Netinfo Security ›› 2017, Vol. 17 ›› Issue (3): 33-38.doi: 10.3969/j.issn.1671-1122.2017.03.006
• Orginal Article • Previous Articles Next Articles
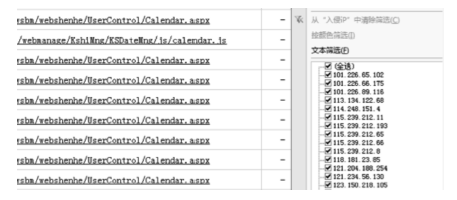
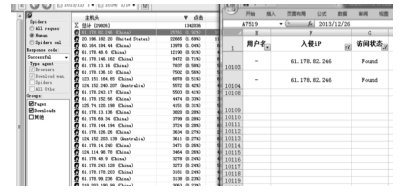
Research on Comprehensive Forensic Analysis Based on Logs2intrusions and Web Log Explorer
Jing YANG( ), Xin ZHAO, Tianliang LU
), Xin ZHAO, Tianliang LU
- School of Information Technology and Network Security, People’s Public Security University of China, Beijing 102600, China