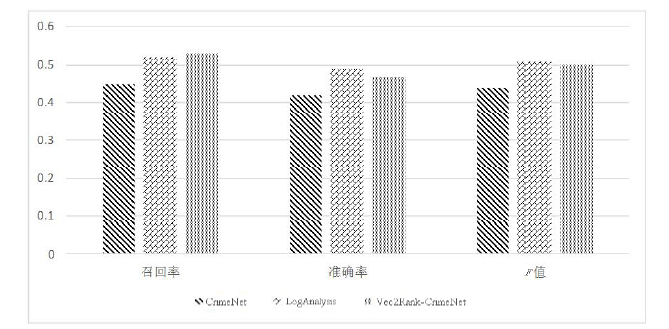
| [1] |
HUANG Liwei, LI Deyi, MA Yutao, et al.A Meta Path-based Link Prediction Model for Heterogeneous Information Networks[J]. Chinese Journal of Computers,2014(4):848-858.
|
|
黄立威, 李德毅, 马于涛,等. 一种基于元路径的异质信息网络链路预测模型[J]. 计算机学报, 2014(4):848-858.
|
| [2] |
WU Xindong, LI Yadong, HU Donghui.Study on Social Network Forensics[J]. Journal of Software, 2014(12): 2877-2892.
|
|
吴信东, 李亚东, 胡东辉. 社交网络取证初探[J]. 软件学报, 2014(12):2877-2892.
|
| [3] |
SARVARI H, ABOZINADAH E, MBAZIIRA A, et al.Constructing and Analyzing Criminal Networks[C]// IEEE. 2014 IEEE Security and Privacy Workshops, May 17-18, 2014, San Jose, CA, USA.NJ: IEEE, 2014:84-91.
|
| [4] |
HARTIGAN J A, WONG M A.Algorithm AS 136: A K-Means Clustering Algorithm[J]. Journal of the Royal Statistical Society, 1979, 28(1):100-108.
|
| [5] |
AGGARWAL C C, XIE Yan, Yu P S. Towards Community Detection in Locally Heterogeneous Networks[EB/OL]..
|
| [6] |
TAHA K, YOO P D.SIIMCO: A Forensic Investigation Tool for Identifying the Influential Members of a Criminal Organization[J]. IEEE Transactions on Information Forensics & Security, 2016, 11(4):811-822.
|
| [7] |
ABADI M, AGARWAL A, BARHAM P, et al. TensorFlow: Large-Scale Machine Learning on Heterogeneous Distributed Systems[EB/OL]. .
|
| [8] |
DUAN Dagao, XIE Yongheng, GAI Xinxin, et al.A Rumor Detection Model Based on Neural Network[J].Netinfo Security, 2017,17(9):134-137.
|
|
段大高, 谢永恒, 盖新新,等. 基于神经网络的微博虚假消息识别模型[J]. 信息网络安全, 2017,17(9):134-137.
|
| [9] |
GOLDBERG Y, LEVY O. Word2vec Explained: Deriving Mikolov et al.'s Negative-sampling Word-embedding Method[EB/OL]. .
|
| [10] |
GROVER A, LESKOVEC J.Node2vec:Scalable Feature Learning for Networks[C]// ACM. The 22nd ACM Sigkdd International Conference on Knowledge Discovery & Data Mining, August 13 - 17, 2016 , San Francisco, California, USA .New York: ACM, 2016:855-864.
|
| [11] |
LIU Hao, CHEN Zhigang, ZHANG Lianming.A Task-based Access Control Model of Peer-to -Peer Network Based on Admission Degree[J].Netinfo Security, 2017,17(6):22-29.
|
|
刘浩, 陈志刚, 张连明. P2P网络中基于准入度的任务访问控制模型[J]. 信息网络安全, 2017,17(6):22-29.
|
| [12] |
CATANESE S, FERRARA E, FIUMARA G. LogAnalysis: A Tool to Study Communities inside Social Networks[EB/OL]. .
|
| [13] |
WANG Heyong, CHANG C K, YANG H L, et al.Estimating the Relative Importance of Nodes in Social Networks (Preprint)[J]. Journal of Information Processing, 2013, 21(3):414-422.
|
| [14] |
HU Yangrui, CHEN Xingshu, WANG Junfeng, et al.Anomalous Traffic Detection Based on Traffic Behavior Characteristics[J]. Netinfo Security, 2016,16(11):45-51.
|
|
胡洋瑞, 陈兴蜀, 王俊峰,等. 基于流量行为特征的异常流量检测[J]. 信息网络安全, 2016,16(11):45-51.
|
| [15] |
GUO Xiaohe, LIU Ke, LIAO Huanwen.Enron Executives Organization Structure's Found Based on Complex Network[J].Journal of Nanchang Hangkong University, 2013, 27(3):103-108.
|
|
郭小和, 刘科, 廖焕文,等. 基于复杂网络的安然公司高管组织结构发现[J]. 南昌航空大学学报, 2013, 27(3):103-108.
|
| [16] |
FERRARA E, MEO P D, CATANESE S, et al.Detecting Criminal Organizations in Mobile Phone Networks[J]. Expert Systems with Applications, 2014, 41(13):5733-5750.
|
| [17] |
XU J J, CHEN H.CrimeNet Explorer: a Framework for Criminal Network Knowledge Discovery[J]. ACM Transactions on Information Systems, 2005, 23(2):201-226.
|
| [18] |
NEWMAN M E. Fast Algorithm for Detecting Community Structure in Networks[EB/OL]. .
|
| [19] |
GIRVAN M, NEWMAN M E J. Community Structure in Social and Biological Networks[J].Proceedings of the National Academy of Sciences of the United States of America,2002(12):7821-7826.
|