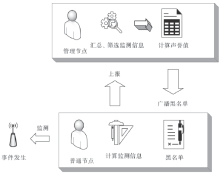
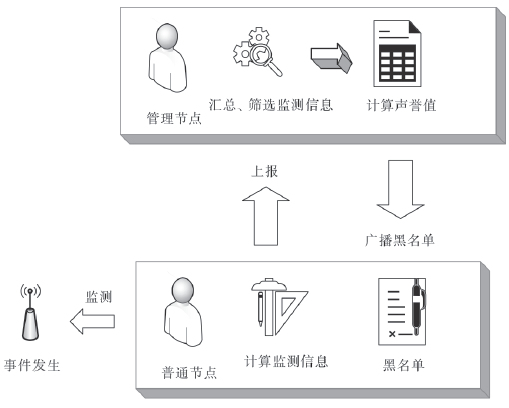
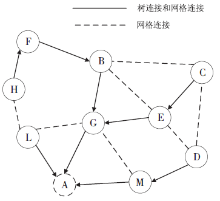
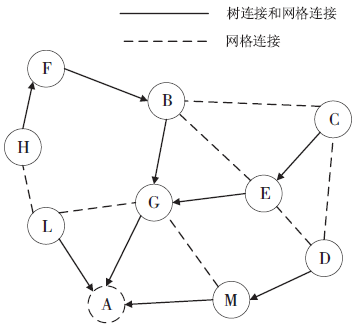
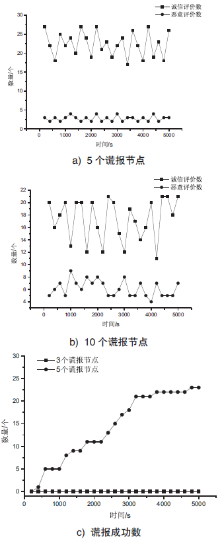
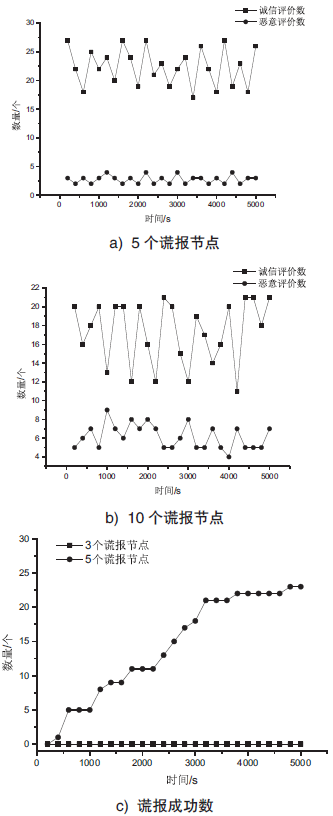
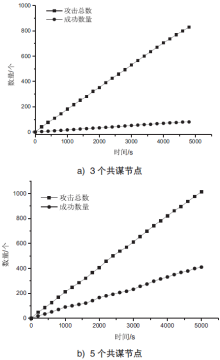
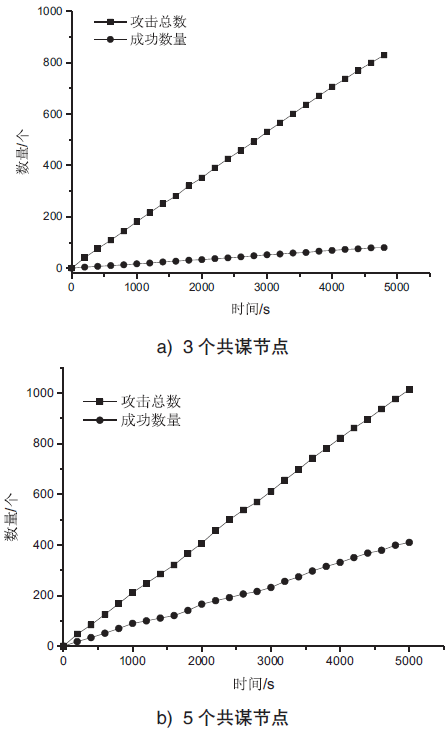
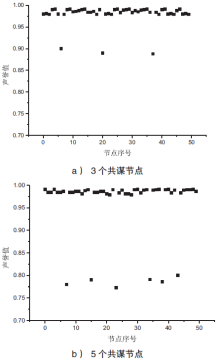
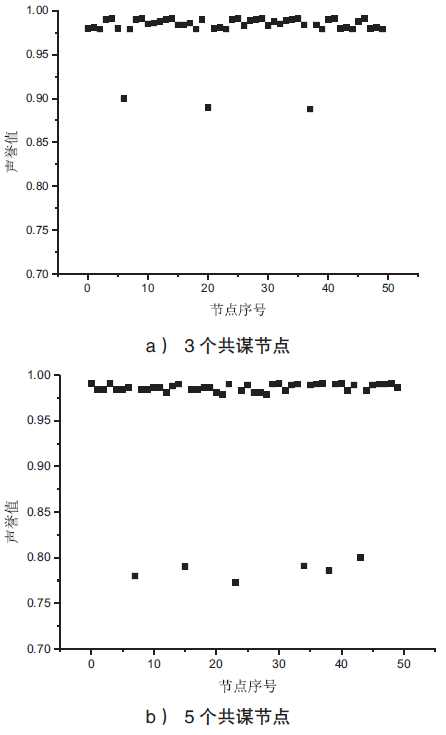
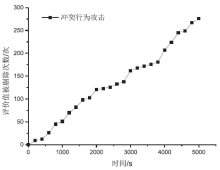
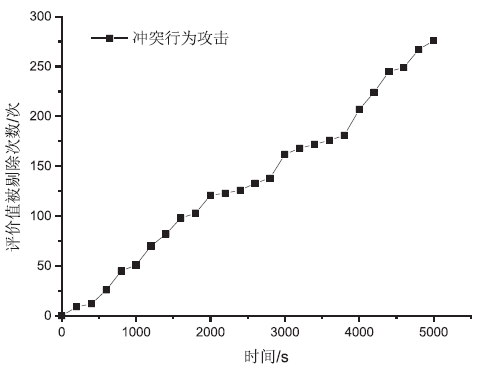
| [1] |
GOVINDAN K,MOHAPATRA P.Trust Computations and Trust Dynamics in Mobile Adhoc Networks: A Survey[J]. IEEE Communications Surveys and Tutorials, 2012,14(2): 279-298 .
|
| [2] |
PROBST M J,KASERA S K.Statistical Trust Establishment in Wireless Sensor Networks[C]//IEEE.2007 International Conference on Parallel and Distributed Systems, December 5-7, 2007, Hsinchu, China.NJ:IEEE,2007:1-8.
|
| [3] |
JIANG Tao, BARAS J S.Trust Evaluation in Anarchy: A Case Study on Autonomous Networks[C]// INFOCOM. IEEE International Conference on Computer Communications, April 23-29,2006, Barcelona, Catalunya, Spain. NJ:IEEE, 2006:1-12.
|
| [4] |
PENG Jia, GAO Neng.Research on Identity Trusted Level Evaluation Mechanism Based on User Behavior Analysis[J].Netinfo Security,2016,16(9):124-129.
|
|
彭佳,高能. 基于实体行为的身份可信等级评估机制研究[J]. 信息网络安全,2016,16(9):124-129.
|
| [5] |
SHABUT A M, DAHAL K P, BISTA S K, et al.Recommendation-based Trust Model with an Effective Defence Scheme for MANETs[J].IEEE Transactions on Mobile Computing,2015,14(10):2101-2115.
|
| [6] |
SHEN Haiying, LI Ze.A Hierarchical Account-aided Reputation Management System for MANETs[J].IEEE/ACM Transactions on Networking,2015, 23(1):70-84.
|
| [7] |
YIN Bao,JIANG Liying, WANG Chao.The Design of Trusted Secure Routing of Quantum Ant Colony Algorithm for Large Scale Wireless Sensor Networks[J].Netinfo Security,2015,15(3):14-18.
|
|
尹宝,姜丽莹,王潮. 量子蚁群算法的大规模无线传感网可信安全路由设计[J].信息网络安全,2015,15(3):14-18.
|
| [8] |
JIANG Shouxu, LI Jianzhong.A Reputation-based Trust Mechanism for P2P E-commerce Systems[J].Journal of Software, 2007,18(10):2551-2563
|
|
姜守旭, 李建中. 一种P2P电子商务系统中基于声誉的信任机制[J]. 软件学报, 2007, 18(10):2551-2563.
|
| [9] |
LI Wenjia, SONG Houbing.ART: An Attack-resistant Trust Management Scheme for Securing Vehicular Ad Hoc Networks[J].IEEE Transactions on Intelligent Transportation Systems, 2016,17(4):960-969.
|
| [10] |
TAN Shuaishuai, LI Xiaoping, DONG Qingkuan.A Trust Management System for Securing Data Plane of Ad-Hoc Networks[J].IEEE Transactions on Vehicular Technology, 2016, 65(9):7579-7592.
|
| [11] |
HUANG Qiang, WANG Gaojian, MI Wenzhi, et al.Centralized and Unified Trusted Computing Platform Management Model and Its Application[J].Netinfo Security, 2017,17(4):9-14.
|
|
黄强, 王高剑, 米文智,等. 集中统一的可信计算平台管理模型研究及其应用[J]. 信息网络安全, 2017,17(4):9-14.
|
| [12] |
MARTI S, GIULI T J, LAI K, et al.Mitigating Routing Misbehavior in Mobile Ad Hoc Networks[C]//ACM. The 6th Snnual International Conference on Mobile Computing and Networking, August 6 - 11, 2000 , Boston, Massachusetts, USA. New York: ACM, 2000:255-265.
|
| [13] |
DETTI A, BLEFARI-MELAZZI N.Overlay, Borůvka-based, Ad-hoc Multicast Protocol: Description and Performance Analysis[J]. Wireless Communications & Mobile Computing, 2008, 8(10):1313-1329.
|
| [14] |
LEE S J, GERLA M, TOH C.On Demand Multicast Routing Protocol (ODMRP) for Ad Hoc Networks[J]. Lecture Notes in Mathematics, 2003, 3:1298-1302.
|
| [15] |
HABEL J M. A Língua Nas Artes e a Arte de Falar Línguas Minoritárias: Ações de Popularização da Ciência No Projeto ALMA-H[EB/OL]. ,2018-3-15.
|
| [16] |
XIE J,TALPADE R R,MCAULEY A J, et al. AMRoute: Ad Hoc Multicast Routing Protocol[EB/OL]. , 2018-3-15.
|
| [17] |
TIETJEN G L, MOORE R H.Some Grubbs-type Statistics for the Detection of Several Outliers[J]. Technometrics, 1972, 14(3):583-597.
|
| [18] |
WILENSKY U. Netlogo,1999[EB/OL].,2018-3-15.
|
 ), Hui XIA
), Hui XIA