017, 43(7): 29-37. |
| 吴修国. 云存储系统中基于动态规划的最小开销数据副本布局研究[J].计算机工程,2017,43(7):29-37. | |
| [18] | MA weijun, RUAN Kun, FENG Jing, et al. Optimizing Algorithm for I/O Performance of Cloud Storage System Based on Dynamic Hybrid Range Mechanism[J]. Journal of Beijing University of Technology, 2013,39(5): 707-712. |
| 马玮骏,阮鲲,冯径,等.基于动态混合分片机制的云存储系统I/O性能优化算法[J].北京工业大学学报,2013,39(5): 707-712. | |
| [19] | XPENXPEN. Mersenne Twister[EB/OL]. , 2019-1-15. |
| [20] | NAN Chunli, ZHANG Shengrui, NING Hang, et al.Random Number And its Performance Evaluation in Urban Traffic Simulation[J]. Computer engineering, 2009, 35(10): 259-261. |
| 南春丽,张生瑞,宁航,等.城市交通仿真中的随机数及其性能评价[J].计算机工程,2009,35(10):259-261. |
| [1] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [2] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [3] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [4] | Ning LI, Bochao LI. Token-based UTM Architecture for Mobile Internet [J]. Netinfo Security, 2020, 20(3): 18-28. |
| [5] | Xinglong ZHANG, Yuting LI, Qingfeng CHENG, Lulu GUO. A Browser Security Model for Preventing TLS Protocol Downgrade Attacks [J]. Netinfo Security, 2020, 20(3): 65-74. |
| [6] | Shuilin LI, Guobang ZHU, Chunling FAN, Guangyong CHEN. Research on a New Scoring Algorithm of Testing and Evaluation for Classified Cybersecurity Protection [J]. Netinfo Security, 2020, 20(2): 1-6. |
| [7] | Xiao WANG, Jun ZHAO, Jianbiao ZHANG. Research on Dynamic Monitoring Mechanism for Virtual Machine Based on Trusted Software Base [J]. Netinfo Security, 2020, 20(2): 7-13. |
| [8] | Weimin LANG, Han ZHANG, Yifeng ZHAO, Jinfang YAO. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [9] | Mengmeng YAO, Li TANG, Yongxing LING, Weidong XIAO. Formal Analysis of Security Protocol Based on Strand Space [J]. Netinfo Security, 2020, 20(2): 30-36. |
| [10] | Zongping LÜ, Chundi ZHAO, Zhaojun GU, Jingxian ZHOU. Dynamic Detection of Ransomware Based on Stacking Model Fusion [J]. Netinfo Security, 2020, 20(2): 57-57. |
| [11] | Lu YU, Senlin LUO. A Method of Internal Intrusion Detection of Database in RBAC Mode [J]. Netinfo Security, 2020, 20(2): 83-90. |
| [12] | Tao JING, Wei WAN. Research on a P2P Network Communication Behavior Analytical Method for Status Migration Attribute-oriented [J]. Netinfo Security, 2020, 20(1): 16-25. |
| [13] | Die HU, Dongtang MA, Ming GONG, Zhao MA. A Physical Layer Security Authentication Method Based on PUF [J]. Netinfo Security, 2020, 20(1): 61-66. |
| [14] | Xiaoran LI, Rong HAO, Jia YU. Certificateless Provable Data Possession with Data Uploading Control [J]. Netinfo Security, 2020, 20(1): 83-88. |
| [15] | WANG Chonghua, LI Jun, CHEN Xuehong. Research on Industrial Internet Platform Security Protection [J]. Netinfo Security, 2019, 19(9): 6-10. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||