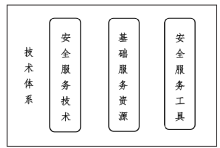
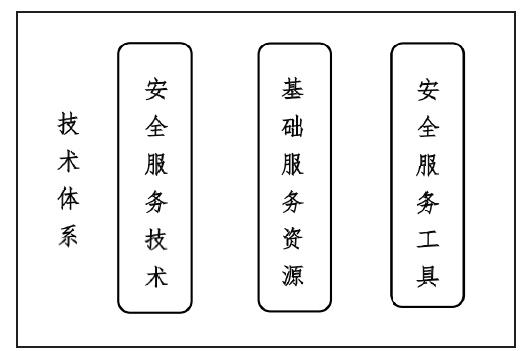
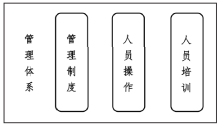
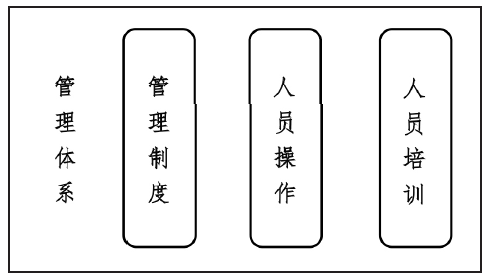
| [1] |
Network Security Law of the People’s Republic of China [EB/OL]. , 2016-11-7.
|
|
中华人民共和国网络安全法[EB/OL]., 2016-11-7.
|
| [2] |
GA/T 1390A/T 1390.2-2017.Information Security Technology—Baseline for Classified Protection of Cybersecurity —Part 2: Specialsecurity Requirements for Cloud Computing[S].Beijing: Standards Press of China,2017.
|
|
GA/T 1390A/T 1390.2-2017.信息安全技术网络安全等级保护基本要求第二部分:云计算扩展要求[S].北京:中国标准出版社,2017.
|
| [3] |
CHEN Yuehua, YANG Dongsheng, MU Biao.The Thoughts of Information Security Service Outsourcing Management[J].Netinfo Security,2012,12(12):86-87.
|
|
陈跃华,杨东升,穆彪. 信息安全服务外包管理思考[J].信息网络安全,2012,12(12):86-87.
|
| [4] |
SUN Mingliang, WEI Hua, WANG Yan. Escort Network Power Strategy to Promote the Development of Network Security Service Industry[EB/OL]. , 2018-4-19.
|
|
孙明亮,位华,王琰. 护航网络强国战略促进网络安全服务业发展[EB/OL]., 2018-4-19.
|
| [5] |
ISO/IEC 27002-2013.Information technology-Security techniques -Code of practice for information security controls [EB/OL].,2018-10-30.
|
| [6] |
GB/T 30271-2013B/T 30271-2013.Information Security Technology—Assessment Criteria for Information Security Service Capability[S].Beijing: Standards Press of China,2013.
|
|
GB/T 30271-2013B/T 30271-2013 .信息安全技术信息安全服务能力评估准则[S].北京:中国标准出版社,2013.
|
| [7] |
JI Hui.Controlling Information System Risk by Information Security Service[J]. Netinfo Security,2010,10(5):17-18.
|
|
季辉. 通过信息安全服务实现信息系统风险可控[J].信息网络安全,2010,10(5):17-18.
|
 ), Chunling FAN2, Guangyong CHEN1, Jintao ZHAO1
), Chunling FAN2, Guangyong CHEN1, Jintao ZHAO1